A collaborative control method for array honeypots based on blockchain
A collaborative control and blockchain technology, applied in the field of network security, can solve problems such as the loss of the defender and the paralysis of the array honeypot system, and achieve the effect of resisting attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the purpose, technology and advantages of the present invention clearer, the present invention will be further described in detail and completely below in conjunction with the accompanying drawings.
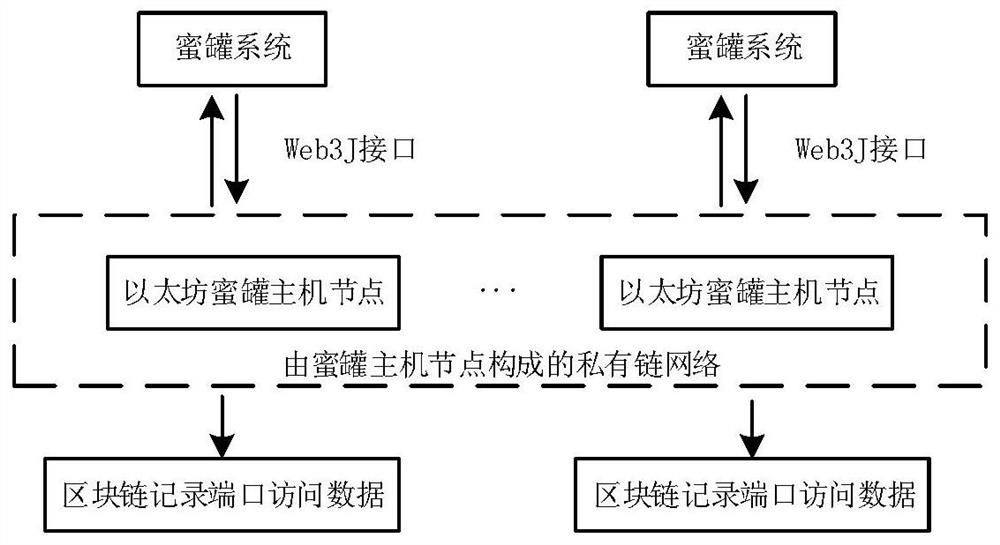
[0023] Step (1): Under the Ethereum platform, use the genesis block file to build a private chain consisting of n hosts in the honeypot inside the array, that is, priChain={host 0 ,host 2 ,...,host n-1}.
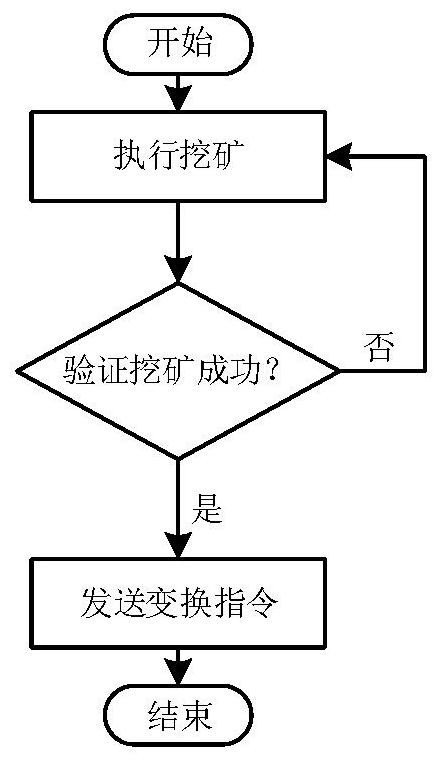
[0024] In the step (1), using the genesis file to build a private chain requires data adjustment to the JSON type file, that is, modifying the internal difficulty (difficulty value) parameter. By adjusting the difficulty value, the mining time interval T is within a reasonable range, so that the change cycle of the internal service host of the array honeypot system is at the best defense stage.
[0025] Step (2): In n host computers, build a distributed dynamic array honeypot system with active defense function, i.e. honArray={sys 0 ,sys 2 ,...,sys ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com