Binary vulnerability code cloning detection method and system
A binary code and detection method technology, applied in the field of computer program detection, can solve problems such as high complexity, low accuracy, incomplete clone type detection, etc., to ensure comprehensiveness, universal applicability, and solve clone type detection incomplete effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
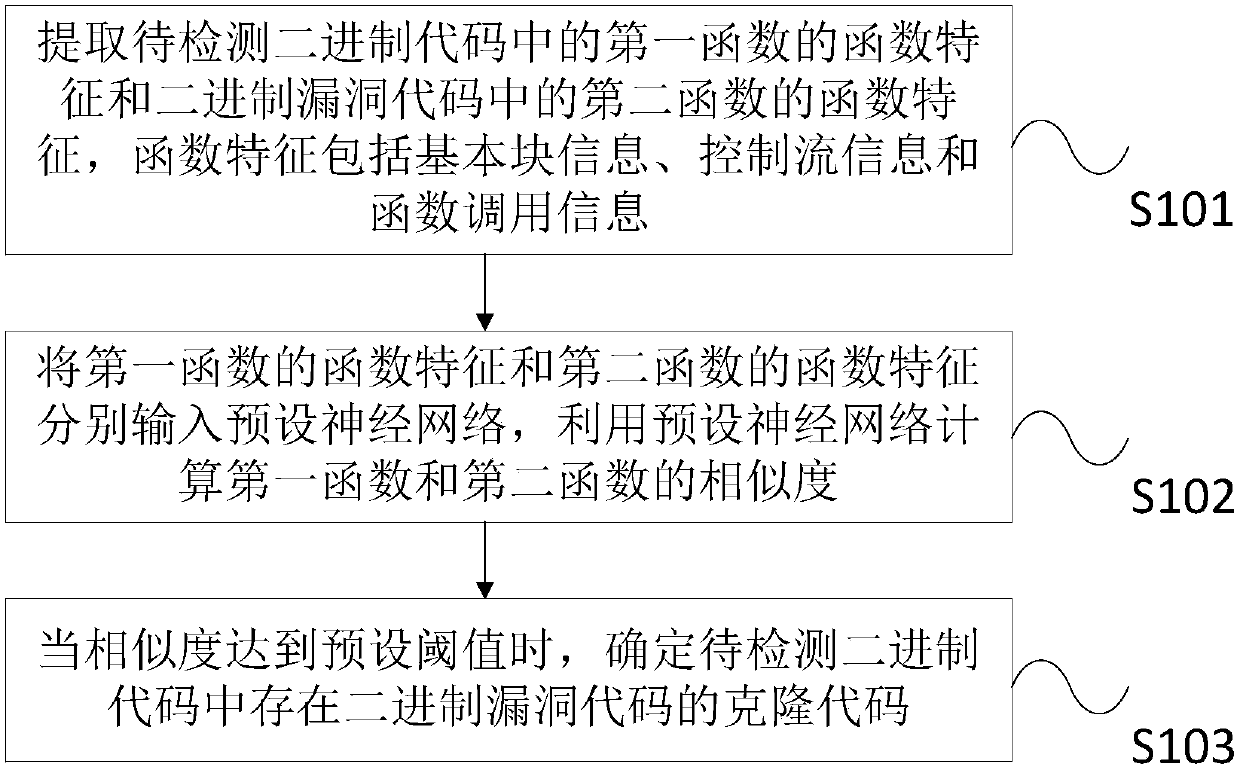
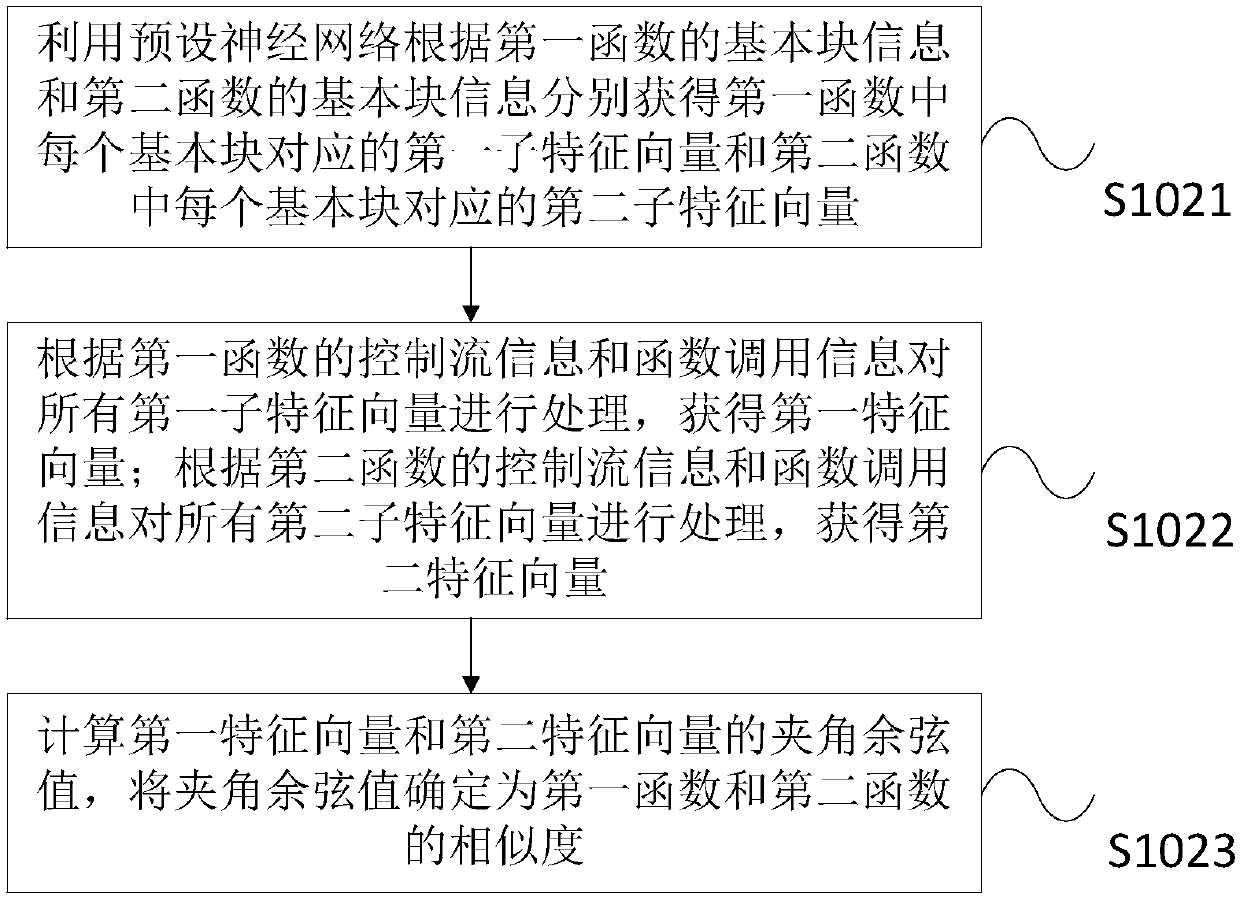
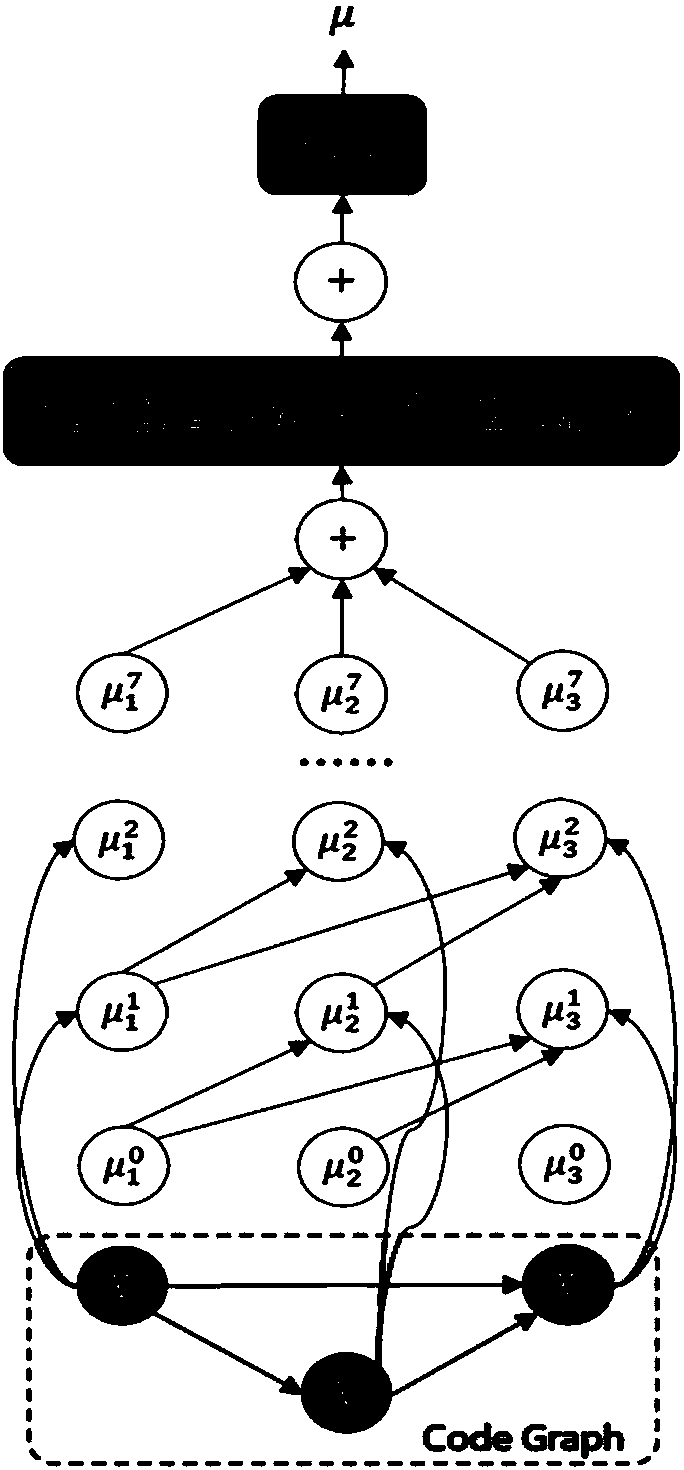
[0048] It should be noted that most of the existing research on clone code analysis technology is based on source code, and less research is based on binary code. But in some cases, we cannot get the source code, such as most commercial software will not release the source code, then it is particularly important to use binary files for similarity detection. In view of this, the present invention provides a binary vulnerability code clone detection method, comprising: extracting the function characteristics of the first function in the binary code to be detected and the function characteristics of the second function in the binary vulnerability code, the function characteri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com