Network attack target identification method and network attack target identification system based on attack graph
A network attack and target recognition technology, which is applied in the attack graph-based network attack target recognition method and system field, can solve the problems of low probability of attack intention realization and difficulty in accurately reflecting behavior intention, and achieve simple and convenient operation and low computational complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions. The technical term involved in the embodiment is as follows:
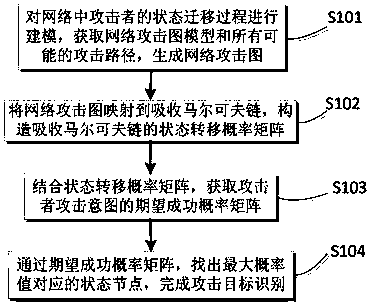
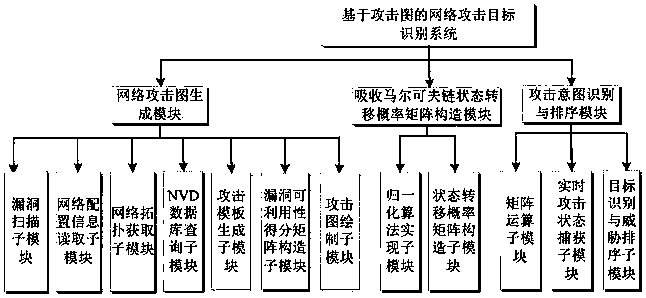
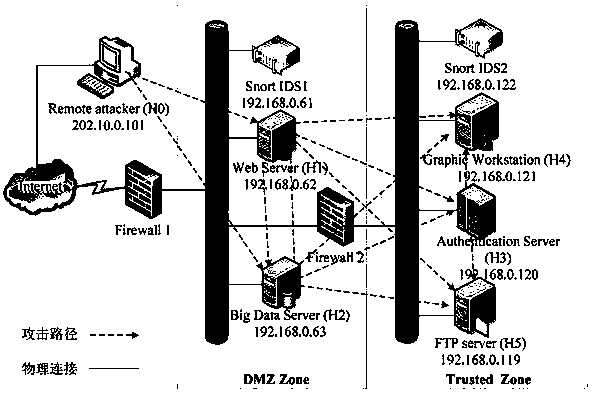
[0043] In the practical application of network security, because the attacker is not familiar with the network structure, the attacker often chooses the most likely attack target as the intrusion intention, and there may be repeated state transition behaviors in the actual attack scenario, resulting in a directed and circular attack graph , resulting in the realization probability of the attack intention in the ideal scenario is often smaller than the actual value, it is difficult to accurately reflect the behavior intention of the attacker in the real world, and the accuracy and effectiveness of the intention assessment cannot be ensured. In view of this, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com