Method and system for secure access to vehicle-mounted controller
A vehicle-mounted controller and security access technology, which is applied in the security access method and system field of the vehicle-mounted controller, can solve problems affecting driving safety, intruding into the vehicle-mounted controller, threatening the security performance of the vehicle-mounted controller, etc., and achieve the goal of maintaining normal performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
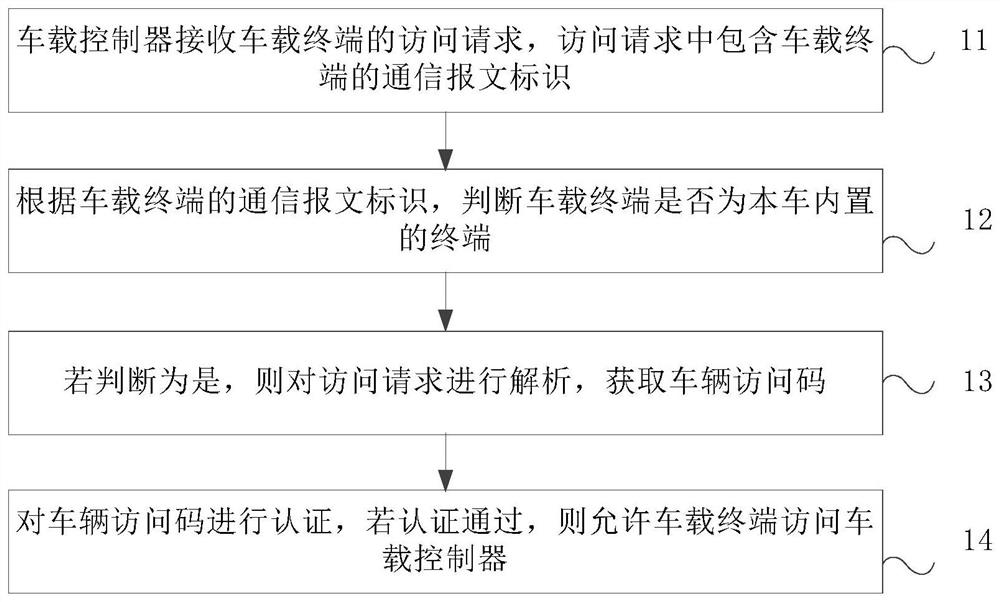
[0056] figure 1 It is a schematic flowchart of a method for securely accessing a vehicle-mounted controller provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method includes the following steps:
[0057] Step 11, the vehicle-mounted controller receives the access request of the vehicle-mounted terminal, and the access request includes the communication message identification of the vehicle-mounted terminal;
[0058] When the vehicle leaves the factory, the built-in terminal of the vehicle must be assigned a communication message identification of the vehicle terminal, for example, the communication message identification of the engine controller is 0x10, and the communication message identification of the window controller is 0x20. When the vehicle-mounted terminal sending the access request is a built-in terminal in the vehicle, the access request will include the communication message identification of the vehicle terminal.
[0059] Step 12...
Embodiment 2
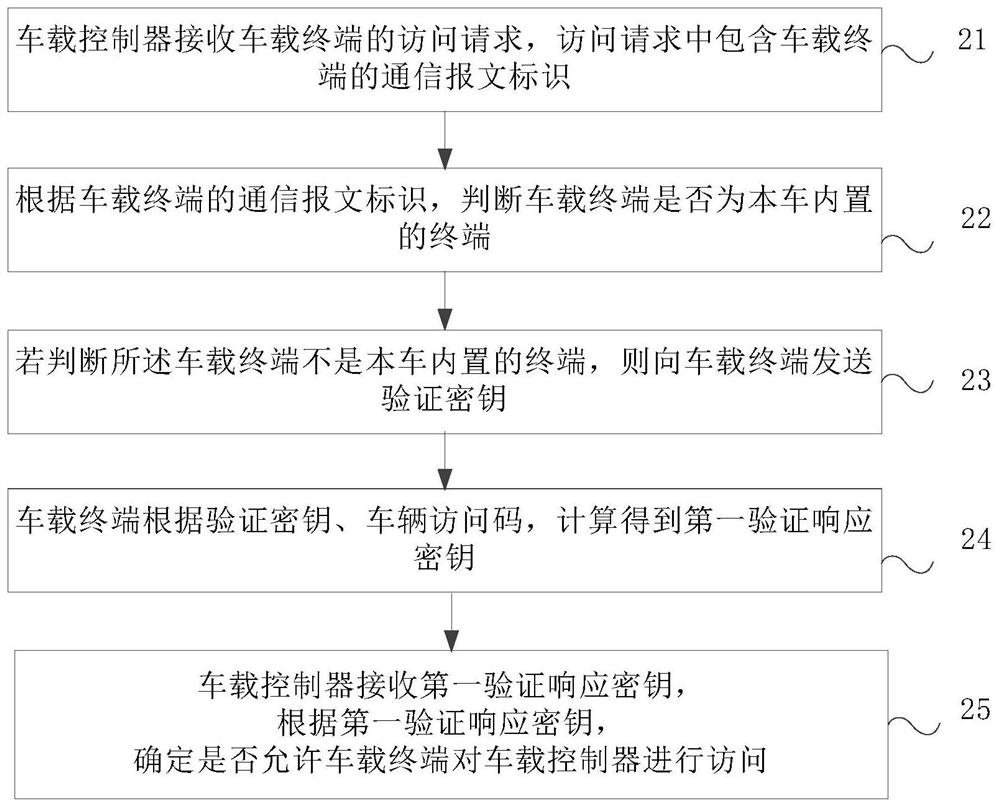
[0067] figure 2 It is a schematic flowchart of a method for securely accessing a vehicle-mounted controller provided by Embodiment 2 of the present invention. Such as figure 2 Shown, after 12, described method comprises the steps:
[0068] Step 21, the vehicle-mounted controller receives the access request of the vehicle-mounted terminal, and the access request includes the communication message identification of the vehicle-mounted terminal;
[0069] When the vehicle leaves the factory, the built-in terminal of the vehicle must be assigned a communication message identification of the vehicle terminal, for example, the communication message identification of the engine controller is 0x10, and the communication message identification of the window controller is 0x20. When the vehicle-mounted terminal sending the access request is a built-in terminal in the vehicle, the access request will include the communication message identification of the vehicle terminal.
[0070] S...
Embodiment 3
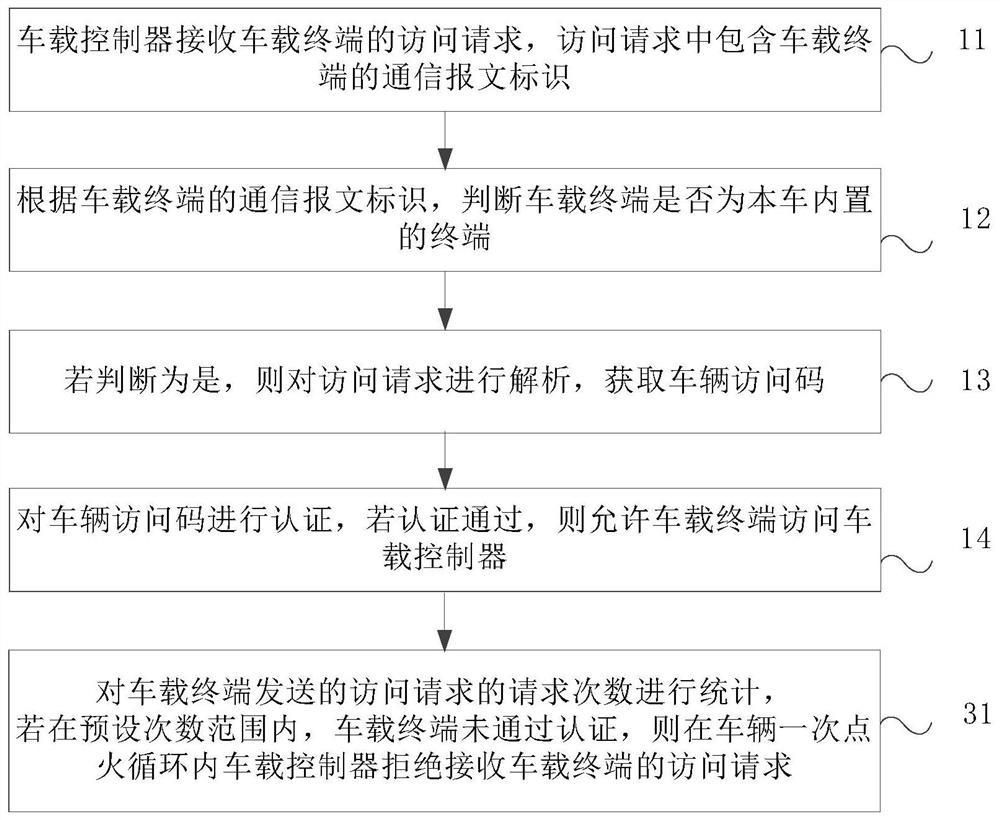
[0087] image 3 It is a schematic flowchart of a secure access method for an on-board controller provided by Embodiment 3 of the present invention. Such as image 3 As shown, the method also includes:
[0088] 31. Count the number of access requests sent by the vehicle-mounted terminal. If the vehicle-mounted terminal fails to pass the authentication within the preset number of times, the vehicle-mounted controller refuses to receive the access request from the vehicle-mounted terminal within one ignition cycle of the vehicle.
[0089]The on-board controller counts the number of access requests while verifying the legitimacy of the access request. In order to avoid misjudgment in the identification of the vehicle access code by the on-board controller, the preset number of requests depends on the allowable range. If within the preset number of times, the vehicle access codes contained in the multiple access requests sent by the vehicle-mounted terminal fail to pass the authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com