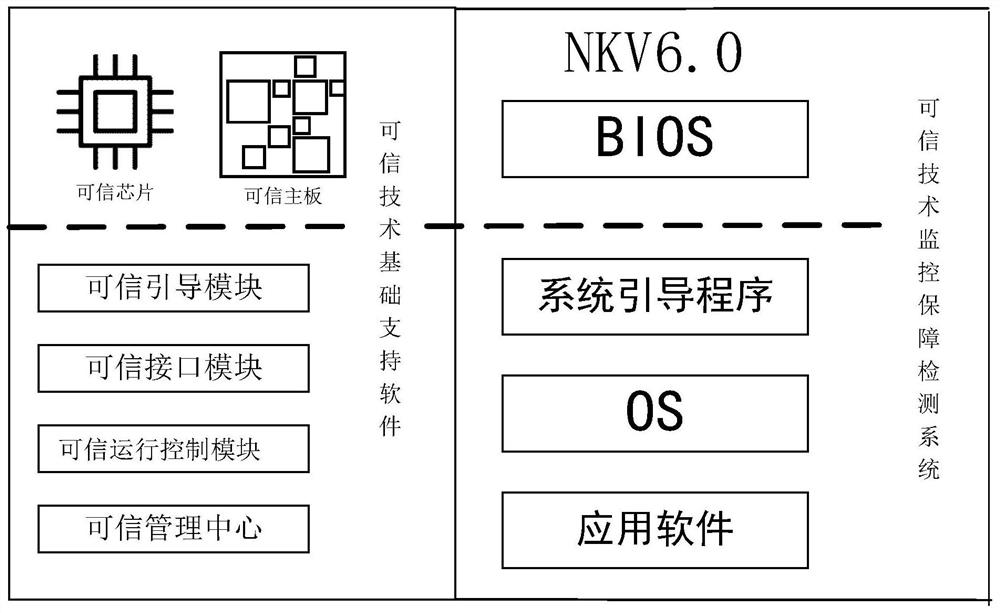
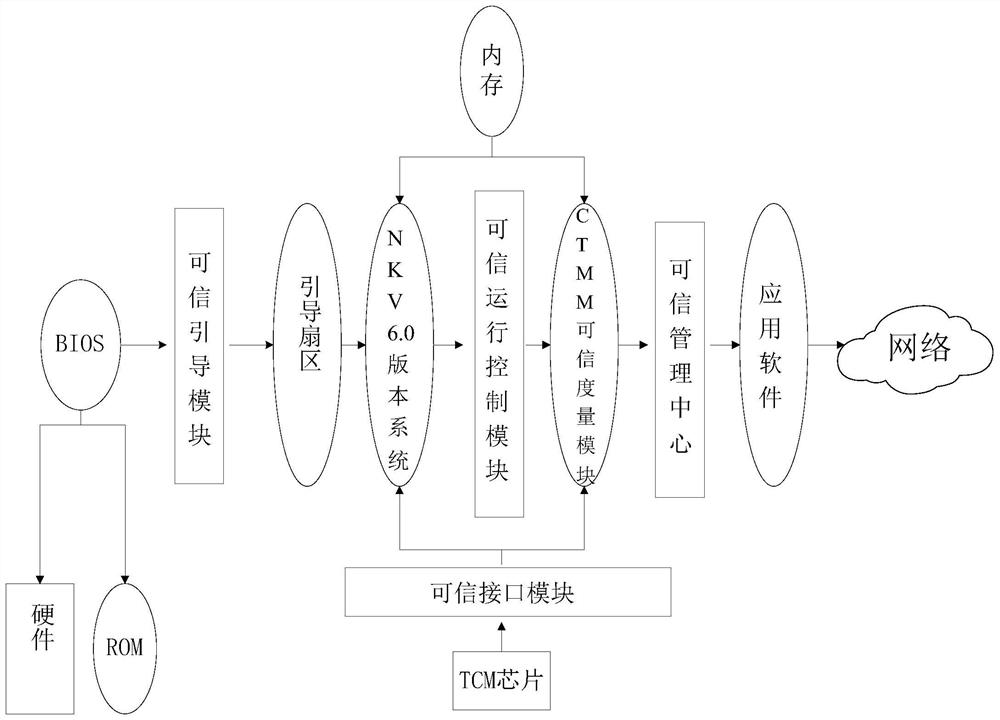
A Trusted Technology Compatibility Testing Method Based on nkv6.0 System
A compatibility test and compatibility technology, applied in the computer field, can solve problems such as inability to execute, affect software performance, and different operating results, and achieve the effect of ensuring safety and quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0128] Embodiment 1: Trusted operation control checks file integrity protection compatibility
[0129] 1. Test description
[0130] Verify CTMM's integrity measurement of kernel modules and executable files loaded during operation, and compare the measurement results with the baseline value of the whitelist. If the verification fails, the loading of the module or the execution of the application is rejected.
[0131] 2. Preconditions
[0132] (1) The machine under test has a TCM chip, and the NKV6.0 system has been installed;
[0133] (2) ctmm is on;
[0134] (3) The executable program ntsysv exists under / usr / sbin and is in the whitelist.
[0135] 3. Operation steps
[0136] Step 1: The secadm user logs in to the NKV6.0 system and enters the Trusted Management Center: Click "Start" - "System Tools" - "Security Control Management Center" in sequence - double-click to enter the Trusted Management Center;
[0137] Step 2: Set the executable file to strict mode: click "Setti...
Embodiment 2
[0151] Example 2: Trusted Management Center adds a whitelist test
[0152] 1. Test description
[0153] Verify that the system can be scanned in the Trusted Management Center and the scanned files can be added to the whitelist.
[0154] 2. Test premise
[0155] (1) The machine under test has a TCM chip, and the NKV6.0 system has been installed;
[0156] (2) There is a test script file test3 in the " / tmp / lvl4" directory, and this file does not exist in the whitelist;
[0157] (3) ctmm status is on and standard / normal scripts are set to loose mode.
[0158] 3. Operation steps
[0159] Step 1: Run the test script file test3 and execute the command:
[0160][secadm@locahost~]$cd / tmp / lvl4
[0161] [secadm@locahost~]$. / test3
[0162] Step 2: After editing the contents of the script file test3, run again:
[0163] [secadm@locahost~]$ vim test3
[0164] [secadm@locahost~]$. / test3
[0165] Step 3: The secadm user logs in to the NKV6.0 system and opens the "Trusted Management...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com