Device and method for identifying malicious code
A malicious code and identification device technology, which is applied in the field of malicious code identification devices, can solve the problems of not being able to identify unknown malicious codes, malicious code reinforcement, etc., and achieve the effect of improving accuracy and effect and preventing threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described below in conjunction with specific examples and accompanying drawings.
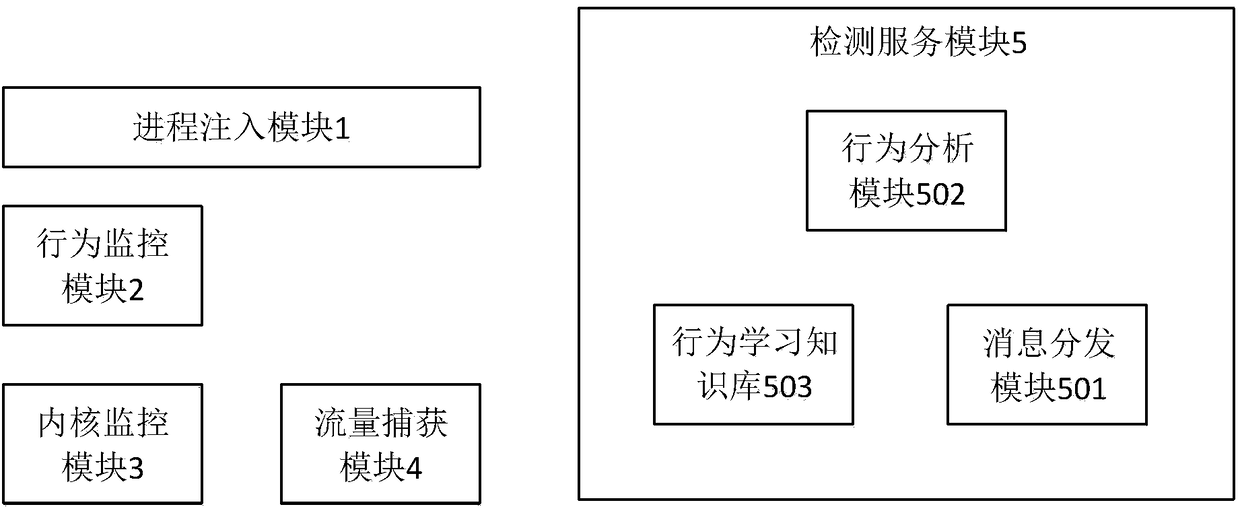
[0047] The present invention provides a malicious code identification device, such as figure 1 As shown, it includes:
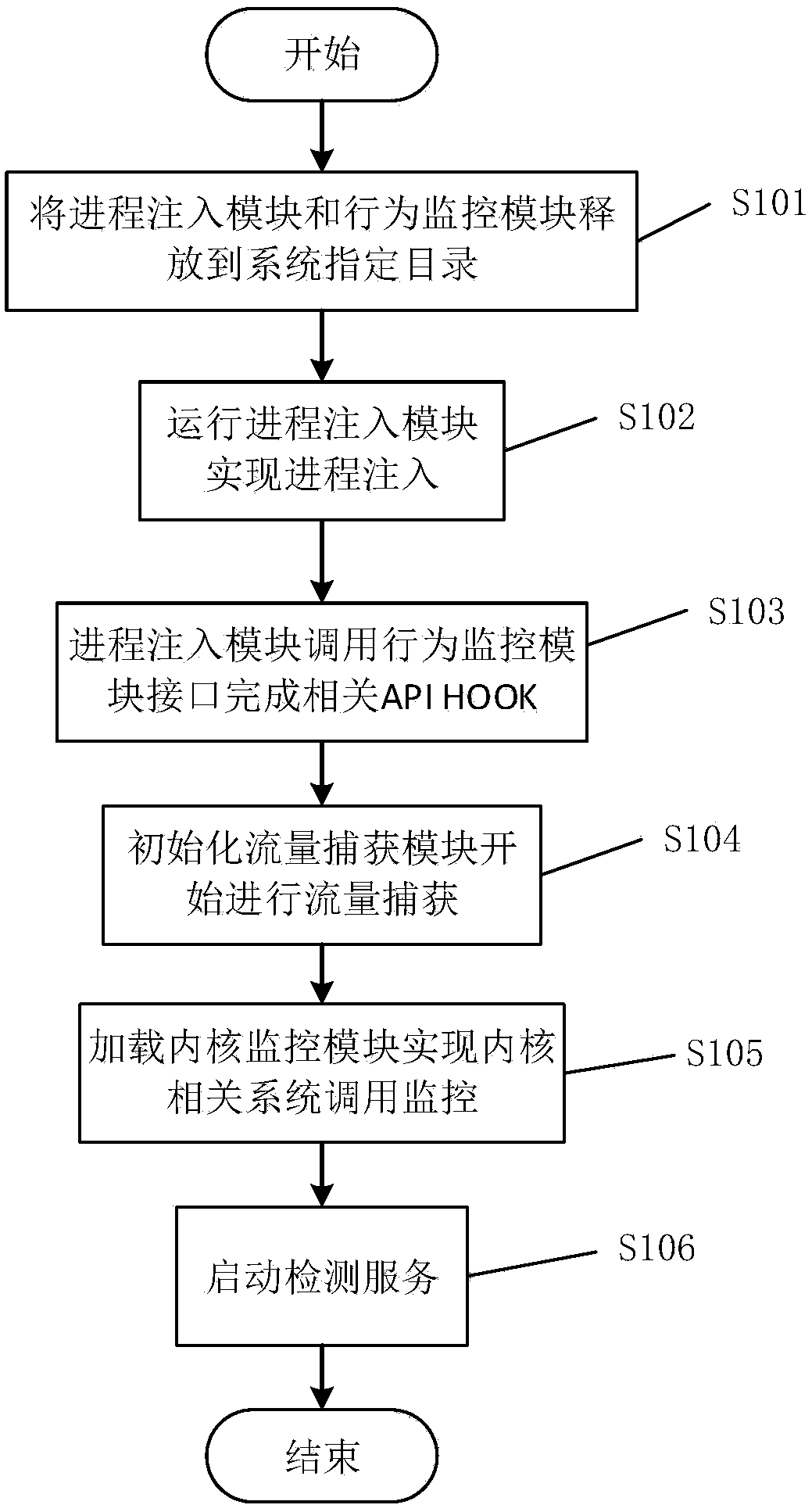
[0048] The process injection module 1 is used to inject the system process at run time and load the API HOOK dynamic library during the running process of the terminal equipped with the Android system, so as to achieve the purpose of monitoring other application process APIs in the system. Specifically, perform ptrace on zygote and system_server, and load the API HOOK dynamic library through dlopen.
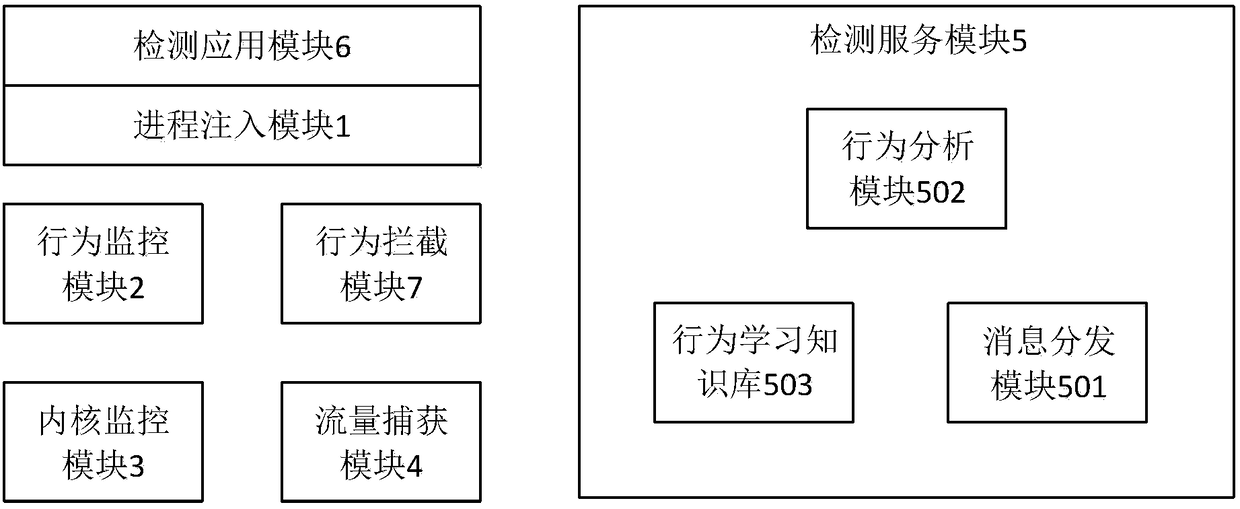
[0049] The monitoring module is used to monitor sensitive APIs through API HOOK and send behavior monitoring vectors. Among them, the sensitive API is a preset list of a series of Android APIs that may have threatening behaviors based on human experience. The monitoring module includes: behavior monitoring module 2, which is used to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com