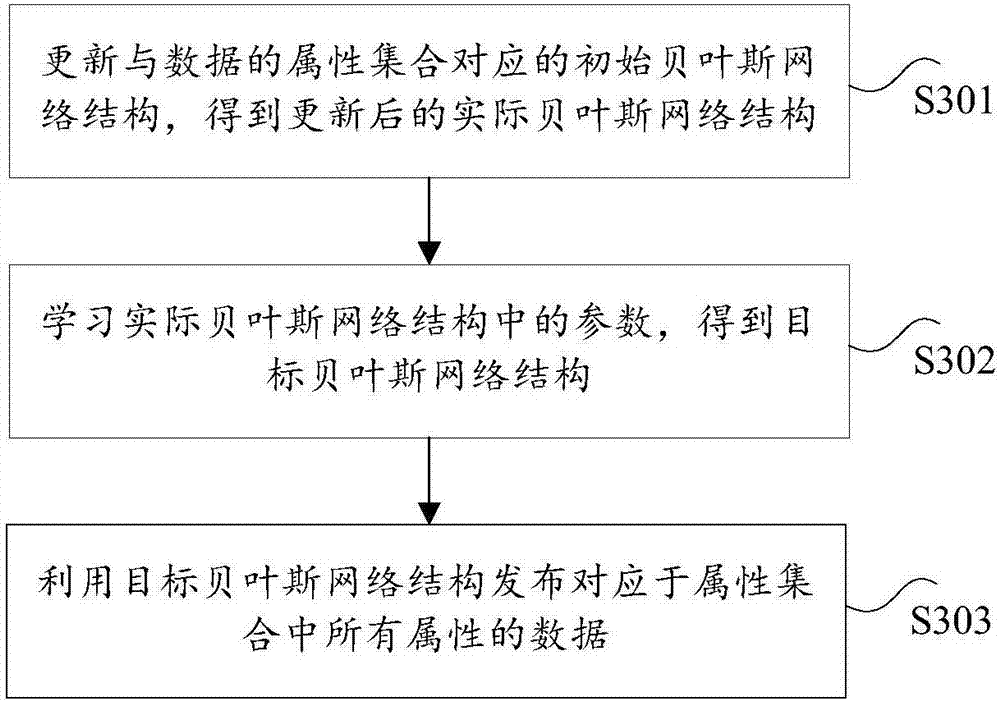
Data releasing method and device and terminal
A data release and data technology, applied in the field of data security, can solve problems such as low security and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device (ie, a terminal). Take running on a computer terminal as an example, such as figure 1 As shown, the computer terminal may include one or more (only one is shown in the figure) processors 101 (the processors 101 may include but not limited to processing devices such as microprocessor MCU or programmable logic device FPGA, etc.), for storing Data storage 103, and transmission means 105 for communication functions. Those of ordinary skill in the art can understand that, figure 1 The shown structure is only for illustration, and it does not limit the structure of the above-mentioned electronic device.
[0048] The memory 103 can be used to store software programs and modules of application software, such as program instructions / modules corresponding to the control method of the device in the embodiment of the pr...
example 1
[0131] like Figure 5 As shown, taking K hospitals (coded as P 1 ,P 2 ,...,P k , K≥2) joint release of medical data as an example to describe this application in detail.
[0132] The medical data of K hospitals exist on their respective physical hosts, and the semi-trusted third party and each hospital are connected through the Internet. According to the PrivSeq algorithm process, the semi-trusted third party coordinates all parties to release data that meets differential privacy protection (publishing overall medical data).
[0133] In step S501, the semi-trusted third party divides the attribute set A (such as name, gender, age, disease, etc.) using a non-overlapping attribute division method to obtain a set of views. A view is a set containing some attributes, such as view V 1 =(X 11 ,X 12 ,...,X 1i );
[0134] Step S502, each hospital uses its own data to count the marginal distributions of all views in the previous step, and sends the statistical results to a semi...
example 2
[0157] like Figure 6 As shown, taking K stores (numbered as P 1 ,P 2 ,...,P k , K≥2) joint release of the overall purchase record is taken as an example to describe this application in detail.
[0158] The purchase records of K stores exist on their respective physical hosts, the semi-trusted third party and each store are connected through the Internet, and the semi-trusted third party coordinates all parties to complete the data that meets the differential privacy protection according to the PrivSeq algorithm process (the overall purchase record ) to post jobs.
[0159] In step S601, the semi-trusted third party uses a non-overlapping attribute division method to divide the attribute set A (such as attributes including the user's name, gender, age, purchased goods, etc.) to obtain a set of views. The view is a set containing some attributes. as view V 1 =(X 11 ,X 12 ,...,X 1i );
[0160] Step S602, each store uses its own data to count the marginal distributions of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com