Method and device for compiling functions
A compilation method and function technology, applied in the computer field, can solve problems such as the absence of function source codes, achieve the effect of reducing the amount of code and speeding up compilation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
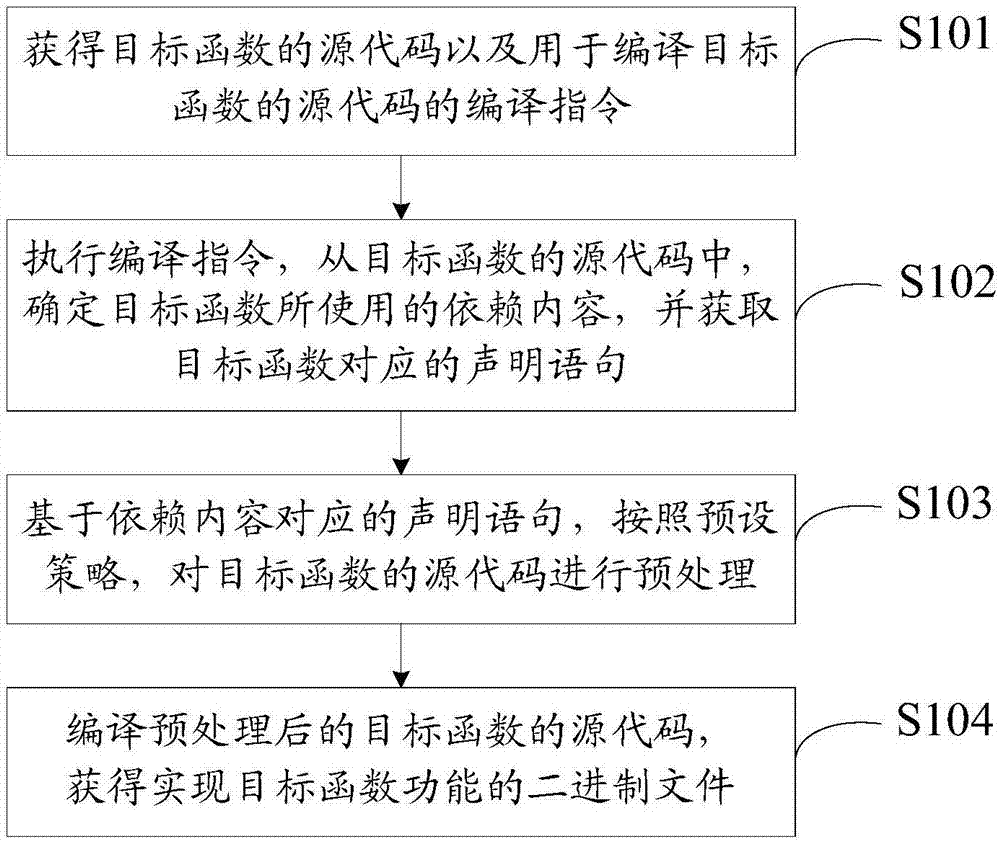
[0022] The embodiment of the present invention provides a function compilation method, which can be applied to a certain target function in the kernel source code using dependent content, such as global variables, macros, inline functions, signed functions, etc., each An occasion where the target function needs to be compiled separately, such as compiling the problem function corresponding to the kernel vulnerability, making a patch for a certain function in the kernel source code, and wanting to replace a certain function in the kernel with an updated function , Want to obtain the binary code file corresponding to the minimum implementation of the objective function, etc.
[0023] In practical applications, a kernel source code contains many functions. For a certain function, it can use some dependent content, such as using global variables, calling other functions, or using macros and inline functions contained in header files. If the kernel code is compiled as a whole, the ...
Embodiment 2
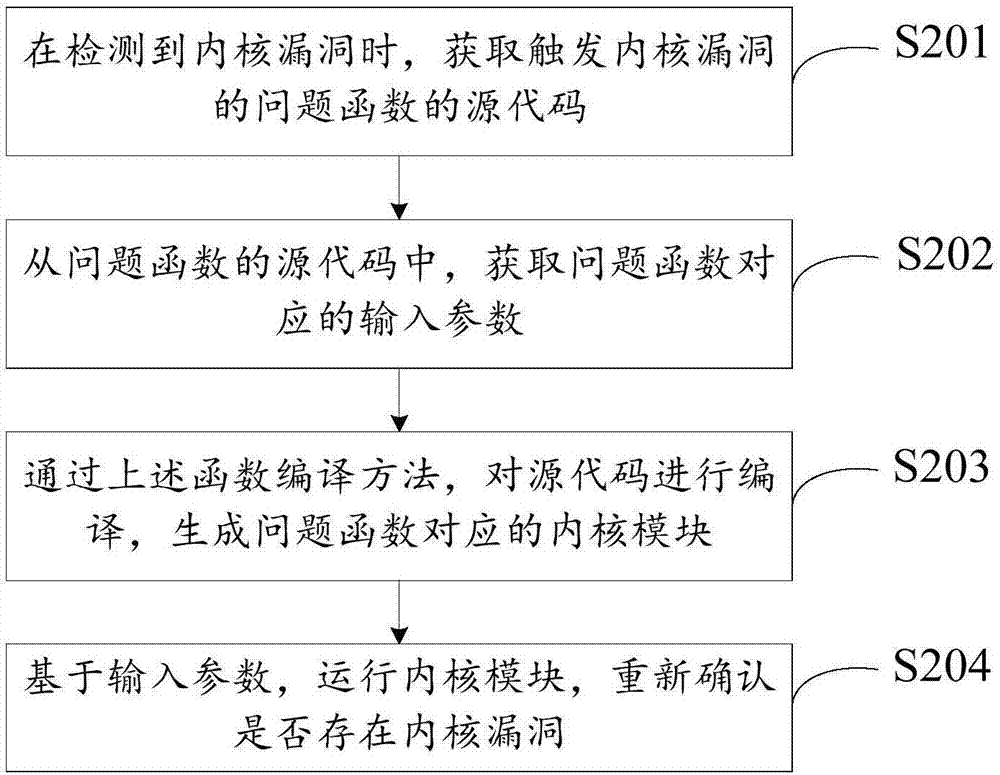
[0071] Based on the same inventive concept, this embodiment provides a vulnerability detection method, which is applied to the following scenario: when a kernel vulnerability occurs, it is necessary to quickly confirm whether the kernel vulnerability exists.
[0072]Generally, during the kernel vulnerability detection process of the kernel, if a kernel vulnerability occurs, corresponding alarm data will be generated, so that the problem function triggering the kernel vulnerability can be determined. Next, in order to confirm whether the kernel vulnerability really exists, the parameters of the system call plus the system call are needed to try to trigger the vulnerability and finally detect whether the kernel has the vulnerability. Specifically, first, you need to find the caller of the problem function, and then find the caller of the caller, so that you search in turn until you return to the user mode system call interface; secondly, you need to construct the defect code that...
Embodiment 3
[0090] Based on the same inventive concept, as an implementation of the above-mentioned function compiling method, the embodiment of the present invention provides a function compiling device. The device embodiment corresponds to the aforementioned method embodiment. Details in the embodiments are described one by one, but it should be clear that the device in this embodiment can correspondingly implement all the content in the foregoing method embodiments.
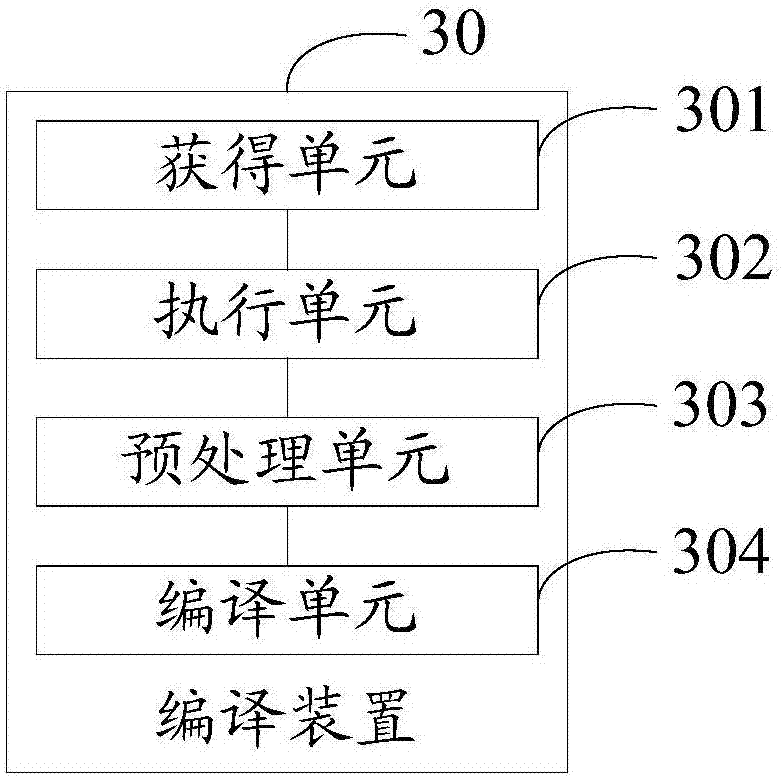
[0091] image 3 It is a schematic structural diagram of the function compiling device in Embodiment 3 of the present invention, see image 3 As shown, the function compiling device 30 includes: an obtaining unit 301, an execution unit 302, a preprocessing unit 303, and a compiling unit 304, wherein the obtaining unit 301 is used to obtain the source code of the target function and to compile the source code of the target function the compilation instruction; the execution unit 302 is used to execute the compilation instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com