A Cryptographic Scrambling Method Based on Nonlinear System
A nonlinear system and cryptography technology, applied in the field of digital image confidentiality, can solve the problems of repeated patterns, time-consuming sorting and searching, insufficient scrambling, etc., to shorten the execution time, omit the search process, and achieve good scrambling effects Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
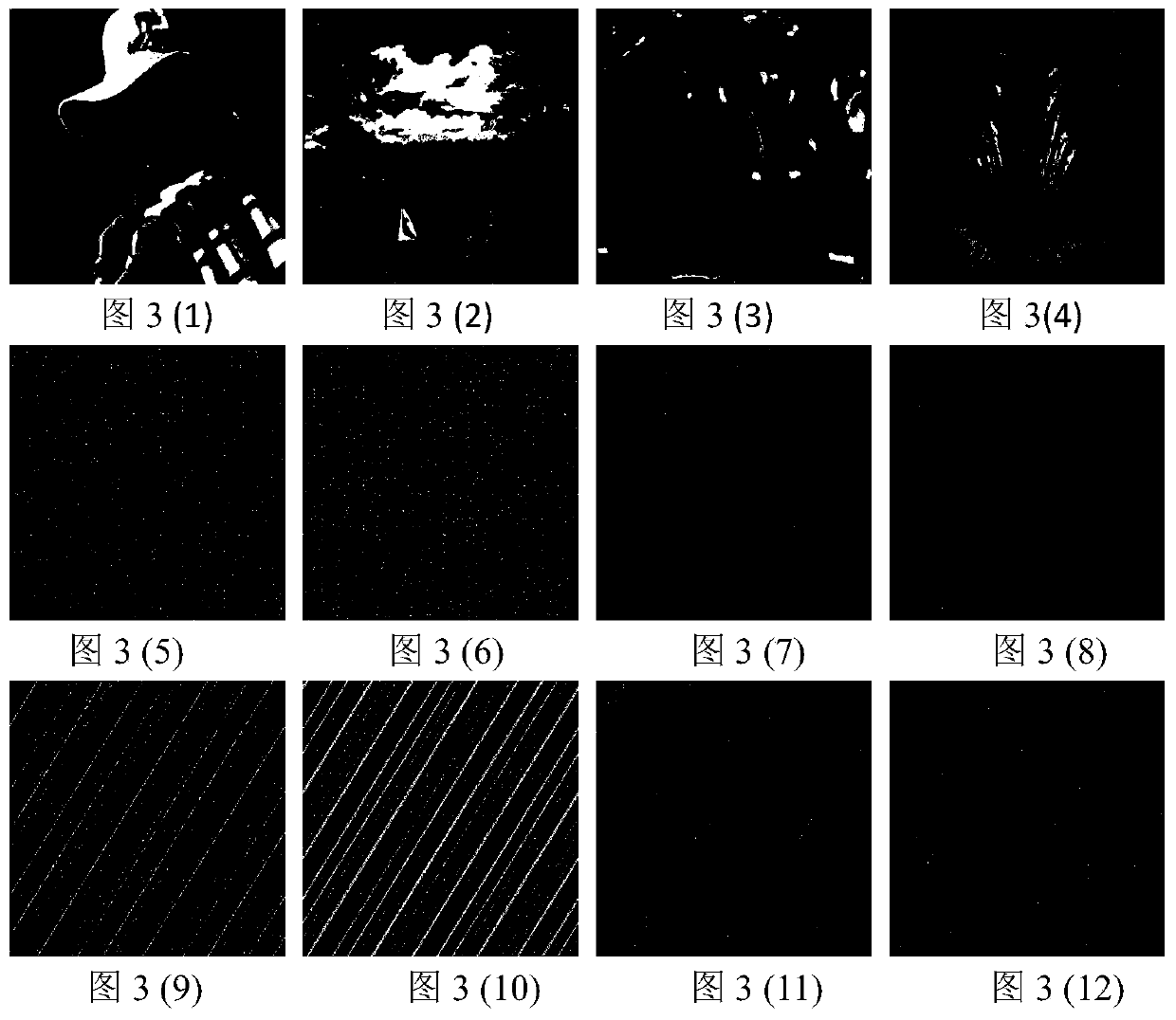
[0021] In order to evaluate the effectiveness of this method, the pictures in TIFF format such as Elaine, Sailboat, Peppers and Mandrill were selected for testing and analysis. The sizes of the above pictures are all 512×512 pixels, among which Elaine is a grayscale image, and Sailboat, Peppers and Mandrill are color images. The random number generation system adopted is the Logistic system (x i+1 =μx i (1-x i )), μ=3.99999, initial value x 0 = 0.25369856. The test environment is CPU: Intel Core i7-6700HQ2.60GHz; RAM: 8.0GB. Test language: C++.
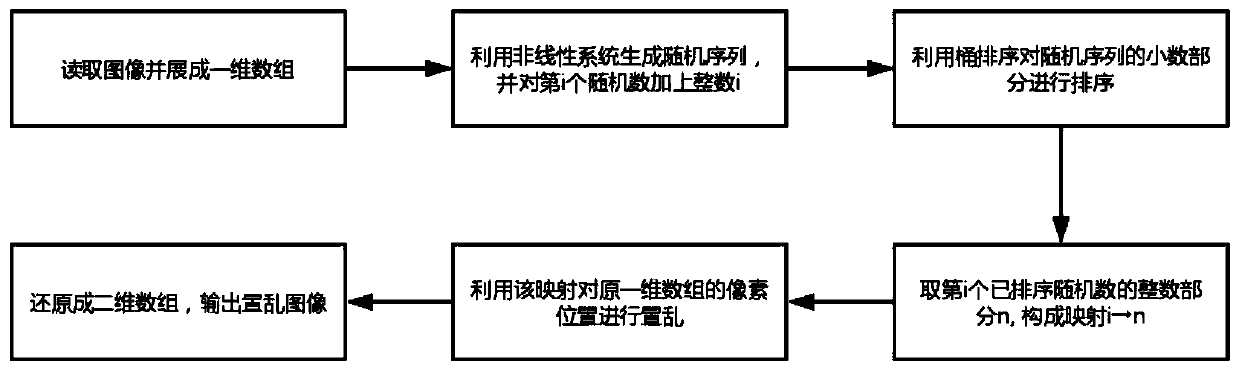
[0022] A pseudo-random sequence is generated through a nonlinear system, and an integer i is added to the i-th random number. The fractional part of the random sequence is sorted by bucket sorting, and the integer part of the sorted sequence obtained is the final position mapping relationship. In this way, the scrambled mapping relationship can be obtained only through one sorting, which saves a lot of running time by eliminati...
Embodiment 2
[0032] Example 2: Taking Lotistic map as an example to illustrate the scrambling efficiency of this method
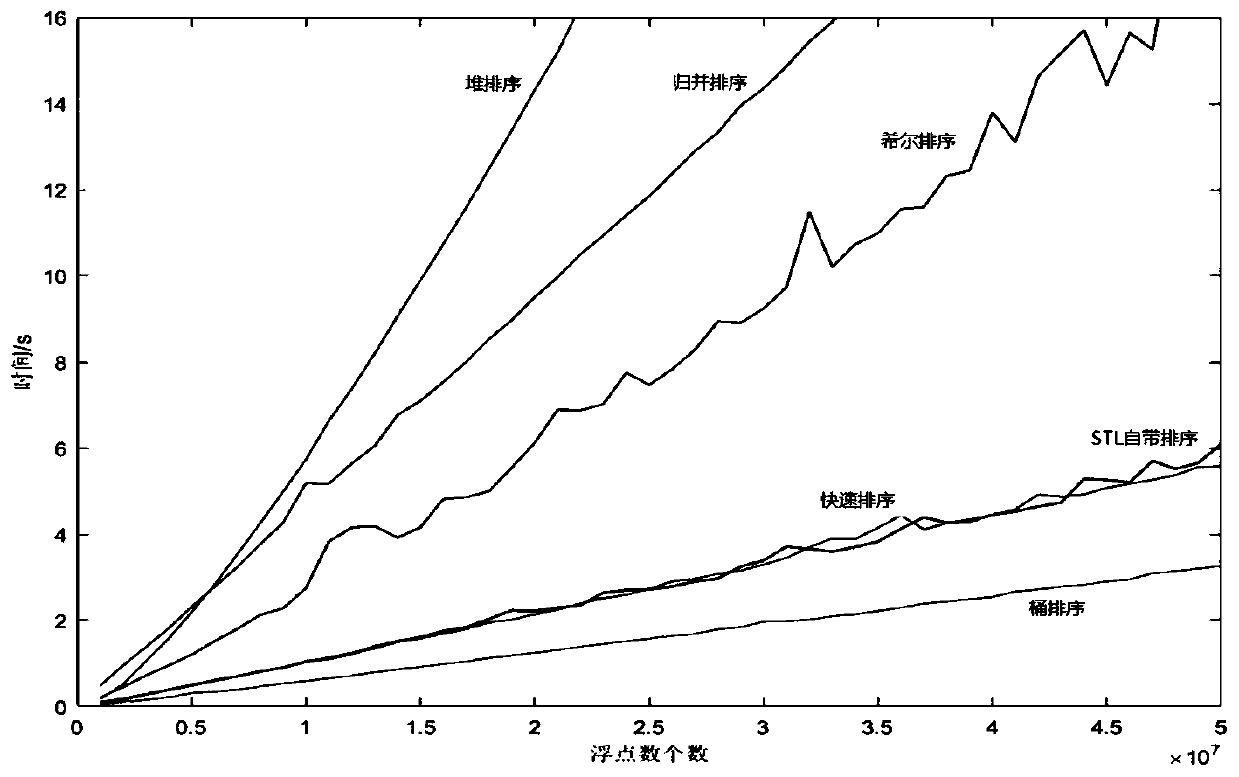
[0033] An important indicator to measure the scrambling algorithm is the scrambling efficiency, that is, the additional time burden due to the scrambling operation. In the traditional sorting-based scrambling algorithm, the time consumption mainly includes four parts: generating random sequences, sorting random sequences, searching each random number generation mapping table, and applying the mapping relationship to the image. In the algorithm of this paper, the completion of sorting means that the generation of the mapping table is completed, so the time consumption mainly has three parts: generating random sequences, sorting random sequences, and applying the mapping relationship to the image.
[0034] In the test, the Logistic mapping equation is used to generate the random sequence. Since the generation of random sequences and position mapping are only related to t...
Embodiment 3
[0042] Example 3: Taking the Logistics map as an example to illustrate the compression rate of this method
[0043] Another measure of encryption algorithms is compression efficiency. A good video encryption algorithm should affect as little as possible the potential compression rate of the image after encoding. In the encryption algorithm described in this paper, only the position of the pixel in the image is changed, but the value of the pixel is not changed. The probability distribution of pixels in the original image is constant, so the scrambling algorithm does not affect the compression rate of the compression algorithm based on the pixel probability model.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com