A wireless multi-hop ad hoc network encryption key dynamic loading device and method
A self-organizing network and wireless self-organizing technology, applied in wireless communication, network topology, security devices, etc., can solve problems such as wireless communication data leakage, and achieve the effect of protecting authentication security, safe and convenient key protection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
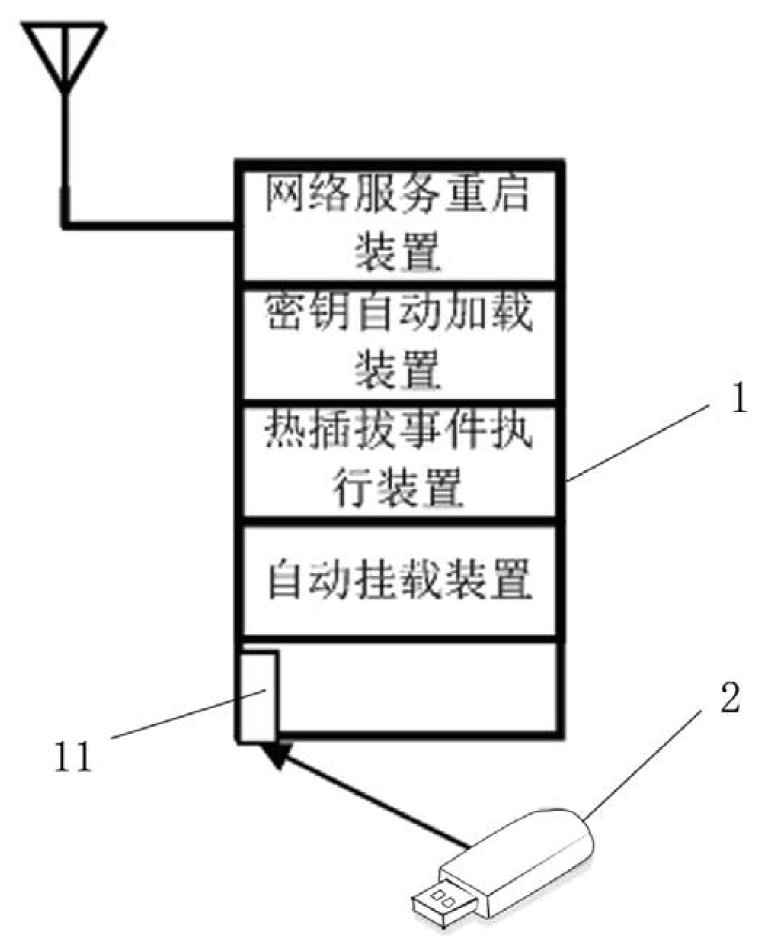
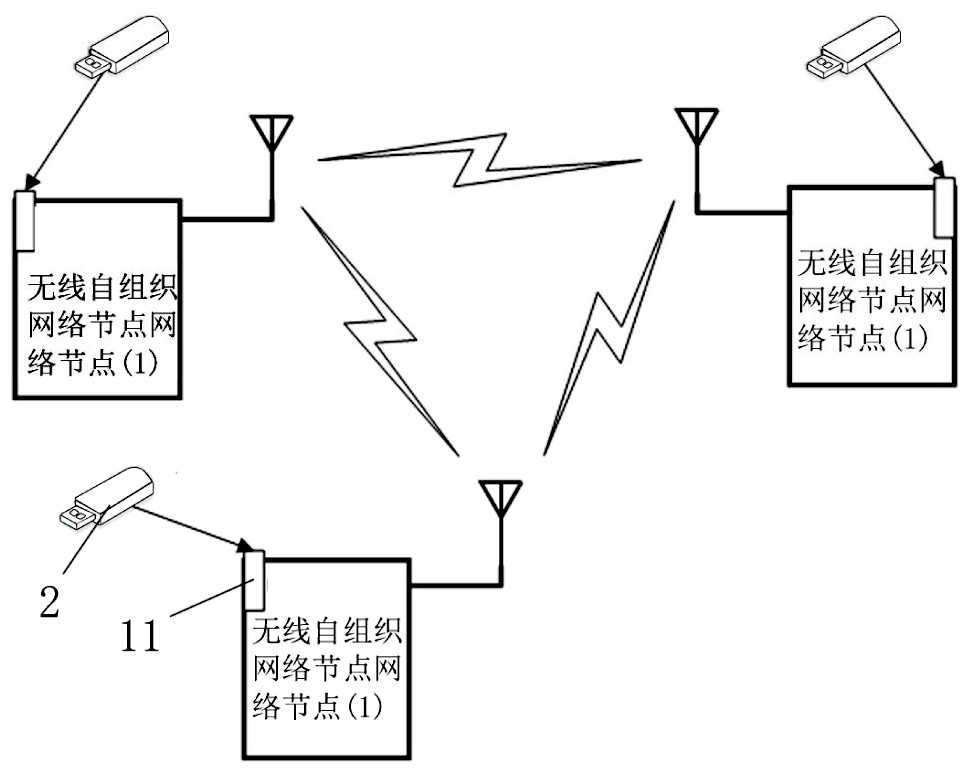
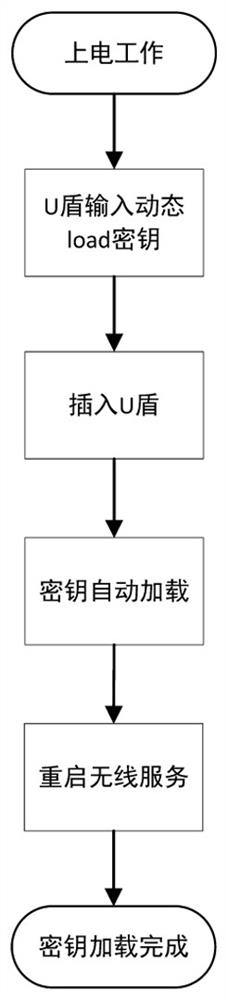
[0050] In the embodiment of the present invention, please refer to Figure 1-6 , a wireless multi-hop self-organizing network encryption key dynamic loading device, comprising: a dynamic key U-shield (2), a USB interface (11), an automatic mounting device, a hot-swappable event execution device, and a key automatic loading device and network service restart device. The dynamic key U-shield (2) is connected to the wireless self-organizing network node (1) through the USB interface (11) to form an interface event, which triggers the automatic mounting device. After the mounting is completed, the hot plug action is detected through the kernel Plug event execution device, hot plug event execution device will call the automatic key loading device at last, load the latest dynamic key, after the key loading is completed, finally call the network service startup device, restart the network service of the wireless Mesh network, complete The process of dynamically loading encryption ke...
Embodiment 2
[0052] In the embodiment of the present invention, please refer to figure 2 , the present invention at first carries out dynamic key input (or change) on computer (computer / notebook etc. installs the equipment of corresponding drive software) with dynamic key U-shield (2) according to the requirement, power-on starts action (task) execution The required wireless ad hoc network node (1) (or a running device), make sure that the startup is complete or has been started (the indicator light is not flashing), insert the dynamic key U-shield (2) into the wireless ad hoc network node (1 ) on the USB interface (11), wait for the indicator light to flash three times at a rate of 1 time per second, and then stay on for 1 second. Indicates that all operations are completed (about 30s), and then insert the dynamic key U-shield (2) into another wireless ad hoc network node (1) device and repeat it. All devices in the network must be executed once.
[0053] The present invention has follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com