File encryption method, file decryption method, file encryption device, file decryption device and computer-readable storage medium
A file encryption, computer program technology, applied in secure communication devices, electrical components, key distribution, and can solve problems such as content leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
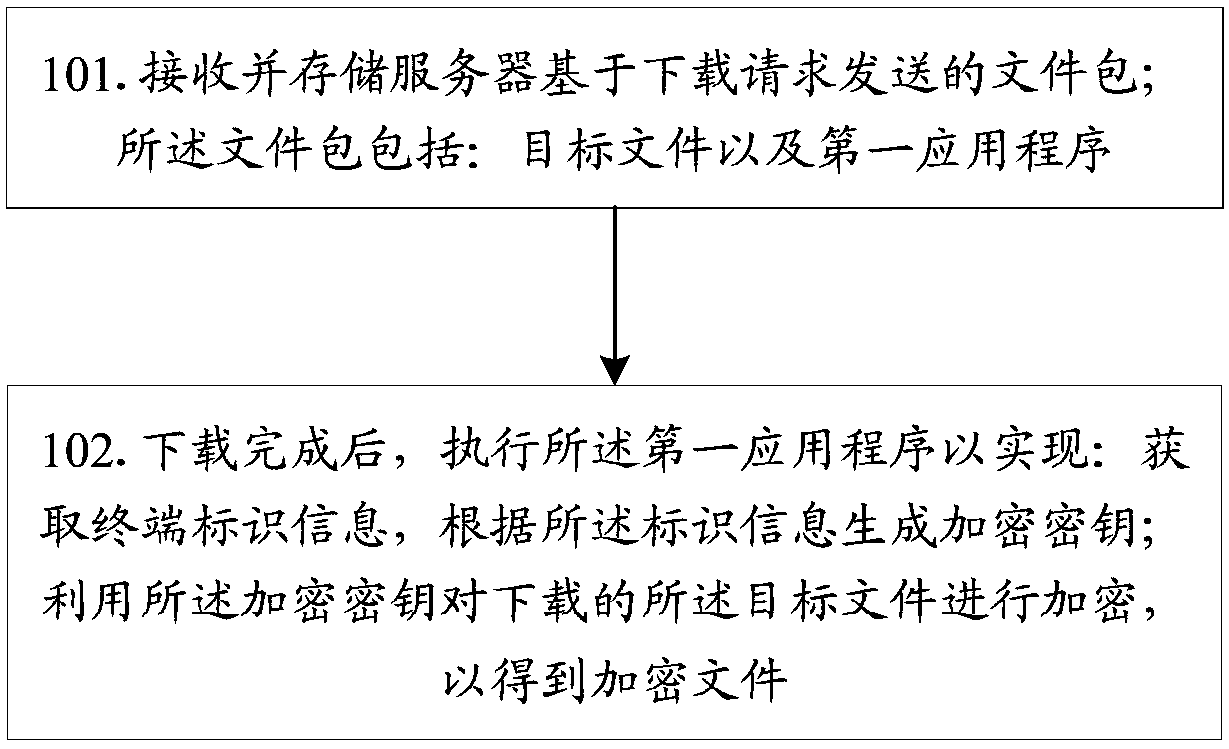
[0057] Such as figure 1 As shown, this embodiment takes the terminal side as an example to describe the file encryption method in detail, including the following steps:
[0058] Step 101: Receive and store the file package sent by the server based on the download request.
[0059] Wherein, the file package includes: an object file, and a first application program capable of realizing a first predetermined function after being executed. The target file is a file required by the user; the first predetermined function includes: obtaining terminal identification information, generating an encryption key according to the identification information, and using the encryption key to encrypt the downloaded target file.
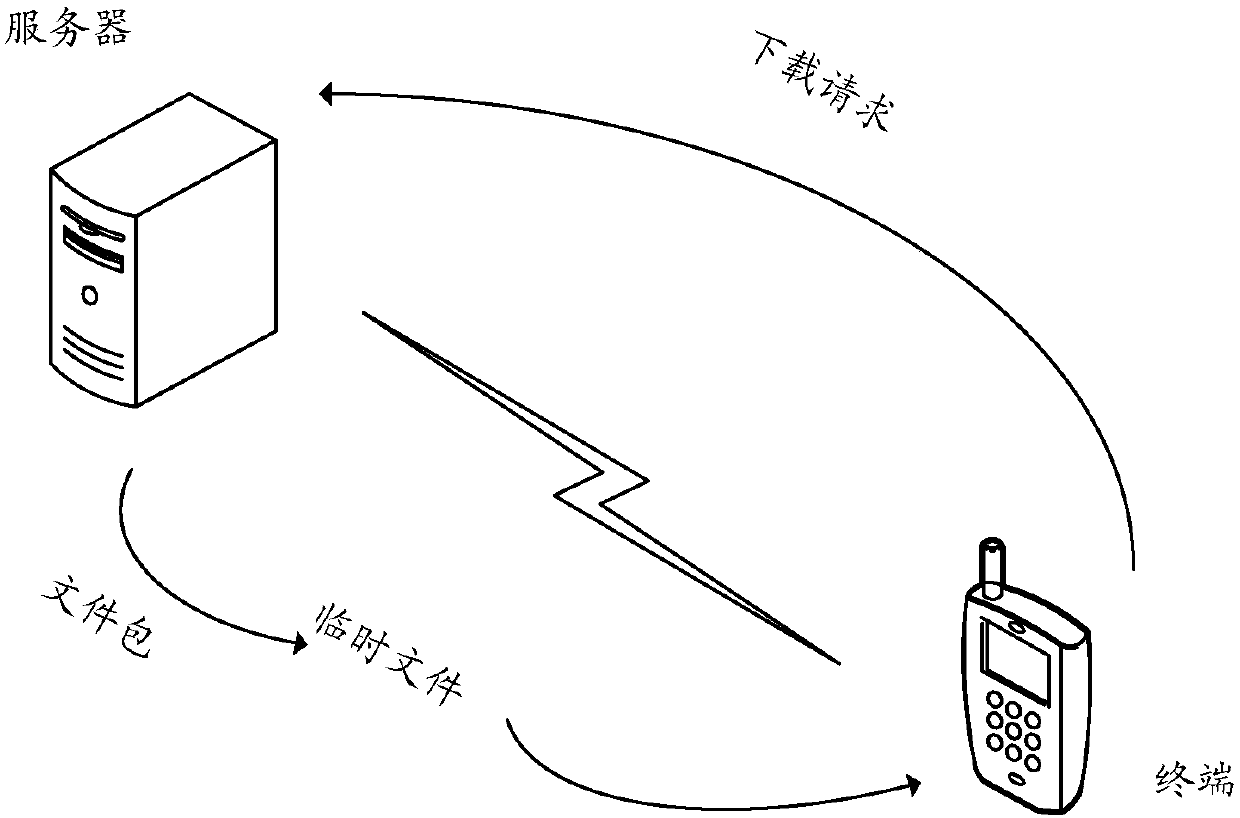
[0060] figure 2 In an implementation manner, it is a schematic diagram of a terminal receiving a file package sent by a server. Such as figure 2 As shown, before the terminal receives and stores the file package sent by the server, the terminal sends a download e...
Embodiment 2
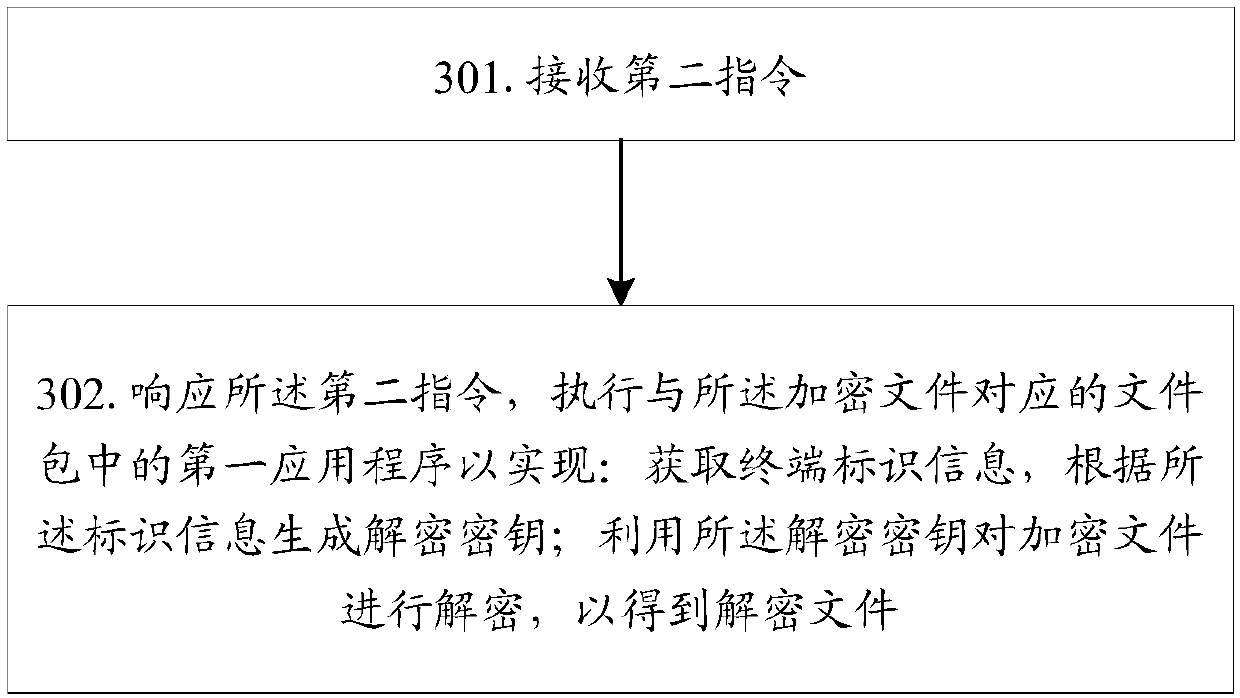
[0111] Such as image 3 As shown, this embodiment takes the terminal side as an example to describe the file decryption method in detail, including the following steps:
[0112] Step 301: Receive a second instruction; the second instruction is used to instruct to decrypt the encrypted file.
[0113] The encrypted file is a file encrypted with an encryption key generated from terminal identification information.
[0114] Step 302: In response to the second instruction, execute the first application program in the file package corresponding to the encrypted file to: obtain terminal identification information, generate a decryption key according to the identification information; use the decryption key Decrypt the encrypted file to obtain the decrypted file.
[0115] Wherein, the file package is sent by the server to the terminal based on the download request; the file package includes: a target file and a first application program capable of realizing a second predetermined fu...
Embodiment 3
[0119] In order to implement the method in Embodiment 1, this embodiment provides a file encryption device, which can be set on the terminal, such as Figure 4 As shown, the device includes: a first receiving module 41, an encryption module 42; wherein,
[0120] The first receiving module 41 is configured to receive and store the file package sent by the server based on the download request;
[0121] The encryption module 42 is configured to start the first application program after the download is completed.
[0122] The functions that can be realized by the first application program include: acquiring terminal identification information, and generating an encryption key according to the identification information; using the encryption key to encrypt downloaded files to obtain encrypted files.
[0123] In the embodiment of the present application, the "starting the first application program" mentioned here can put the first application program in the state of being executed,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com