Protection method and device for target program, equipment and storage medium
A target program and equipment technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
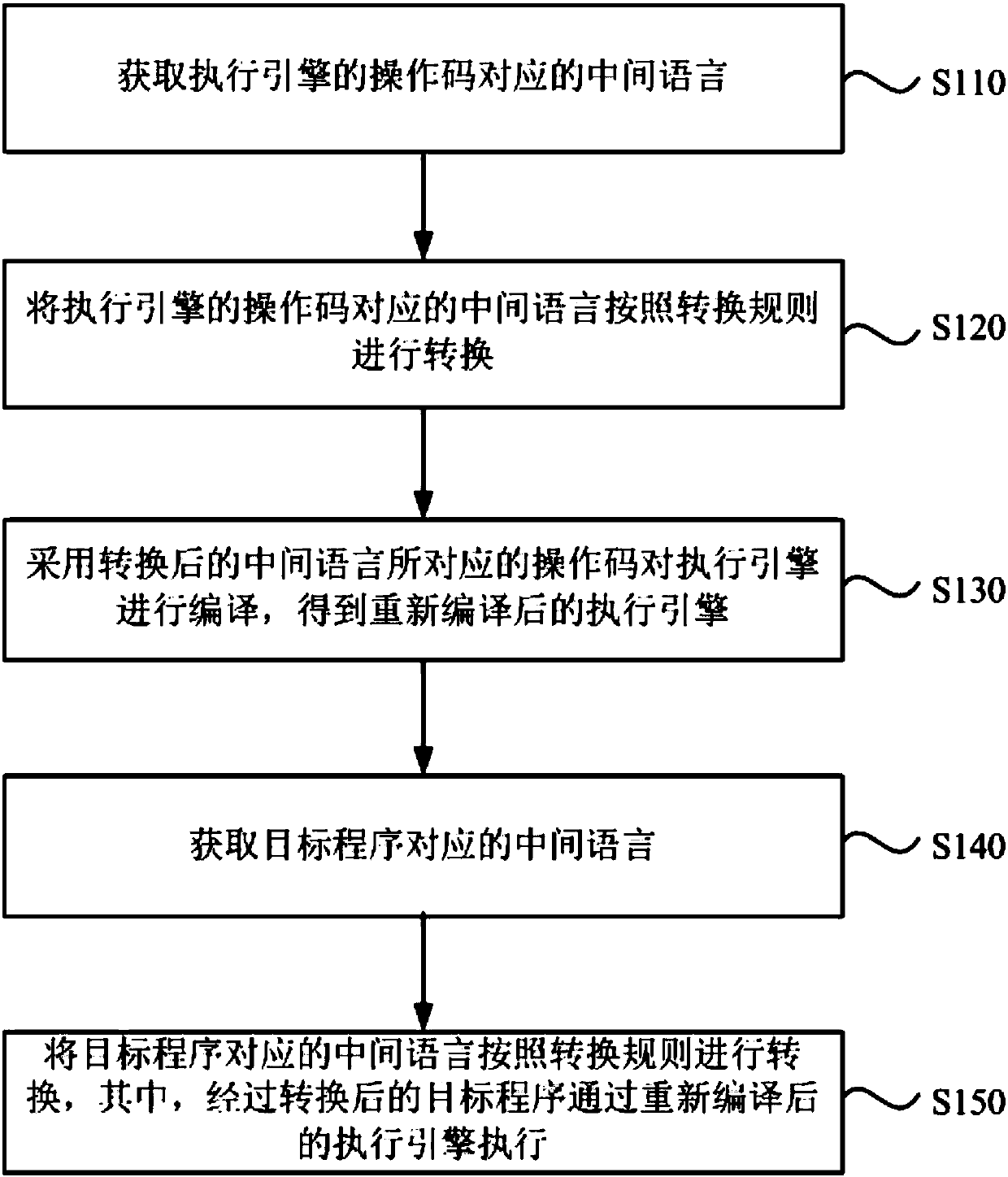
[0049] figure 1 It is a flow chart of a method for protecting a target program provided in Embodiment 1 of the present invention. This embodiment is applicable to the protection of a target program, and the method can be executed by the device for protecting a target program provided in the embodiment of the present invention. The device can be realized by means of software and / or hardware, and the device can be integrated in any terminal equipment that requires the protection of the target program, such as figure 1 As shown, the method specifically includes the following steps:
[0050] S110. Obtain an intermediate language corresponding to the operation code of the execution engine.
[0051] Wherein, the intermediate language (IL, Intermediate Language) is an intermediate language derived on the Microsoft platform, and the compilers of various high-level languages (such as C#, VB, F#) on the platform will convert respective codes into IL , which contains various elements...
Embodiment 2
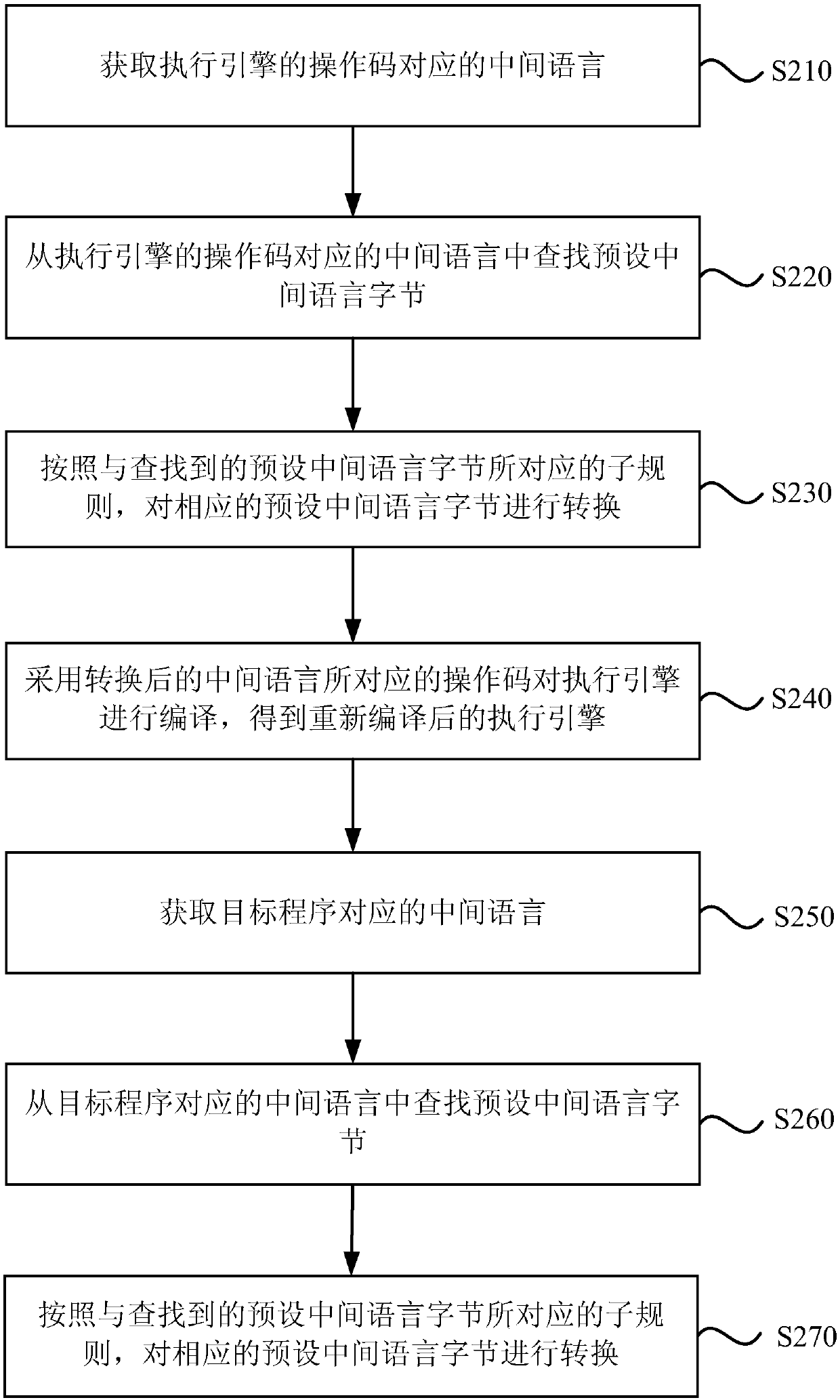
[0071] figure 2 It is a flow chart of a method for protecting a target program in Embodiment 2 of the present invention. This embodiment is optimized on the basis of the foregoing Embodiment 1, and provides a preferred method for protecting a target program. Specifically, the conversion rules include : a subrule for converting the preset intermediate language bytes; converting the corresponding intermediate language in the following manner, including: searching for the preset intermediate language bytes from the corresponding intermediate language; A subrule corresponding to the intermediate language byte is set to convert the corresponding preset intermediate language byte.
[0072] Correspondingly, the method in this embodiment specifically includes the following steps:
[0073] S210. Obtain an intermediate language corresponding to the operation code of the execution engine.
[0074] S220. Search for preset intermediate language bytes from the intermediate language corre...
Embodiment 3
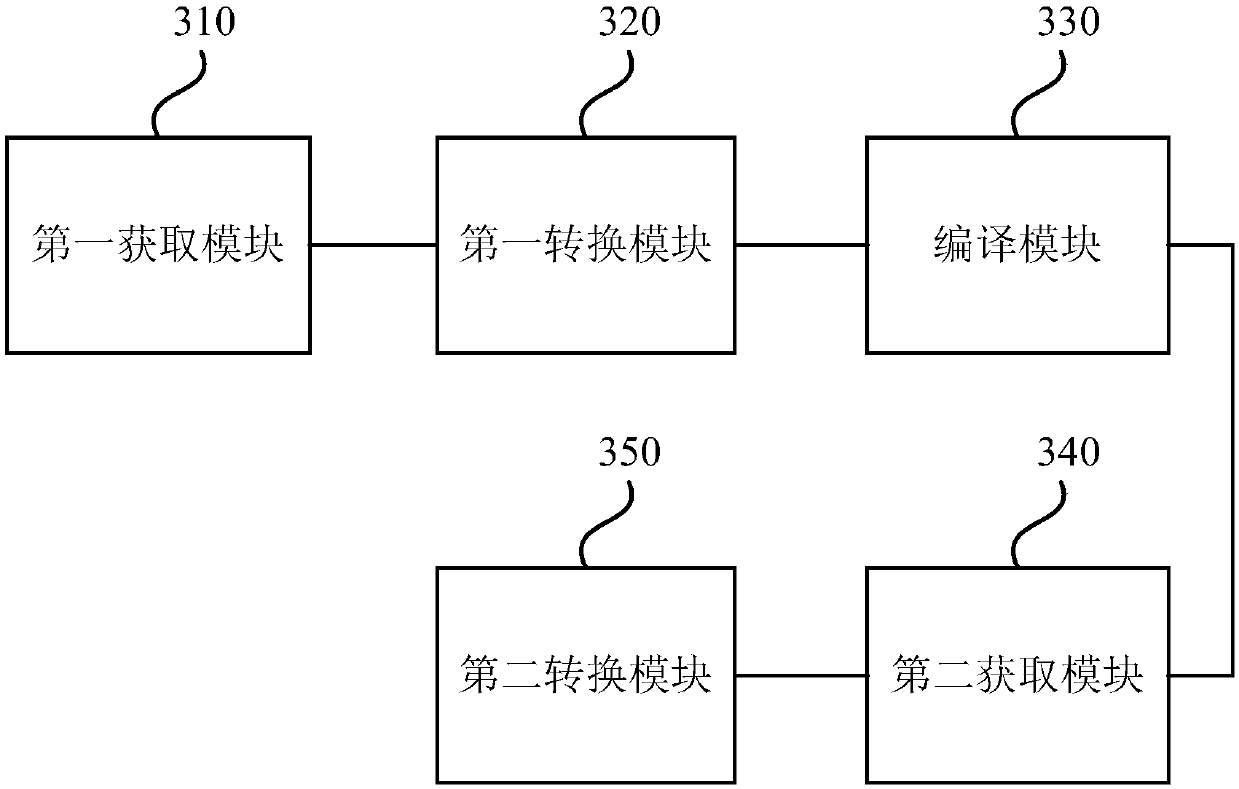
[0094] image 3 It is a schematic structural diagram of an object program protection device according to Embodiment 3 of the present invention. This embodiment can be applied to the protection of the target program, the device can be implemented in the form of software and / or hardware, and the device can be integrated in any device that provides the protection function of the target program, such as image 3 As shown, the device for protecting the target program specifically includes: a first acquisition module 310 , a first conversion module 320 , a compilation module 330 , a second acquisition module 340 and a second conversion module 350 .
[0095] Wherein, the first obtaining module 310 is used to obtain the intermediate language corresponding to the operation code of the execution engine;
[0096] The first conversion module 320 is configured to convert the intermediate language corresponding to the operation code of the execution engine according to conversion rules;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com