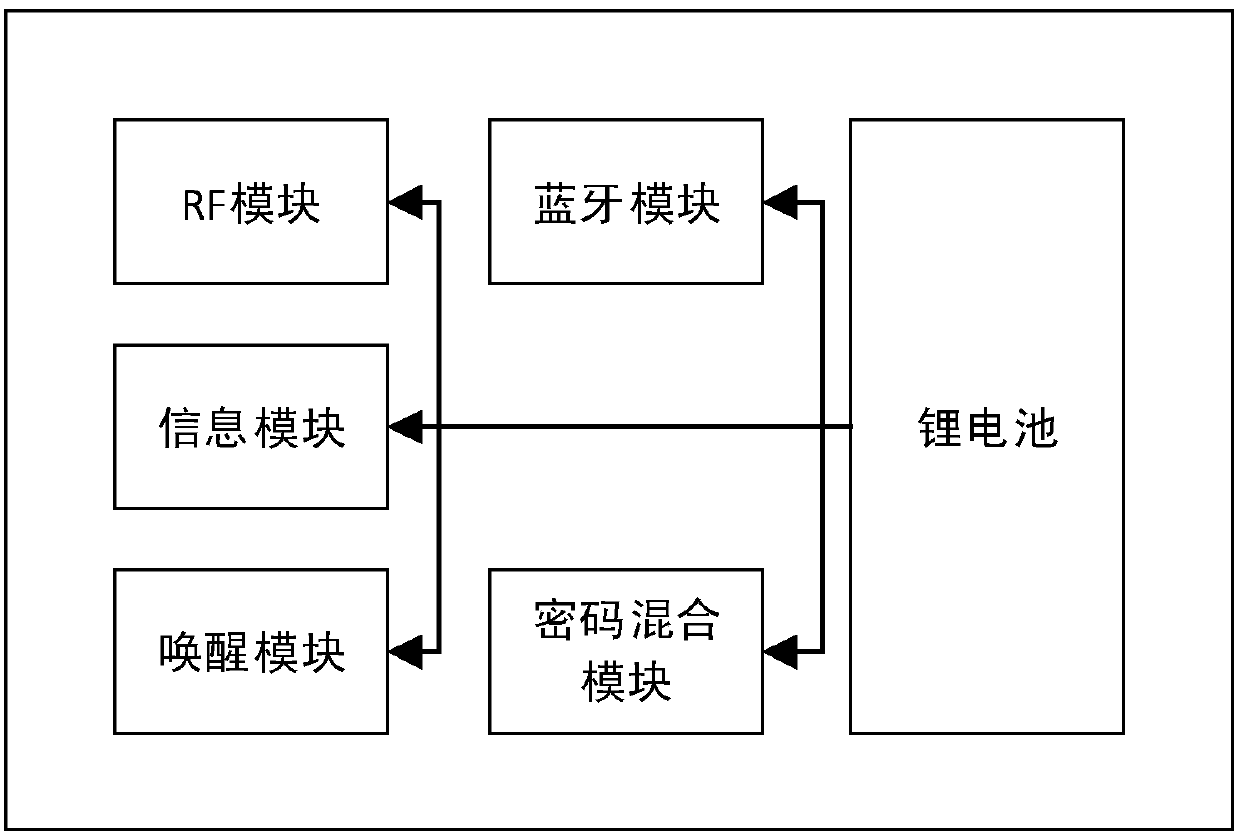
Near field identification-based identity information indication all-purpose card system
A technology of identity information and near-field recognition, applied in the field of one-card system, which can solve the problems of clutter, inconsistent application scenarios, and increased trouble for users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] The communication terminal is connected to the access control system, and the user brings the user card close to the communication terminal. After a series of communications between the communication terminal and the user card, the confirmation is confirmed by feedback on the display screen of the communication terminal whether the access control is enabled. After confirming with the function key, the control access control system is turned on.
Embodiment 2
[0038] The communication terminal is connected to the POS machine, the user brings the user card close to the communication terminal, binds the user card with the bank card, operates through the smart phone APP, writes the bank card information into the user card, and the user brings the user card close to the communication terminal, and the communication terminal Send the data with bank card information to the POS machine. After a series of communications between the communication terminal and the user card, confirm whether the POS machine consumption information is confirmed by feedback on the display screen of the communication terminal. After confirmation, the POS machine consumption can be carried out. There is no need to take out the user card for active card swiping operations.
Embodiment 3
[0040] The communication terminal is connected to the access control system. The user brings the user card close to the communication terminal. After a series of communications between the communication terminal and the user card, the communication terminal recognizes the user's face information through the camera and transmits it to the data center through the feedback on the display screen of the communication terminal. The central server and the data center server use the facial feature information for comparison. After the comparison is successful, they are compared with the certificate information of the public security system to confirm the authenticity of the information. If the comparison is successful, the display screen of the communication terminal pops up the information to confirm whether to open the access control. After the confirmation function key on the communication terminal confirms, the access control system is controlled to open.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com