Safety Top-k query method facing to double-layered sensing network and device
A query method and sensor network technology, applied in the field of double-layer sensor network security defense, can solve problems such as network data privacy and integrity threats, and achieve the effects of ensuring data privacy, reducing communication costs, and reducing redundancy ratios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] like figure 1 Shown, a kind of safety Top-k query method facing double-layer sensor network of the present invention, comprises the following steps:
[0040] Step S101: Perform preprocessing on the data items generated by the sensor node in the same time slot, and generate a preprocessing result data packet.
[0041] Step S102: The supervisor node receives the Top-k query request from the Sink node, and according to the ciphertext value of the data item weight encrypted by the OPES encryption method, searches for the Top-k data item encryption that meets the query request in the data item stored in itself. Text, the Top-k data item ciphertext that meets the query request together with security detection information is sent to the Sink node as the Top-k query result.
[0042] Step S103: The Sink node receives the Top-k query result, finds the corresponding shared symmetric key according to the key in the query result, uses the shared symmetric key to decrypt the ciphert...
Embodiment 2
[0046] like figure 2 Shown, another kind of security Top-k inquiry method facing double-layer sensor network of the present invention, comprises the following steps:
[0047] Step S201: Before the deployment of the two-layer sensor network, that is, before the deployment of TWSNs, each sensor node pre-distributes its own shared symmetric key with the Sink node, and downloads the key material used for OPES encryption in advance at the same time:
[0048] Construct the network model of TWSNs, assuming that there are N sensor nodes and M supervisor nodes in the network, the entire TWSNs deployment area is divided into M units, and a supervisor node H is deployed in the cth (1≤c≤M) unit c and Nc (N=N 1 +N 2 +…+N c +…+N M-1 +N M ) sensor nodes {S 1,c ,S 2,c ,S 3,c ,...,S N-1,c ,S N,c}. S i,c (1≤i≤N c ,1≤c≤M) can be connected with H through single-hop or multi-hop c to communicate. For the convenience of description, S i,c abbreviated as S i . Let T denote the net...
Embodiment 3
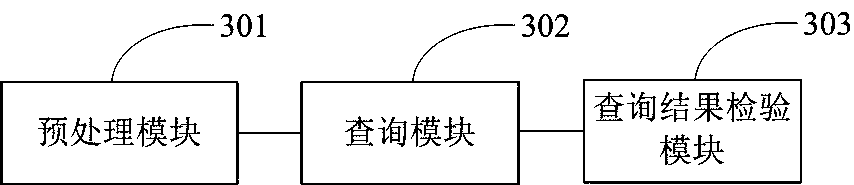
[0092] like image 3 Shown, a kind of safety Top-k inquiry device facing double-layer sensor network of the present invention comprises:
[0093] The preprocessing module 301 is configured to preprocess the data items generated by the sensor nodes in the same time slot, and generate a preprocessing result data packet.
[0094] The query module 302 is used for the supervisor node to receive the Top-k query request from the Sink node, and to search for the Top-k that satisfies the query request in the data items stored in itself according to the ciphertext value of the data item weight encrypted by the OPES encryption method Data item ciphertext, the Top-k data item ciphertext that meets the query request together with security detection information is sent to the Sink node as the Top-k query result.
[0095] Query result verification module 303, used for Sink node to receive Top-k query result, find corresponding shared symmetric key according to the key in the query result, u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com