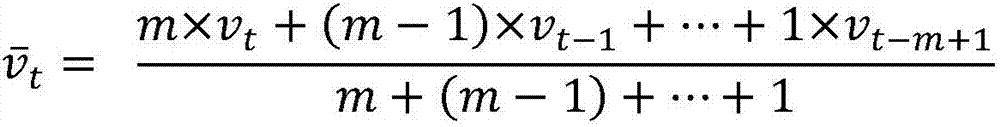Invasion detection method based on channel state information and support vector machine
A channel state information, support vector machine technology, applied in computer parts, character and pattern recognition, transmission monitoring and other directions, can solve problems such as coarse-grained and volatile unsuitable for accurate perception, poor intrusion detection accuracy, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] Specific embodiments of the present invention will be described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention. It should be noted that in the following description, the introduction of known functions and designs related to the present invention may be downplayed and omitted.
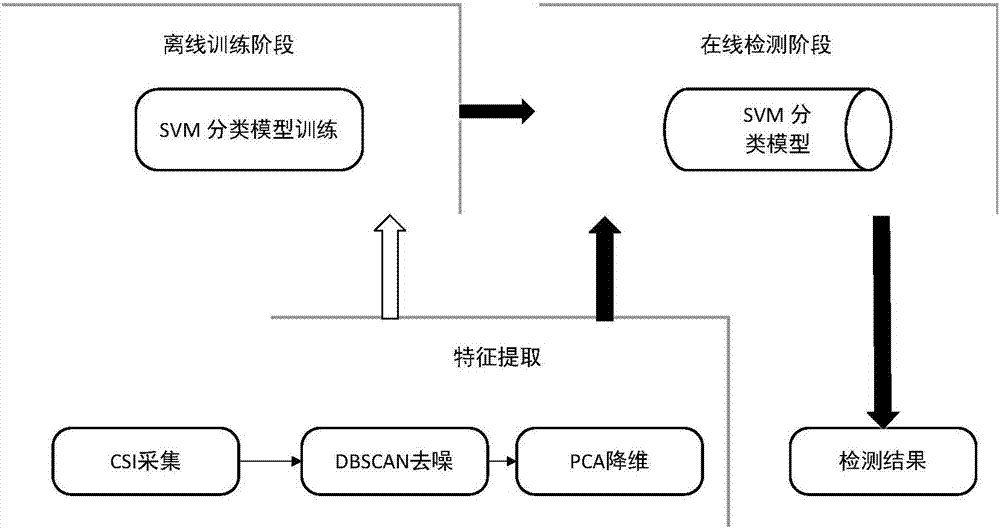
[0015] In this embodiment, the intrusion detection and identification method of the present invention mainly includes the following links: data collection, data preprocessing, data feature extraction, intrusion detection and identification, and the process is as follows: figure 1 As shown, the specific implementation steps are as follows:
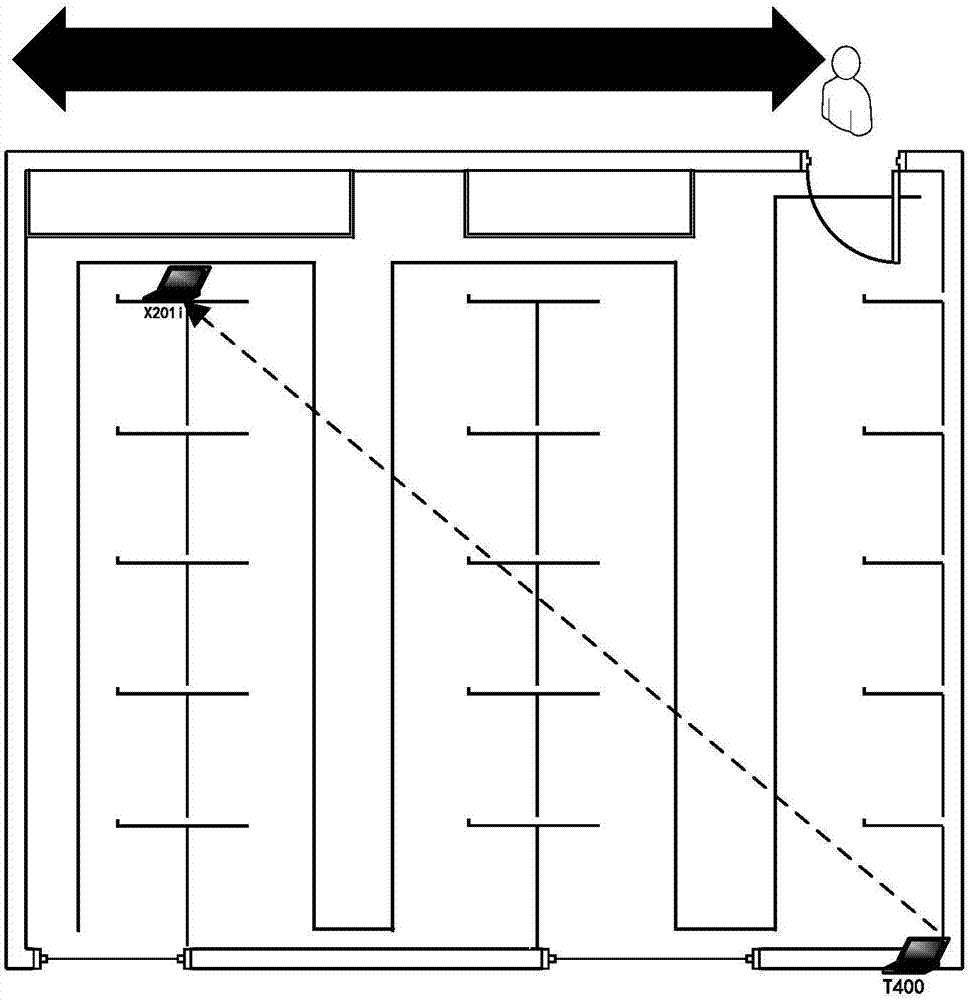
[0016] Step 1: Environmental deployment, Wi-Fi-based intrusion detection and identification requires indoor coverage of Wi-Fi signals. The layout of the experimental scene is 6 meters long and 7 meters wide. The system selects the 5G frequency band with less signal interference...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com