Inter-domain routing system mimicry protection method based on AS security alliance
An alliance and security technology, applied in the field of Internet security, can solve problems such as difficulty in effectively preventing BGP-LDoS attacks, link congestion, exhaustion of router computing and storage resources, etc. Probability, Effects of Increased Cost and Complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
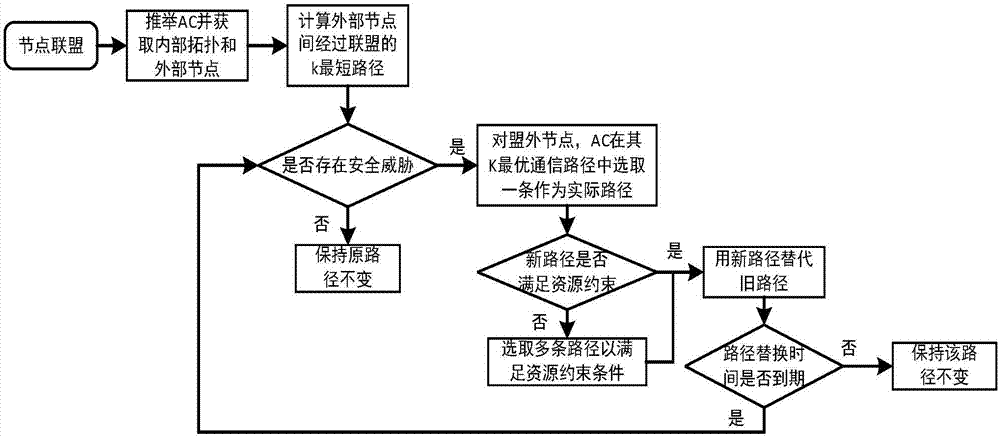
[0030] Combine below figure 1 with figure 2 Describe this application in detail;
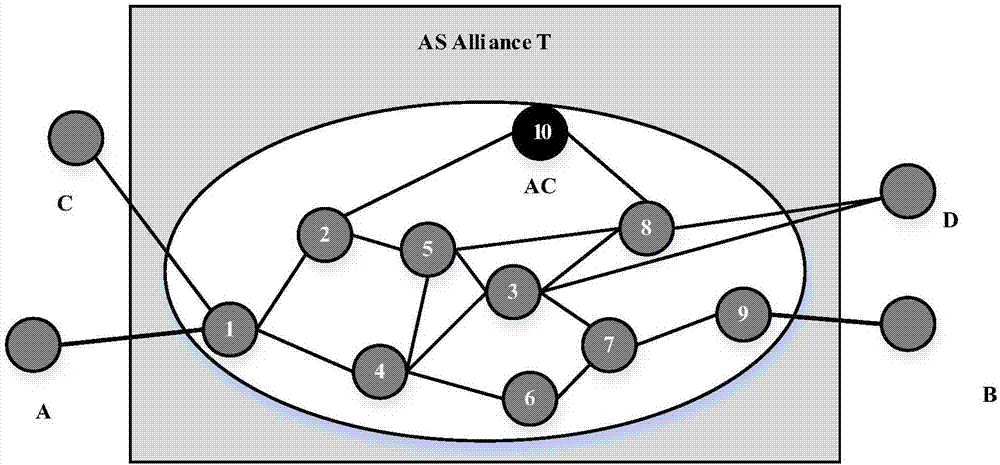
[0031] Such as figure 1 In AS1 and AS10, an AS alliance T is established. After the alliance, each node selects 10 as AC according to its own processing capabilities and connection relationship. Other ASs send their connection relationship to AC, and AC obtains the connection between each node The relationship determines the set of 4 external nodes {A, B, C, D} connected by the alliance. Through analysis, the AC obtains the actual paths of this node set through the alliance as A 1 4 3 7 9 B, C 1 4 5 8 D, B 9 7 3 D.
[0032] According to the size of the security threat, if the threat is small, the AC can keep the original actual path unchanged. If the threat is greater, AC calculates the shortest path k for all external nodes passing through the alliance. For example, for C and D, the other two shortest paths are C 1 2 5 8 D and C 1 2 10 8 D respectively. One of the paths is randomly adopted as th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com