A method and system for identifying web intrusion
A suspicious and score-based technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as security monitoring mechanism dependence, and achieve the effect of reducing the vulnerability rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to better understand the present invention, the content of the present invention will be further described below with reference to the accompanying drawings and examples.
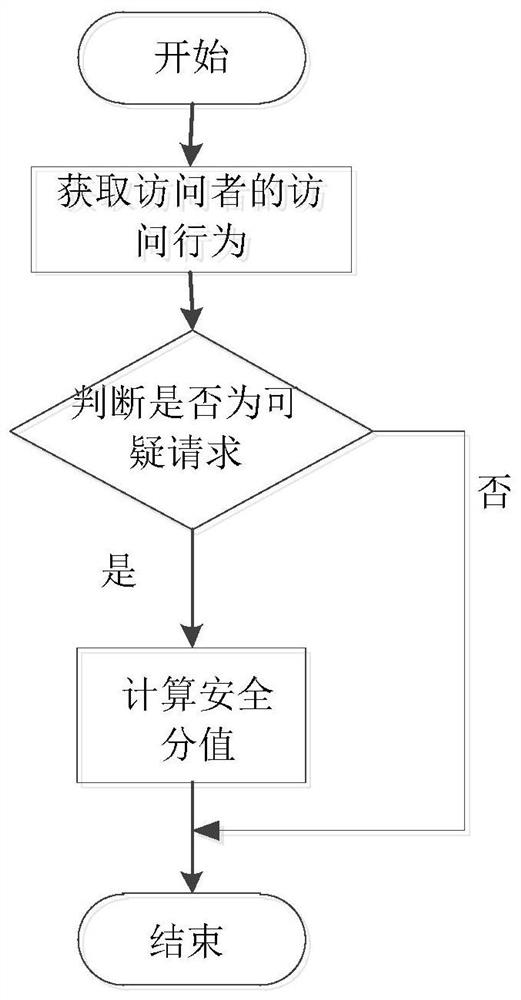
[0055] The present invention provides a method for identifying WEB intrusion, such as figure 1 As shown, the method is specifically:
[0056] Obtain the access behavior of visitors;
[0057] Judging whether the access behavior is a suspicious request, and if it is a suspicious request, according to a preset suspicious score evaluation standard, accumulating the suspicious scores involved in the access behavior to obtain a safety score;
[0058] When the security score is greater than the preset threshold, the user behaves abnormally and there is WEB intrusion.
[0059] This method is further refined as follows:
[0060] Step 1: Establish a trusted architecture for the WEB website. The principle of the trusted architecture is that all the current contents of the WEB website are trusted.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com