A method and device for analyzing phishing based on dns logs
A technology of phishing and analysis methods, applied in the field of phishing analysis methods and devices based on DNS logs, can solve the problems of poor identification accuracy of phishing websites, etc., and achieve short survival period of sites, poor mitigation identification accuracy, and strong camouflage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
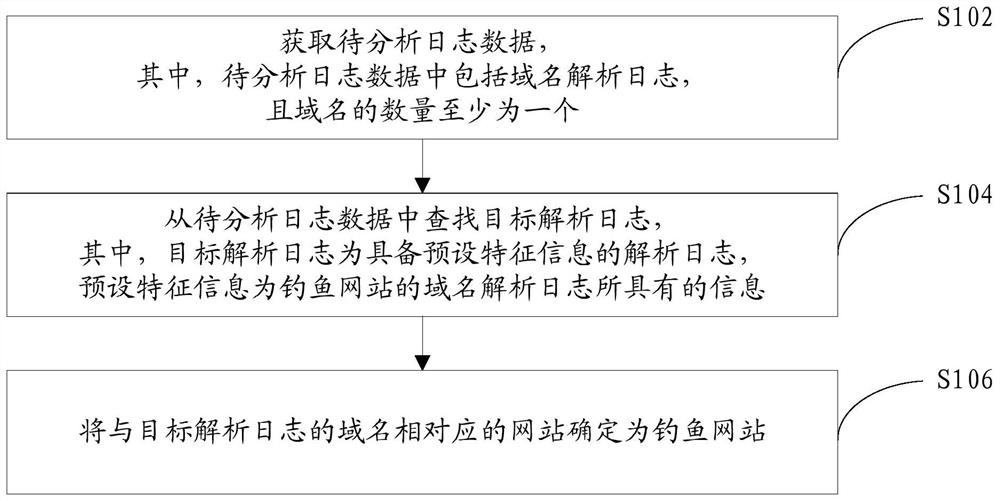
[0054] A kind of phishing analysis method based on DNS log that the embodiment of the present invention provides, such as figure 1 shown, including:
[0055] Step S102, obtaining log data to be analyzed, wherein the log data to be analyzed includes domain name resolution logs, and the number of domain names is at least one;
[0056] Step S104, searching for the target resolution log from the log data to be analyzed, wherein the target resolution log is a resolution log with preset characteristic information, and the preset characteristic information is information contained in the domain name resolution log of the phishing website;
[0057] Step S106, determining the website corresponding to the domain name of the target parsing log as a phishing website.
[0058] In the embodiment of the present invention, the target resolution log is searched from the log data to be analyzed, the log data to be analyzed includes the domain name resolution log, the target resolution log is a...
Embodiment 2
[0132] An embodiment of the present invention provides a DNS log-based phishing analysis device, such as Figure 4 shown, including:
[0133] The acquiring module 100 is configured to acquire log data to be analyzed, wherein the log data to be analyzed includes domain name resolution logs, and the number of domain names is at least one;
[0134] The search module 200 is used to search for the target analysis log from the log data to be analyzed, wherein the target analysis log is an analysis log with preset characteristic information, and the preset characteristic information is information contained in the domain name resolution log of the phishing website;
[0135] The determination module 300 is configured to determine the website corresponding to the domain name of the target parsing log as a phishing website.
[0136] In the embodiment of the present invention, firstly, the acquisition module 100 acquires the log data to be analyzed, and then the search module 200 search...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com