Equipment pairing based safety authentication method
A technology for security authentication and equipment, which is applied in branch office equipment, digital data authentication, secure communication devices, etc., can solve problems such as difficulty in remembering different account names and passwords, and hacker attacks with the same account name and password, so as to reduce the number of crash attacks risk, the effect of increasing ease of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention aims to propose a security authentication method based on device pairing, which solves the problem in the traditional technology that using the same account name and password for multiple APPs is easy to be attacked by hackers, but it is difficult to remember when using different account names and passwords.
[0029] Below in conjunction with accompanying drawing and embodiment the scheme of the present invention will be further described:
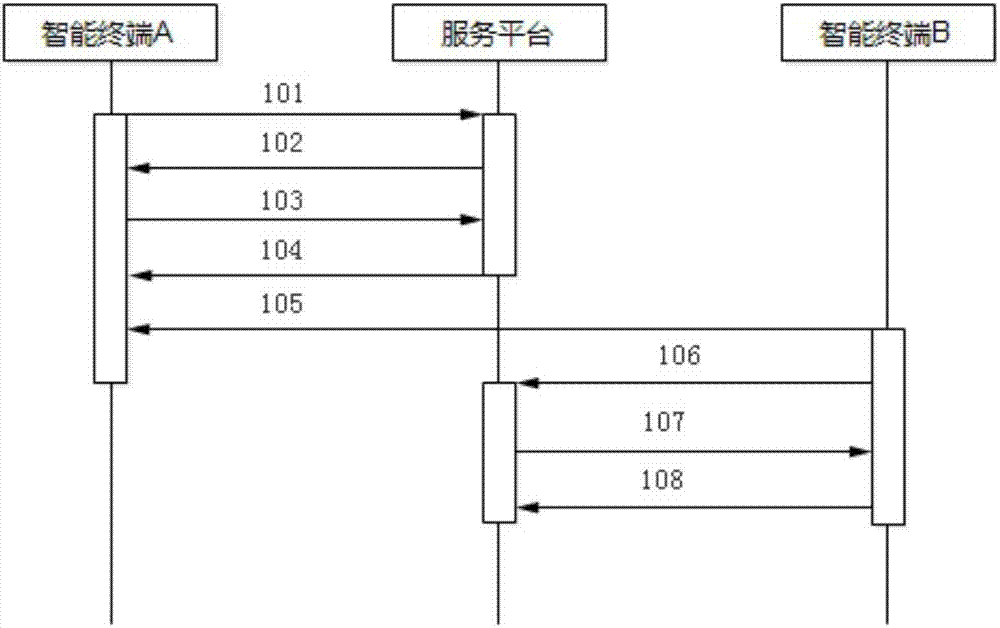
[0030] Such as figure 1 As shown, the security authentication method based on device pairing in this embodiment includes the following specific implementation steps:
[0031] Step 101: Smart terminal A initiates a login request to the service platform:
[0032] In specific implementation, the terminal APP application of the service platform can be installed on the software system of the smart terminal A, and the user uses the terminal APP application and uses its login function to initiate a login request to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com