Private cloud encrypted data access method, terminal and memory medium
A technology for encrypting data and accessing methods, applied in the field of cloud computing, can solve the problems of high risk of leakage, cumbersome and troublesome backup data, and difficult management and control of public cloud storage data, so as to achieve the effect of ensuring the user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
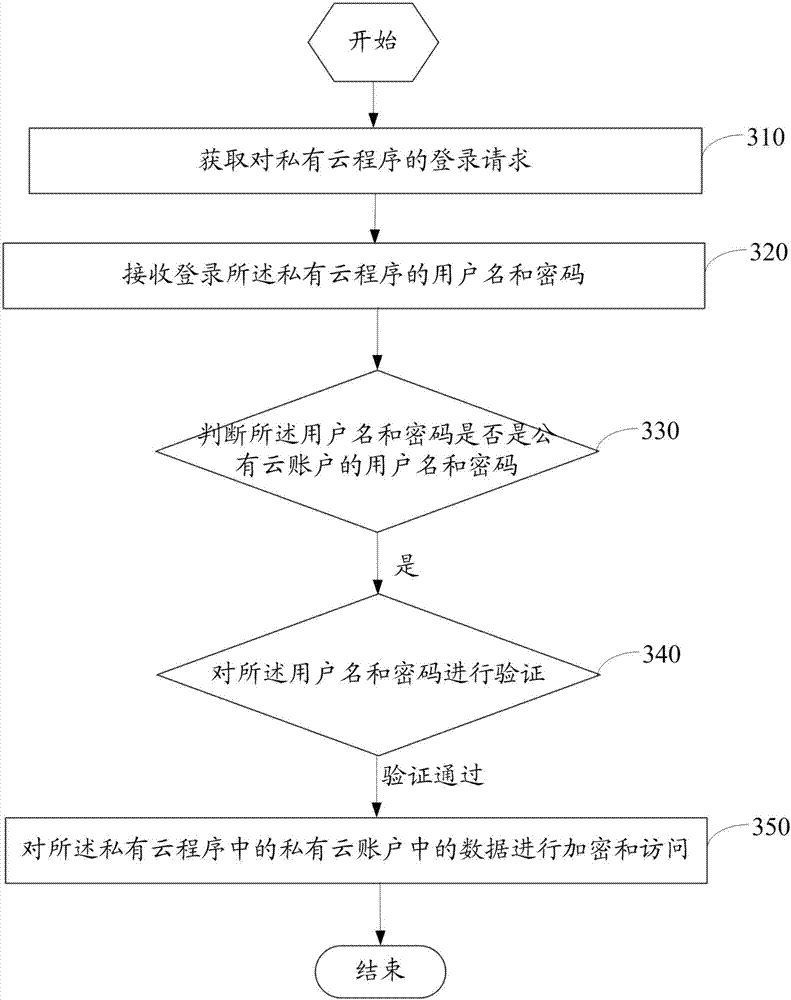
[0082] Such as image 3 As shown, it is the private cloud encrypted data access method provided in the first embodiment of the present application, and the method includes the following steps:
[0083] Step 310, obtaining a login request to the private cloud program;
[0084] Step 320, receiving the user name and password for logging into the private cloud program;
[0085] Step 330, judging whether the username and password are usernames and passwords of a public cloud account; if so, proceed to step 340;
[0086] Step 340, verify the user name and password, and enter step 350 when the verification is passed;
[0087] Step 350, when the user name and password are verified, encrypt and access the data in the private cloud account in the private cloud program.
[0088] Specifically, download the private cloud in the cloud service, and install it on the user's mobile terminal (such as a mobile phone) or a fixed terminal (such as a computer). After startup, the user name and ...
example 1
[0098] Example 1, the bytecode of a single file is 01101011, the bytecode of the sum of the user name and password is 10101000, and after XOR operation, the obtained bytecode is 11000011.
[0099] Further, such as Figure 5 As shown, the access to the data in the private cloud account in the private cloud program in step 330 includes:
[0100] Step 510, extracting the user name and password for logging into the private cloud program;
[0101] Step 520, judging whether the combined character string of the user name and password is the same as the encryption mask; if so, then enter step 530, if not, then the process ends;
[0102] Step 530, performing reverse XOR calculation on the files in the private cloud account;
[0103] Step 540, read the files in the private cloud account.
[0104] Specifically, after encrypting the data in the private cloud account, when logging in to the private cloud program again, first extract the user name and password when logging in to the priv...
no. 2 example
[0121] Such as Figure 7As shown, it is the private cloud encrypted data access method provided in the second embodiment of the present application. In the second embodiment, the private cloud encrypted data access method is a further improvement made on the basis of the first embodiment, the only difference is that the method also includes:
[0122] Step 710, synchronizing the data in the public cloud account to the private cloud account;
[0123] Step 720, saving the data in the public cloud account to a local database.
[0124] Specifically, when the user name and password are the user name and password of the public cloud account, the private cloud can start downloading the user's file in the public cloud. In this way, all the data of the user on the public cloud can be transferred to the private cloud, and the data in the private cloud can be stored in the local database of the terminal.
[0125] Optionally, after saving the data in the public cloud to the local databa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com