Hotlink protection method, device and system based on network terminal
A network terminal and anti-theft link technology, applied in the transmission system, electrical components, etc., can solve the problem of ineffective solution to the hot link problem and the poor effectiveness of the anti-theft link method, and achieve the effect of a safe anti-theft link mechanism and poor solution effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
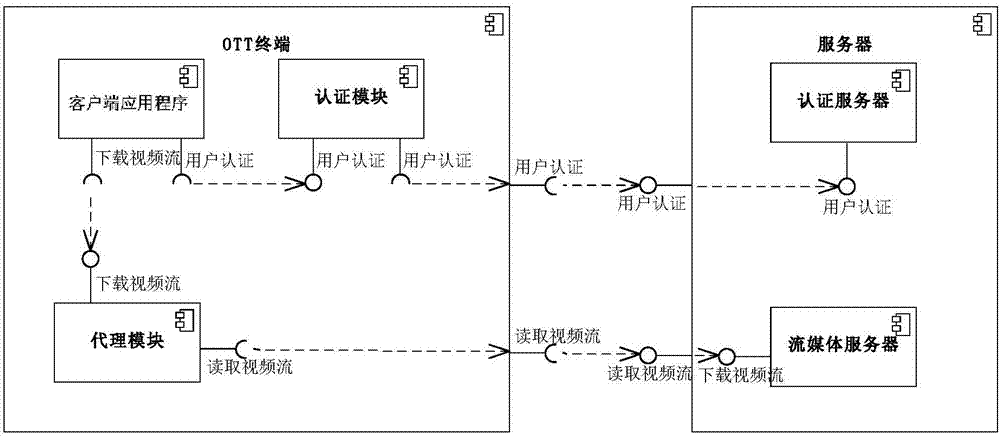
[0044] Embodiment 1 of the present invention describes an anti-leeching system based on network terminals. In this system, network terminals, media servers, and authentication servers are included. All network terminals and all servers are used as layer 0 components, which can be understood as clients respectively. and server side.
[0045] Among them, the network terminal is a client that responds to user operations to play multimedia, it interacts with the authentication server through the user authentication interface, and obtains playback information from the authentication server; The server obtains the media to be played.
[0046] The authentication server is a server that interacts with the network terminal to return playback information to the network terminal, and the media server is a server that interacts with the network terminal to return the media to be played to the network terminal.
[0047] Further, inside the network terminal, it includes a proxy module, a r...
Embodiment 2
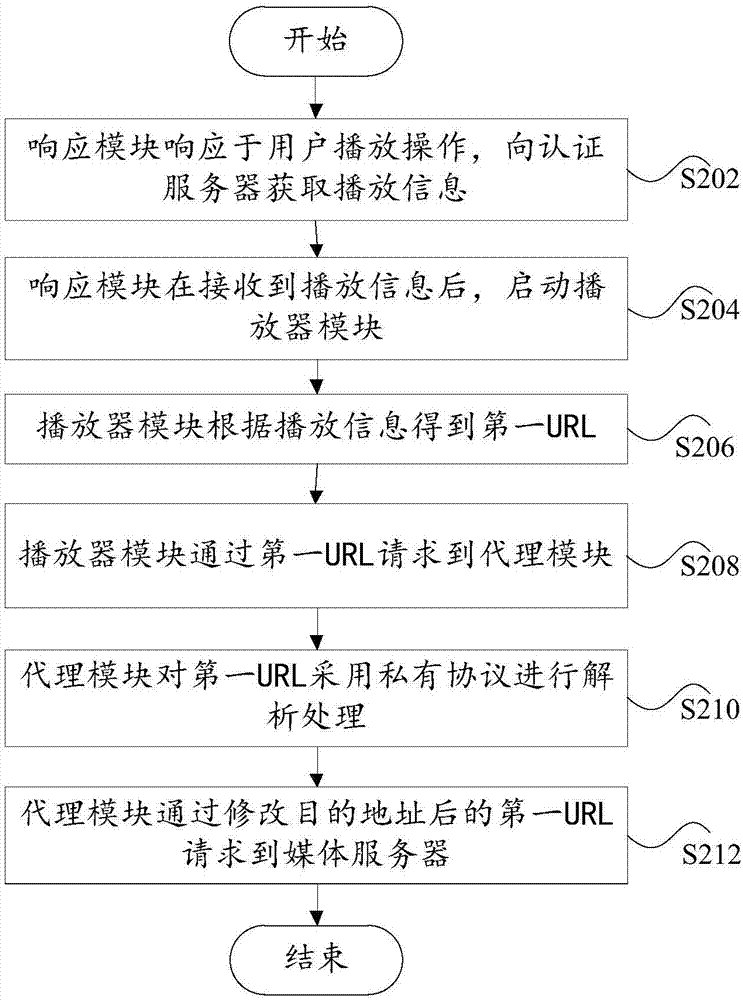
[0055] Embodiment 2 of the present invention describes an anti-leeching method based on a network terminal from the perspective of a network terminal. The network terminal includes a proxy module, a response module for responding to user playback operations, and a player module. The interaction between the servers realizes the response to the user's playback operation, and finally plays the multimedia that the user intends to watch. The focus of this embodiment is to realize anti-leeching during the interaction process. Specifically, as figure 2 As shown, the anti-leech method in this embodiment includes the following steps S202 to S212, and each step is described in detail as follows.
[0056] Step S202: The response module obtains the playing information from the authentication server in response to the user's playing operation.
[0057] The response module can be a client application program installed in the network terminal, such as a browser. When the user wants to play...
Embodiment 3
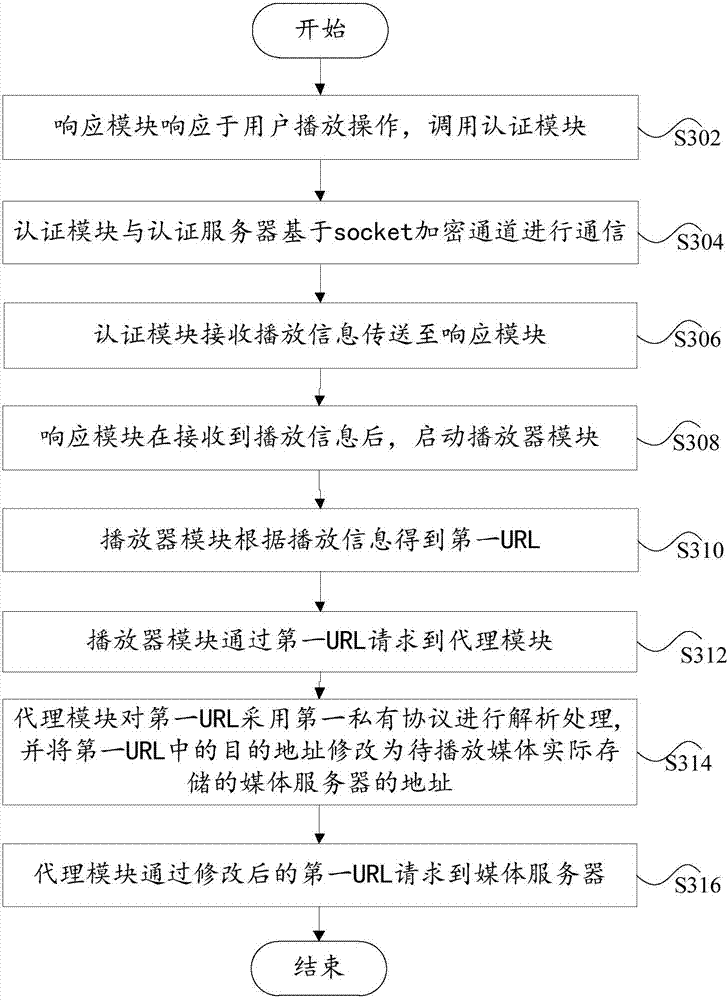
[0070] Embodiment 3 of the present invention is a preferred embodiment on the basis of Embodiment 2 above. In this preferred embodiment, the network terminal further includes an authentication module. Specifically, such as image 3 As shown, the anti-leech method in this embodiment includes the following steps S302 to S316, and each step is described in detail as follows.
[0071] Step S302: The response module invokes the authentication module in response to the user's playback operation.
[0072] The user performs a playback operation through the response module, and the response module responds by first obtaining the description information of the media to be played corresponding to the playback operation. The description information of the media is used as a parameter, and the authentication module is requested by the HTTP protocol.
[0073] Step S304: The authentication module communicates with the authentication server based on the socket encrypted channel, and obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com