Data information dynamic encryption method capable of preventing violent decryption
A technology of dynamic encryption and data information, applied in the computer field, to achieve the effect of ensuring encryption, improving security, and high randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] The method for dynamically encrypting data information of the present invention comprises the following steps:
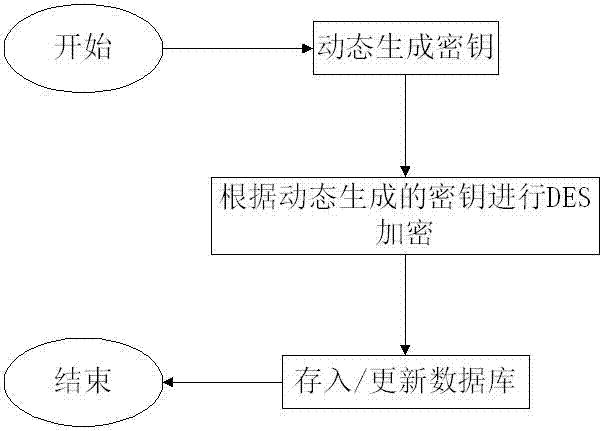
[0027] as attached figure 1 As shown, (1), encryption
[0028] (1) Dynamically generate the encryption key, by controlling the length of the number, dynamically generate a two-digit random number, and then randomly form a dynamic key of numbers and English letters;
[0029] (2), perform DES encryption according to the key generated dynamically, that is, use the key to perform DES encryption, and then use the DES encryption method that oracle itself carries to encrypt the data that needs to be encrypted through the dynamic key;
[0030] (3), secondary encryption, the dynamically generated key and the encrypted ciphertext data are spliced together for secondary encryption;
[0031] (4) Update the database of the data.
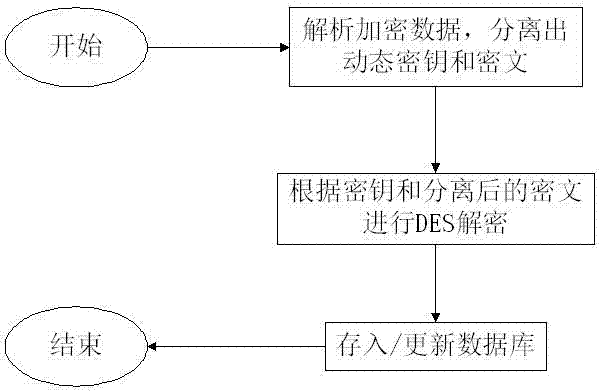
[0032] as attached figure 2 As shown, (2), decryption
[0033] (1) Decrypt for the first time, analyze the encrypted data, separate the...
Embodiment 2
[0037] A method for dynamically encrypting data in a table in a military software system includes the following contents and steps:
[0038] ①. Create the encryption function INSPUR_JTGK_KEY(P_TEXT VARCHAR2), the specific code SQL example:
[0039]
[0040]
[0041] ②. Create the decryption function INSPUR_JTGK_DESKEY(P_TEXT VARCHAR2), the specific code SQL example:
[0042]
[0043]
[0044] ③. Create the table SADSADAS, and create the standard SQL as follows:
[0045]
[0046] The X field is the unique index of the data, and the Y field is the encrypted field.
[0047] Encryption tests were performed on the data ""World Competitiveness Report 2017" evaluates each economy based on the four competitiveness factors of "economic performance", "government efficiency", "business efficiency" and "infrastructure".
[0048] INSERT INTO SADSADAS(X,Y)VALUES(SYS_GUID(),INSPUR_JTGK_KEY('The 2017 World Competitiveness Report is evaluated based on the four competitiveness ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com