Database management method, device and system and storage medium and device
A management method and database technology, applied in database design/maintenance, electronic digital data processing, special data processing applications, etc., can solve problems such as customer inconvenience, customers' inability to access databases and business terminals normally, and service quality of service providers. , to achieve the effect of quickly solving and guaranteeing business needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
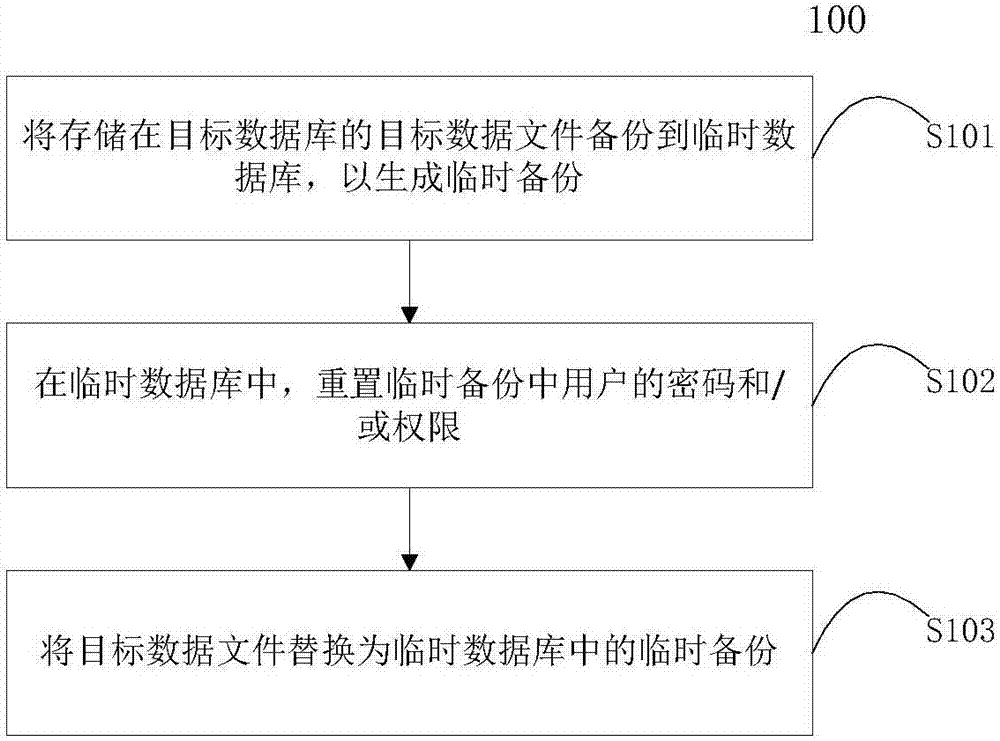
[0028] The following will combine figure 1 The database management method 100 according to the embodiment of the present invention is described in detail.
[0029] figure 1 is a flowchart of the database management method 100 according to the embodiment of the present invention. Such as figure 1 As shown, in step S101, the target data file stored in the target database is backed up to the temporary database to generate a temporary backup.
[0030]According to the embodiment of the present invention, the temporary database can be set on the physical machine of the target database or on other physical machines. Physical machines include, but are not limited to: microcomputers, minicomputers, mid-range computers, mainframes, supercomputers or other physical devices capable of running databases. When the temporary database and the target database are on the same physical machine, the user table that needs to be reset in the target database can be directly copied to the tempora...
no. 2 example
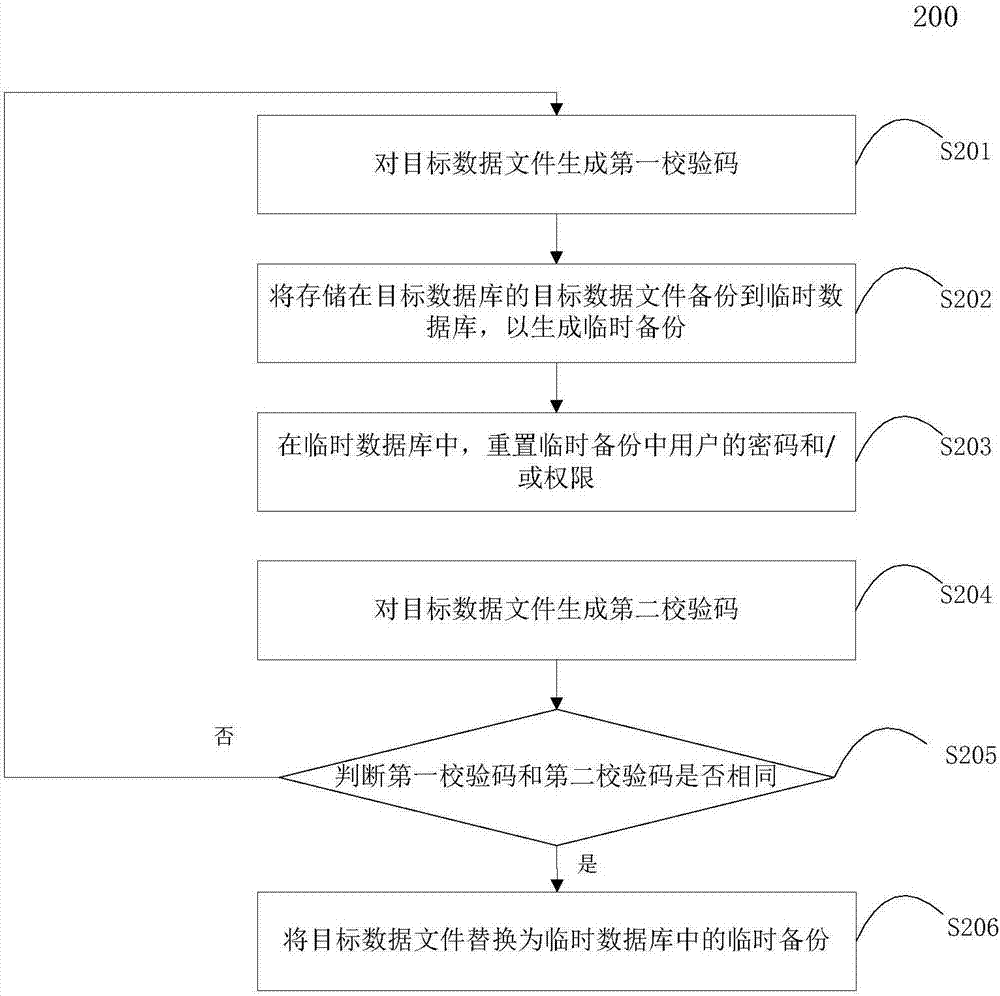
[0041] Although the execution speed of the database management method 100 of the present invention is relatively fast, and the probability of the user actively changing the user table is relatively low, but during the execution of the method 100, the user operates the user table, making the user table Situations where data has changed.
[0042] figure 2 is a flow chart of the database management method 200 according to the embodiment of the present invention.
[0043] Such as figure 2 As shown, in method 200, steps S202, S203, and S206 are respectively the same as steps S101, S102, and S103 of method 100, and for brevity, detailed descriptions are omitted here.
[0044] In step S201, a first check code is generated for the target data file.
[0045] As an example, an algorithm that can realize data integrity verification, such as a hash function, can be used to calculate the user table in the target database that needs to be reset, and correspondingly generate a check cod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com