A network access control method and system for a securely controlled terminal
A controlled terminal and control method technology, applied in transmission systems, digital transmission systems, network interconnection, etc., can solve problems such as high maintenance and debugging costs, multiple debugging and maintenance interfaces, and inconvenience for maintenance and debugging personnel, so as to improve work efficiency and Convenience, reducing the number of reserved interfaces, improving convenience and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in more detail below in conjunction with the accompanying drawings and embodiments.
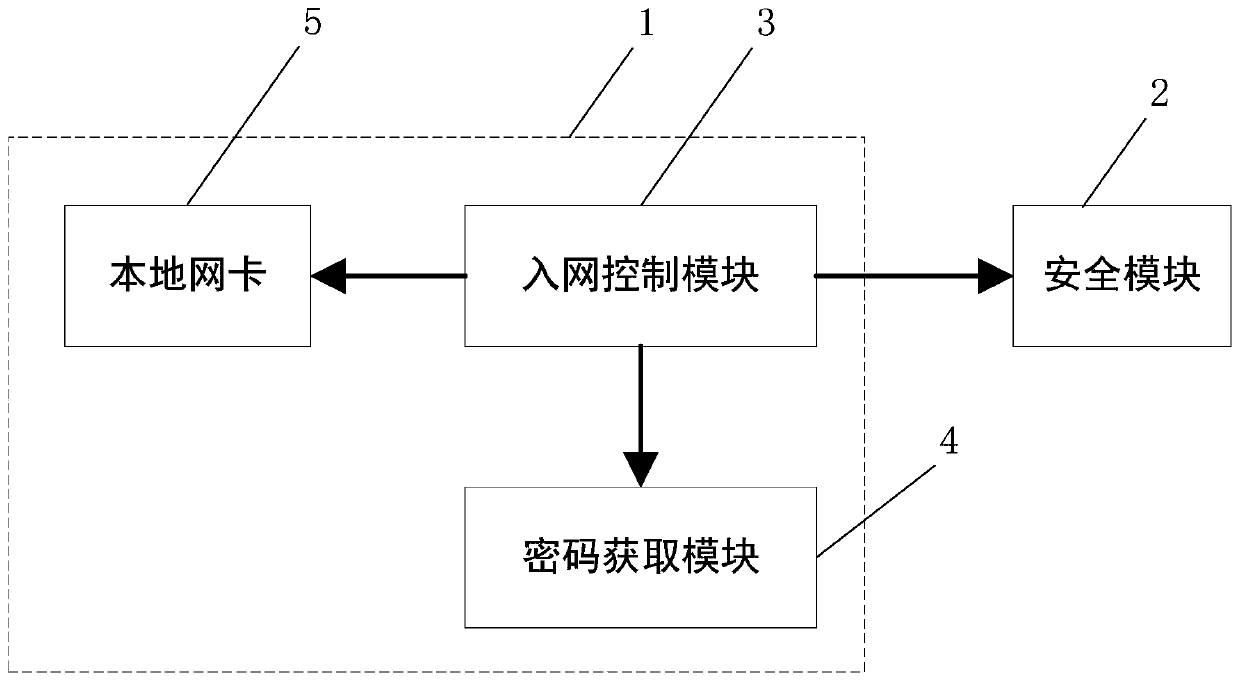
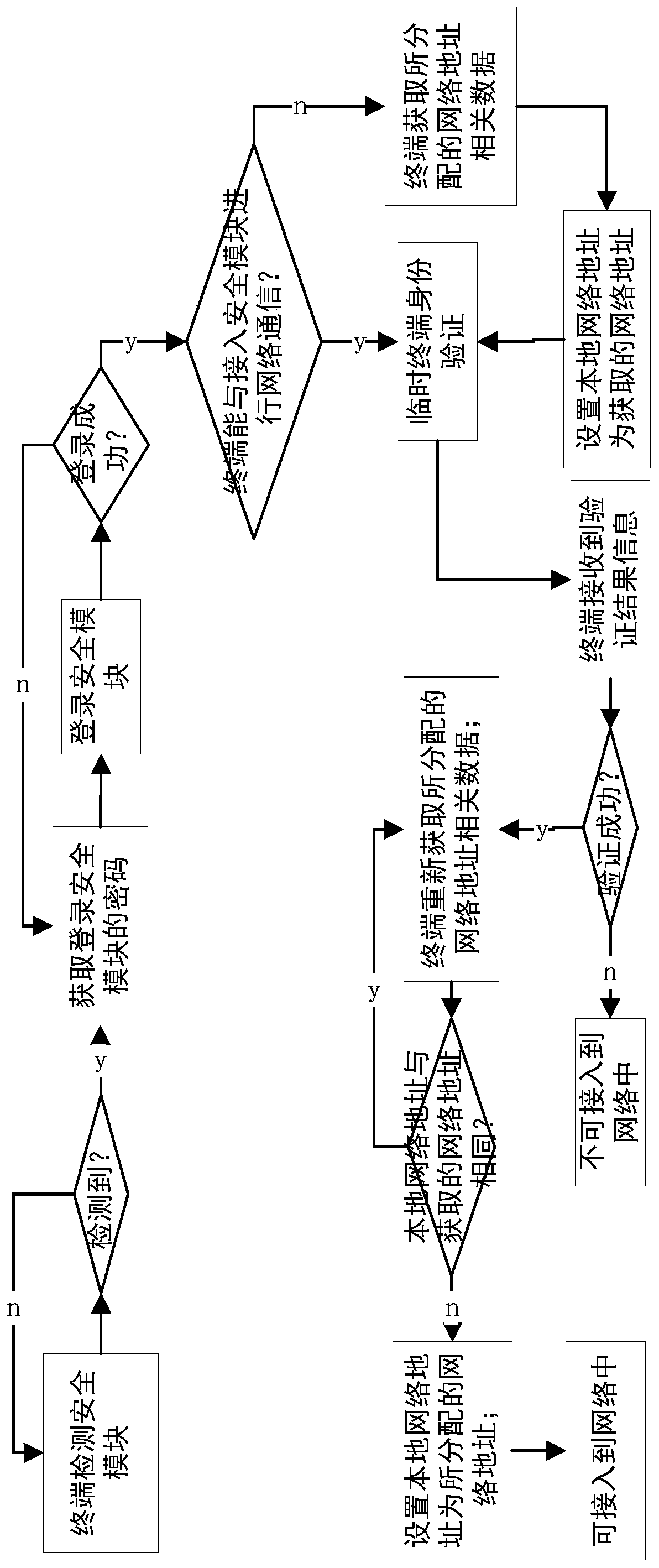
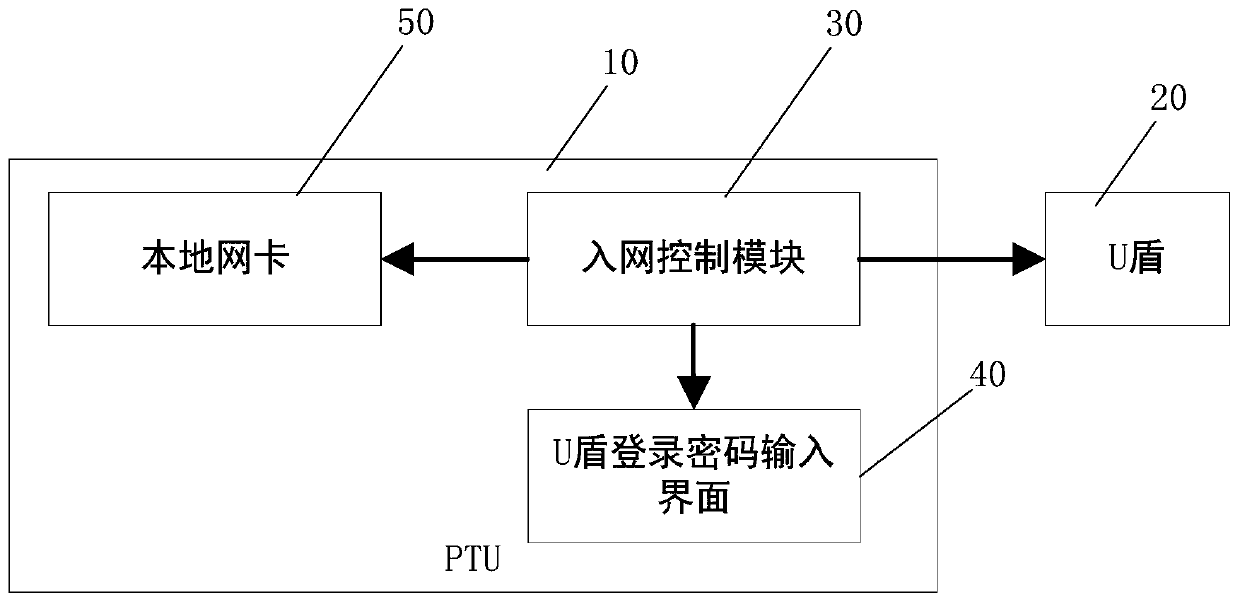
[0023] The invention discloses a network access control method of a security-controlled terminal, which combines figure 1 and figure 2 As shown, the method is implemented based on a system, the system includes a terminal device 1 and a security module 2, and the method includes the following steps:
[0024] Step S1, the terminal device 1 logs into the security module 2;
[0025] Step S2, the terminal device 1 establishes network communication with the security module 2;
[0026] Step S3, the security module 2 performs identity verification on the terminal device 1, and executes step S4 after the verification is successful;
[0027] Step S4, the terminal device 1 obtains a network address, and sets the local network address as the obtained network address;
[0028] Step S5, the terminal device 1 is connected to the network.
[0029] In the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com