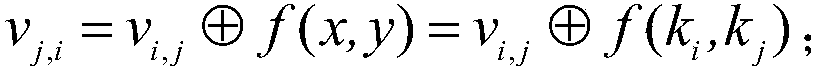AES mask encryption method resisting high order power consumption analysis
A technology of power consumption analysis and encryption method, which is applied in the field of information security, can solve the problems that the AES algorithm cannot resist high-order differential power consumption analysis, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The following are specific embodiments of the present invention, and further clearly and completely describe the technical solutions of the present invention in conjunction with the accompanying drawings.
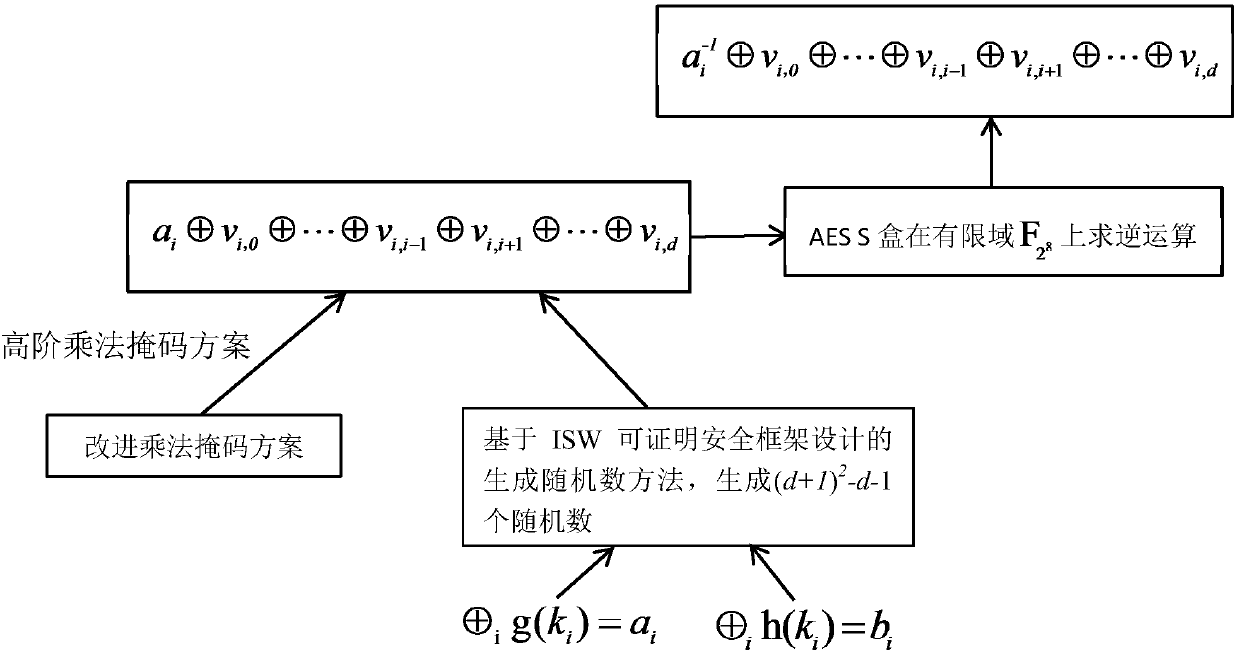
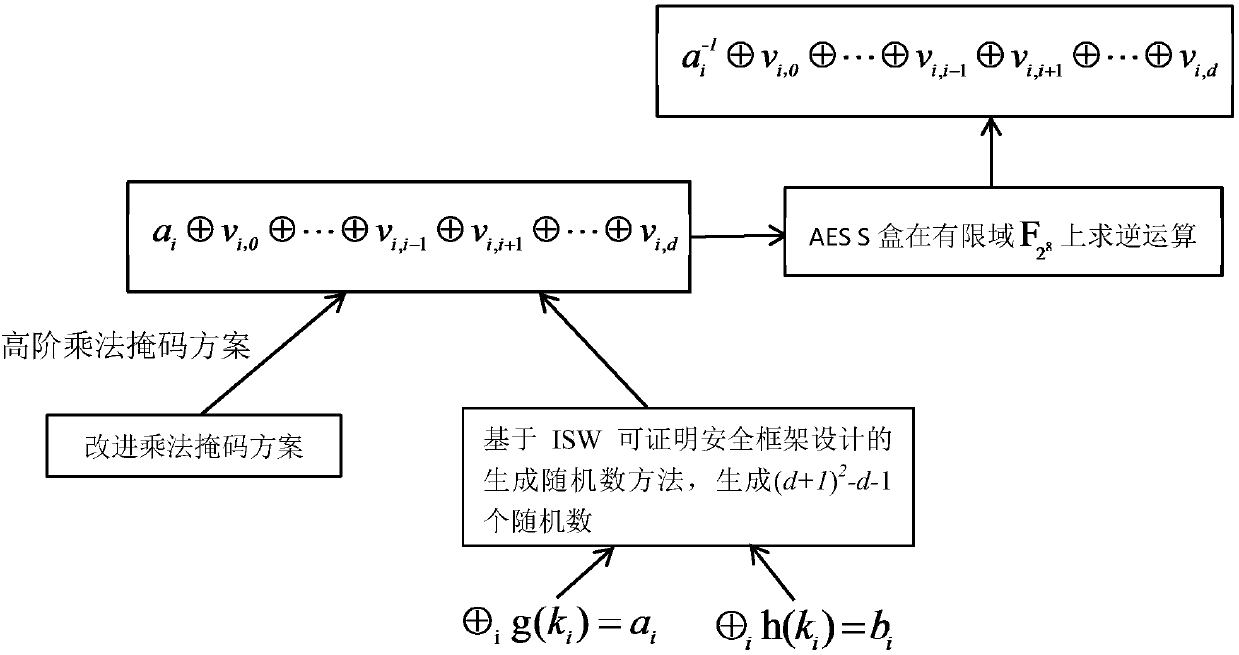
[0033] Most of the AES symmetric encryption algorithm is a linear operation, and the energy consumption is relatively uniform, but the S-box inversion nonlinear operation hardware consumes a lot of energy, which is prone to leakage of data information. Based on the Ishai-Sahai-Wagner provable security framework, the invention solves the security problem of zero-value attack in the AES algorithm protected by the one-factor multiplication mask scheme, and further designs a high-order mask scheme for protecting the AES S-box inverse nonlinear operation. It mainly includes the following steps (involving specific values, all expressed in hexadecimal form):
[0034] Step 1, initialization of higher-order masking schemes for S-box inverse nonlinear operations:
[0035] (1)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com