Application software security vulnerability detection method and system
A technology for application software and vulnerability detection, applied in the field of data security, can solve the problems of low efficiency of security vulnerability detection, achieve good security detection, no false positives, and improve the efficiency of security vulnerability detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
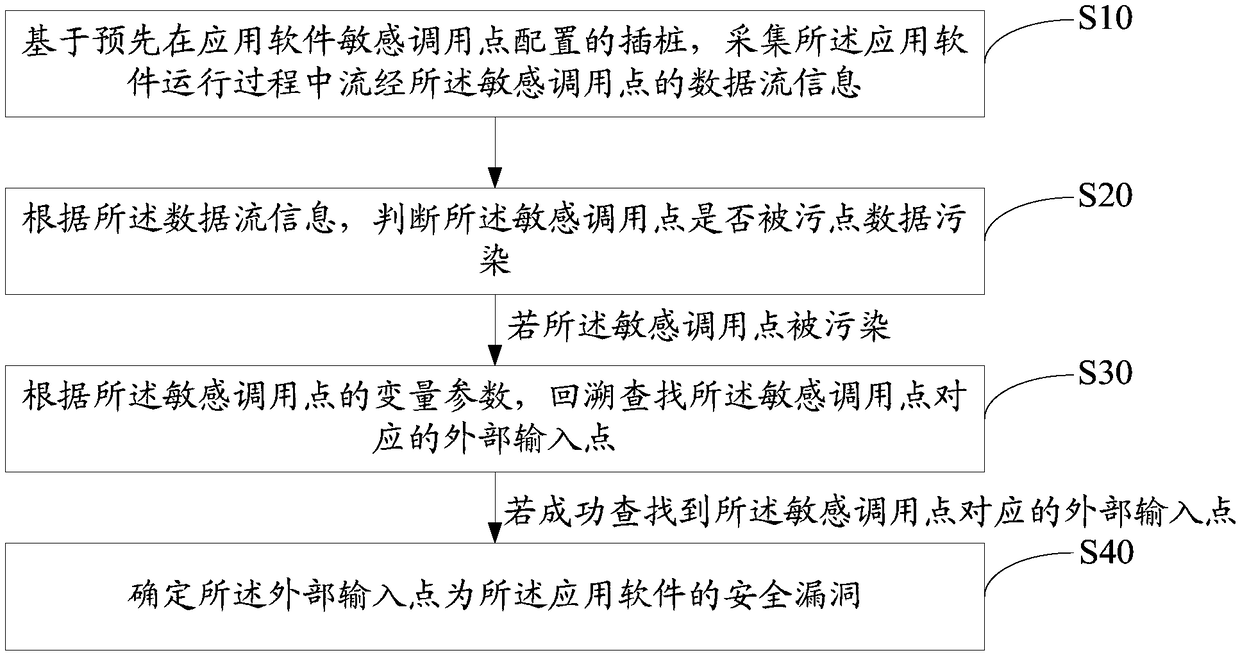
[0145] Further, refer to Figure 7 The second embodiment of the application software security vulnerability detection system of the present invention provides an application software security vulnerability detection system. Based on the above-mentioned first embodiment of the application software security vulnerability detection system of the present invention, the application software security vulnerability detection system further includes:
[0146] The taint module 50 is configured to input taint data at each external input point of the application software when the application software is running.
[0147] When the sensitive call points of the application software have been configured for instrumentation and start running, or during the running of the application software, the taint module 50 inputs taint data with pollution labels into the application software through each external input point of the application software .
[0148] After the tainted data is input into th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com