An industrial control vulnerability mining method based on protocol state graph depth traversal
A technology of protocol status and depth traversal, applied in transmission systems, electrical components, etc., can solve problems such as difficult to simulate, difficult to achieve better results, high real-time performance of the system, and achieve the effect of poor effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
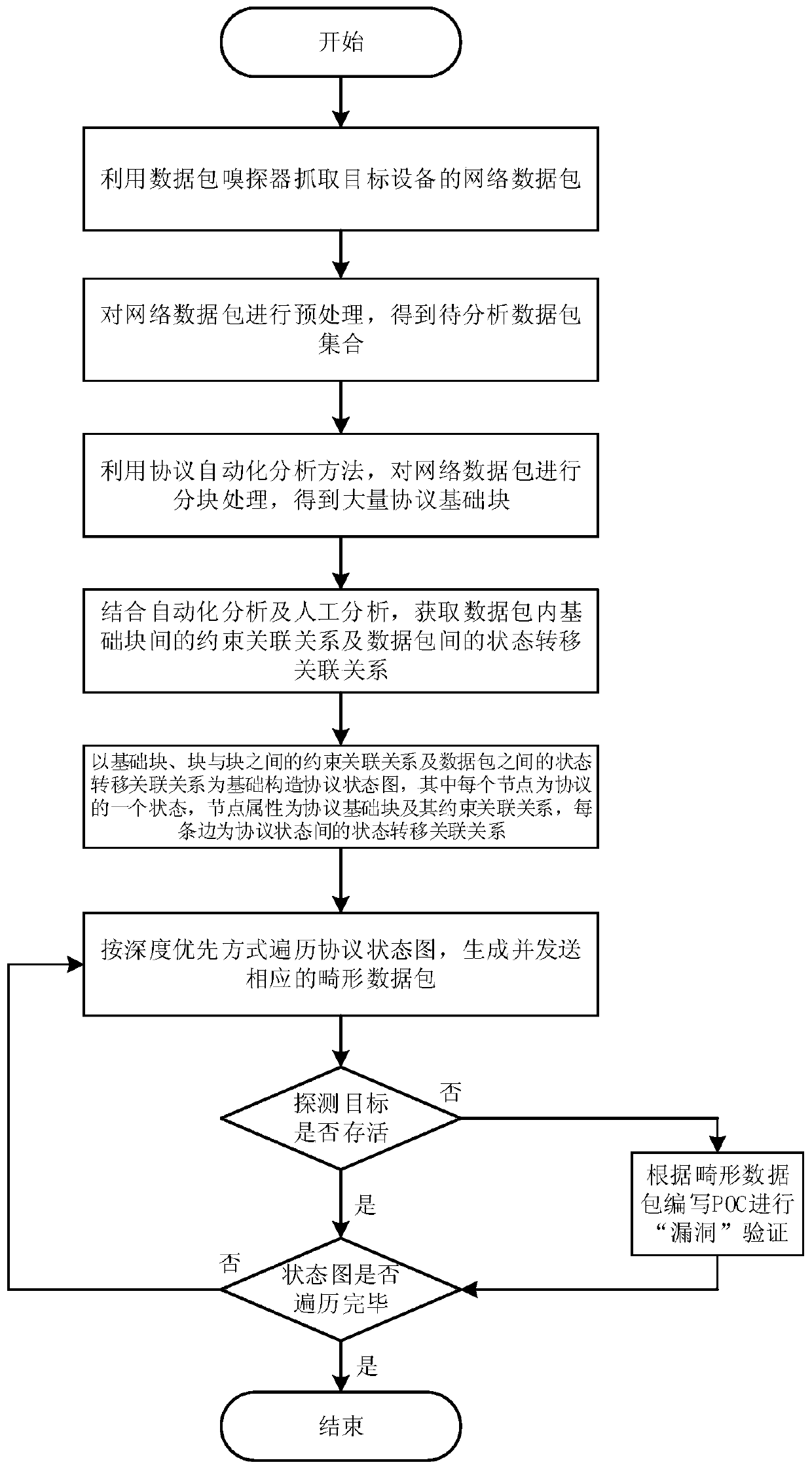
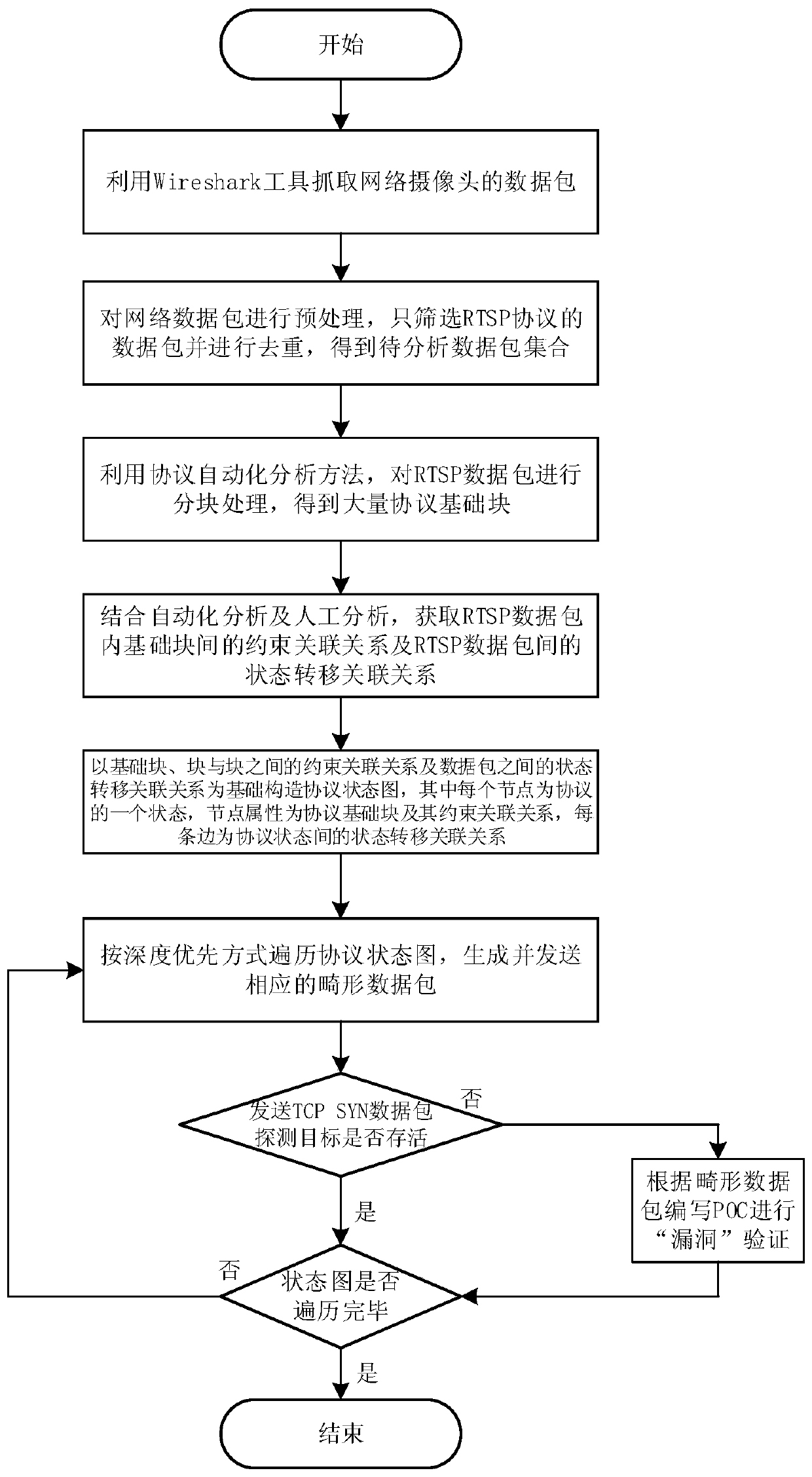
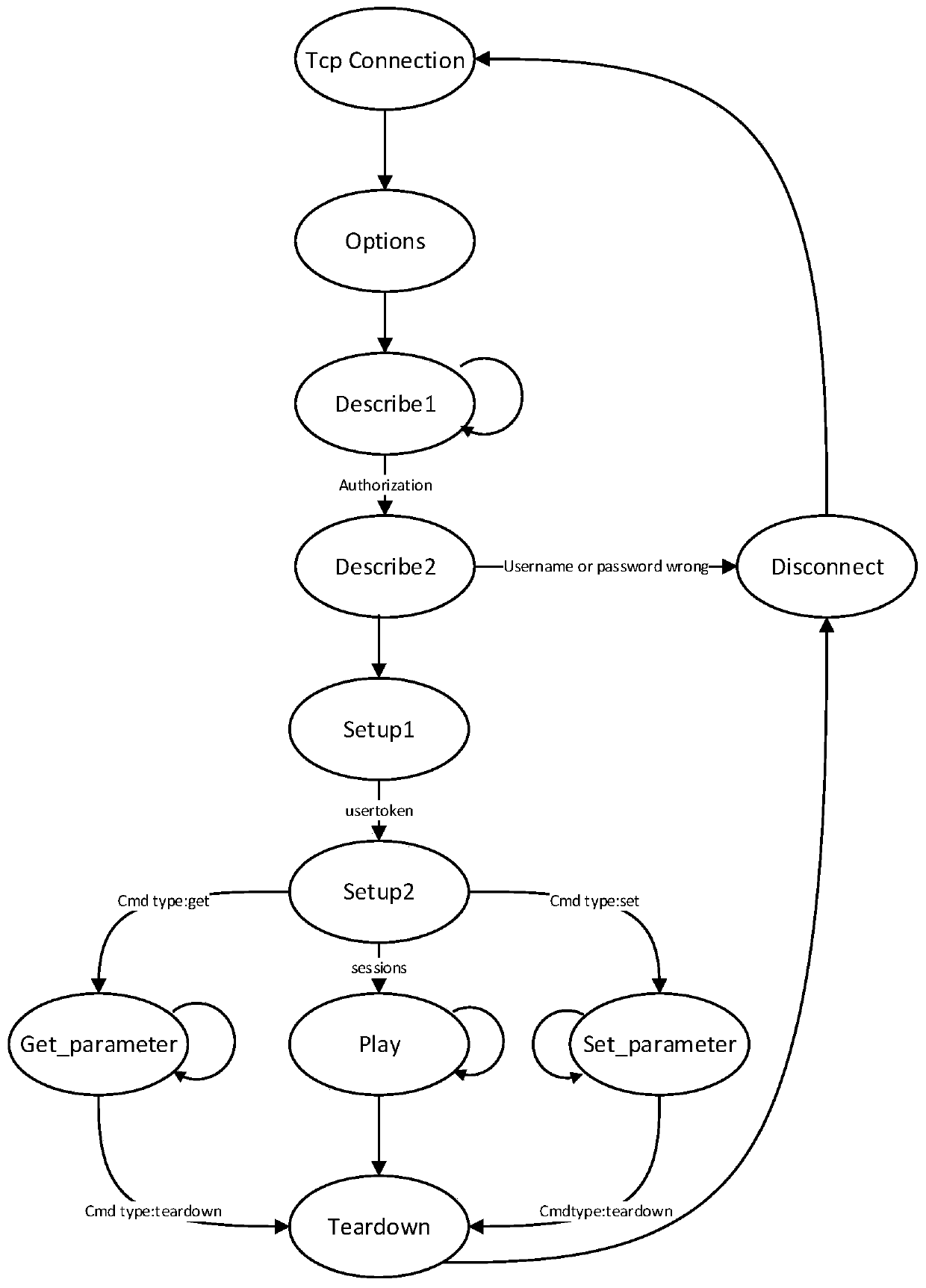
[0029] This embodiment relates to a method for mining industrial control vulnerabilities based on in-depth traversal of protocol state diagrams, mainly obtaining a set of data packets to be analyzed by obtaining network data packets of a target device and performing preprocessing, and dividing the data packets in the set into blocks. Combining automatic analysis and manual analysis to obtain the constraint relationship between the basic blocks in the data packet and the state transition relationship between the data packets, and construct the protocol state diagram based on this. Traverse the protocol graph in a depth-first manner to perform fuzz tests, and detect whether the target is alive, so as to effectively dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com