A Vector Map Integrity Authentication Method
A vector map, authentication method technology, applied in the field of geographic information science and information hiding, which can solve the problems of insufficient accurate positioning of tampered areas, inability to accurately locate tampered areas, and inability to accurately locate all areas.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] Below in conjunction with accompanying drawing and example technical solution of the present invention is described further:
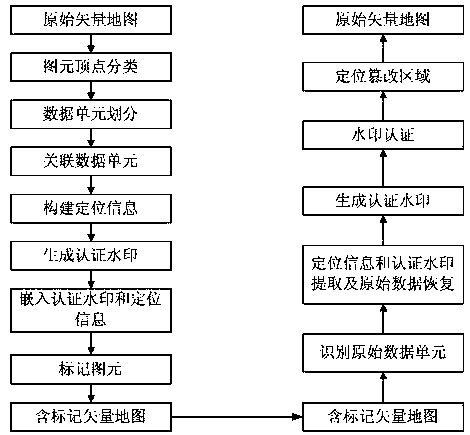
[0071] Such as figure 1 As shown, a flow chart of a vector map integrity authentication method of the present invention, the method is generally divided into two aspects: A, vector map watermark embedding algorithm; B, vector map watermark authentication algorithm.
[0072] A. Vector map watermark embedding algorithm, the steps are as follows:
[0073] (1) Primitive vertex classification;
[0074] The vertices of vector map (line or area) primitives are divided into two categories: marked vertices and non-marked vertices. The marked vertex is used to mark the data unit where the graphic element is located, and the non-marked vertex can embed authentication watermark and positioning information. Treats the first and last vertices of each line primitive as its flagged vertices and the others as non-flagged vertices; treats the second and penult...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com