User password soft safety protection method based on behavior identification
A user password and security protection technology, which is applied in the field of user password soft security protection mechanism based on behavior recognition, can solve problems such as personal information leakage, property loss, loss, etc., achieve good application prospects and improve the effect of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
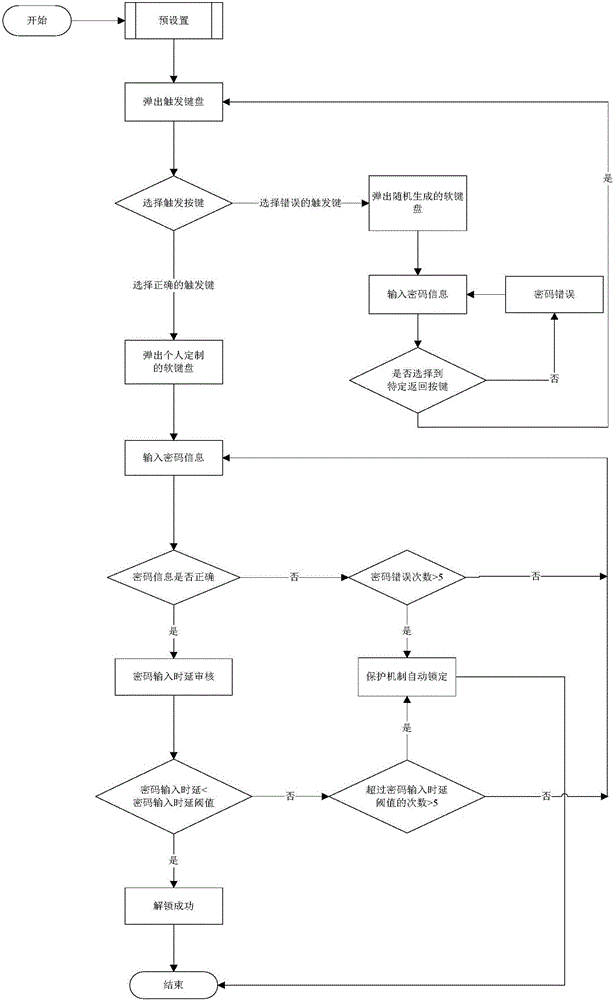
[0013] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings. figure 1 It is a flowchart of the present invention.
[0014] A. User's preset:
[0015] Step (1). The user sets the trigger button, or it can be set as a custom password string, which is set according to personal habits. The setting of the password is similar to the setting of the general password, for example, it can be "#", "123abc" and so on.
[0016] Step (2). The user sets the personal soft keyboard. The setting content includes the information of each key, among which Chinese characters, numbers, English and some common symbols can be set as key information, and the personal soft keyboard is customized.
[0017] Step (3). The user sets a specific return button on the soft keyboard. Wherein, the specific return key is generally a specific key, and it is not recommended to have multiple keys simultaneously serving as the specific retur...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap