Method and system for cleaning SYN FLOOD attack
A technology for cleaning systems and messages, which is applied in the field of computer networks, can solve problems such as low efficiency, missing traffic, complex deployment of network architecture, etc., and achieve the effect of preventing counterfeiting of legitimate traffic and reducing pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
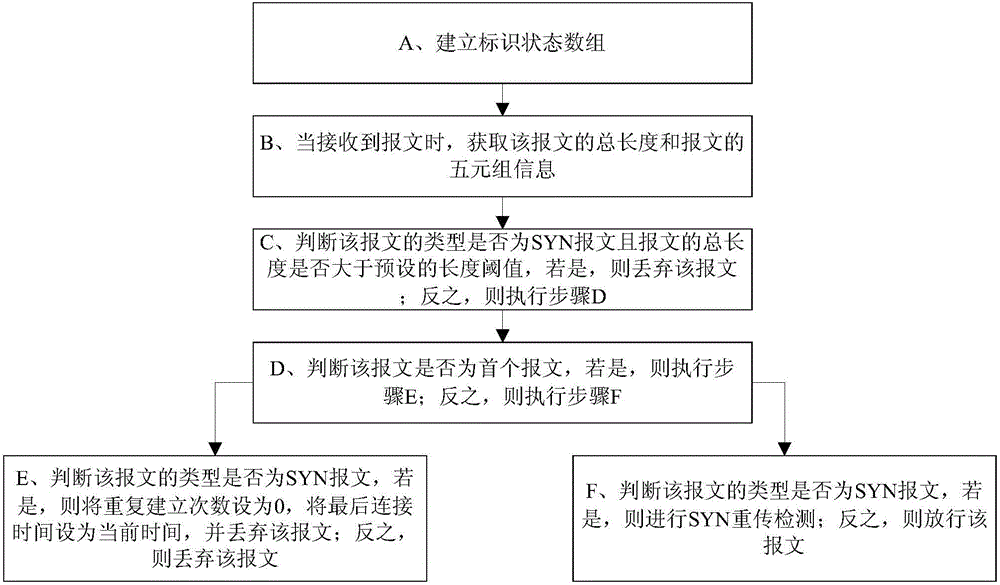
[0047] refer to figure 1 , the cleaning method of a kind of SYN FLOOD attack of the present invention, comprises the following steps:
[0048] A. Establish an identification status array;
[0049] B. When a message is received, obtain the total length of the message and the quintuple information of the message;
[0050] C, judge whether the type of the message is a SYN message and whether the total length of the message is greater than a preset length threshold, if so, discard the message; otherwise, perform step D;
[0051] D. Determine whether the message is the first message, if so, execute step E; otherwise, execute step F;
[0052] E, judge whether the type of this message is a SYN message, if so, then the number of times of repeated establishment is set to 0, the last connection time is set as the current time, and discards this message; Otherwise, then discards this message;
[0053] F. Determine whether the type of the message is a SYN message, if so, perform SYN re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com