Unlocking method, and mobile terminal
A mobile terminal, unlocking technology, applied in the field of communication, can solve the problems of insufficiency, lack of unlocking function, application depth mining, etc., and achieve the effect of increasing the probability of recovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
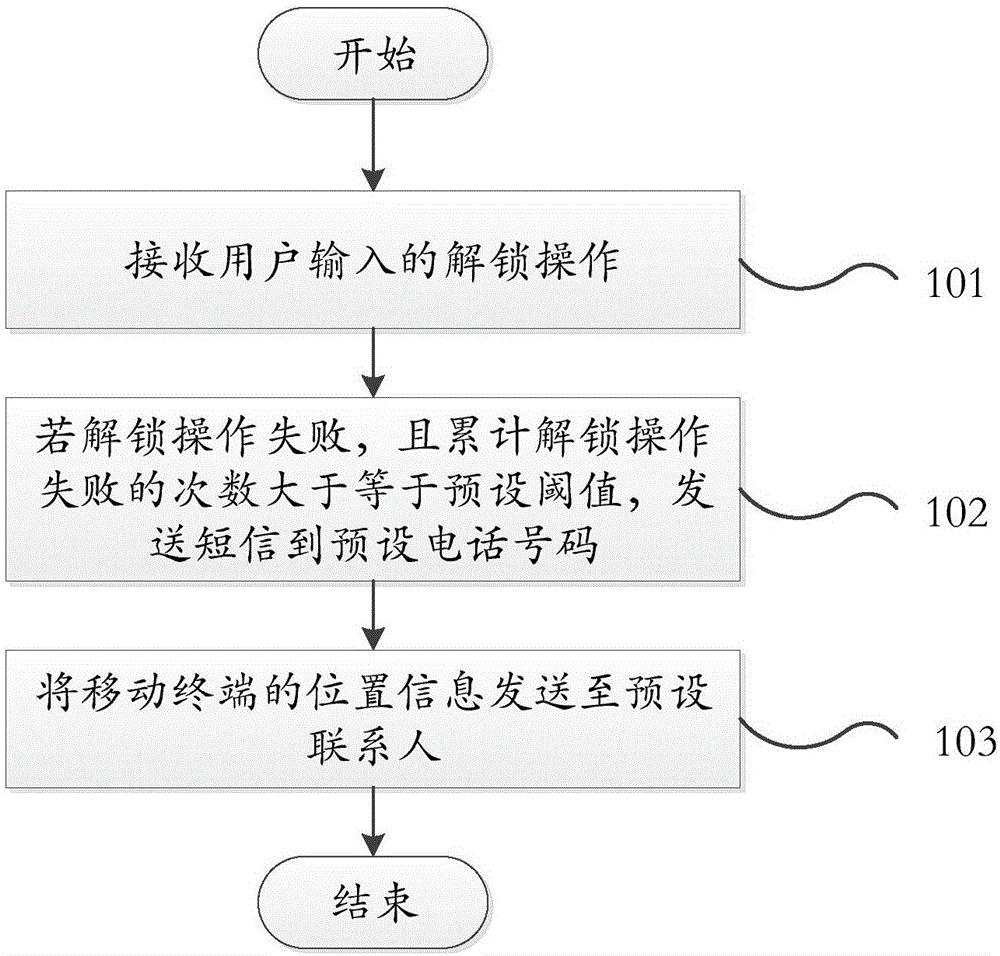
[0021] An unlocking method provided by the present invention, such as figure 1 shown, including the following steps:
[0022] Step 101 receives an unlocking operation input by a user.
[0023] In this step, when the user starts the unlocking operation, the unlocking operation input by the user is received.
[0024] The unlocking operation may include password unlocking, pattern unlocking, fingerprint unlocking and other unlocking operation modes that are not limited.
[0025] Step 102: If the unlocking operation fails, and the cumulative number of times the unlocking operation fails is greater than or equal to a preset threshold, send a short message to the preset phone number.
[0026] In this step, on the premise that the unlocking operation fails, it is further judged whether the cumulative number of unsuccessful unlocking operations is greater than or equal to a preset threshold, so as to determine the identity characteristics of the current user of the mobile phone, so ...
no. 2 example
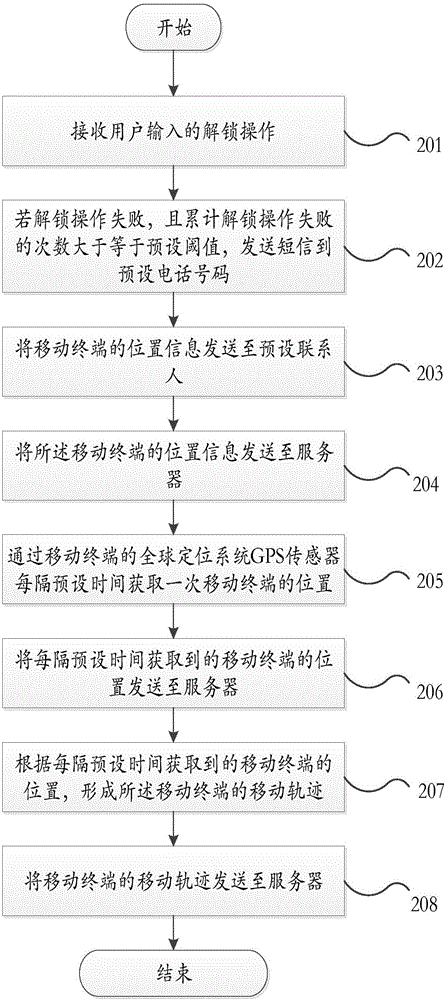
[0031] An unlocking method provided by the present invention, such as figure 2 shown, including the following steps:
[0032] Step 201, receiving an unlocking operation input by a user.
[0033] In this step, when the user starts the unlocking operation, the unlocking operation input by the user is received.
[0034] The unlocking operation may include password unlocking, pattern unlocking, fingerprint unlocking and other unlocking operation modes that are not limited.
[0035] Step 202, if the unlocking operation fails, and the cumulative number of times of the unlocking operation failure is greater than or equal to a preset threshold, send a short message to the preset phone number.
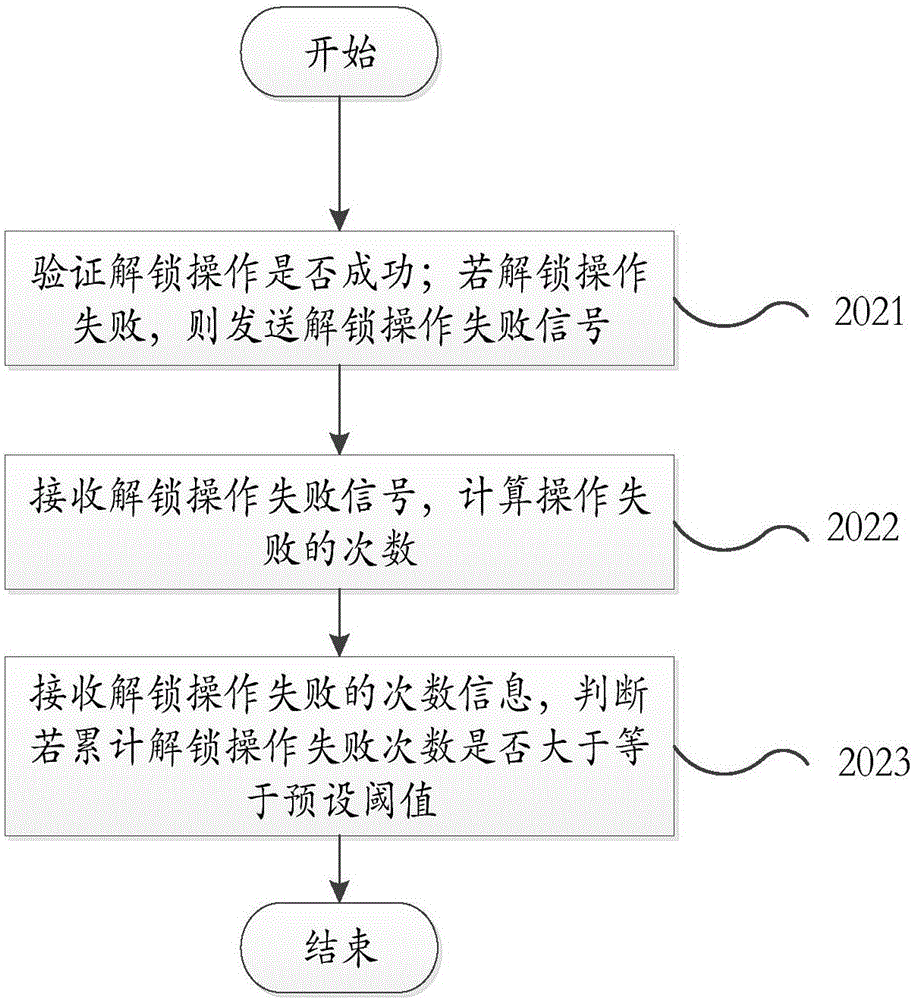
[0036] In this step, refer to Figure 2a , which specifically includes the following steps: Step 2021, verify whether the unlocking operation is successful; if the unlocking operation fails, send an unlocking operation failure signal. Specifically, after receiving the unlocking operation i...
no. 3 example
[0052] refer to image 3 , is a structural diagram of a mobile terminal according to an embodiment of the present invention, and the mobile terminal 300 includes:
[0053] The receiving module 301 is configured to receive an unlocking operation input by a user.
[0054] The judging module 302 is configured to receive the unlocking operation result of the receiving module 301 . If the unlocking operation fails, and the cumulative number of failed unlocking operations is greater than or equal to the preset threshold, send a short message to the preset phone number.
[0055] The sending module 303 is configured to send the location information of the mobile terminal to the preset contact after sending the short message to the preset phone number.
[0056] The mobile terminal according to the embodiment of the present invention receives the unlocking operation input by the user through the above-mentioned module, and judges that the current user is an illegal user if the unlocki...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com