Security Protection System Based on Behavior Fingerprint
A security protection and behavior technology, applied in computer security devices, instruments, digital data authentication, etc., can solve the problems that single-dimensional data cannot effectively describe user behavior characteristics, poor terminal adaptability, and poor model reliability, etc. Reduce custodial costs and risk of key loss, ensure security and normal operation, and reduce the effect of precision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
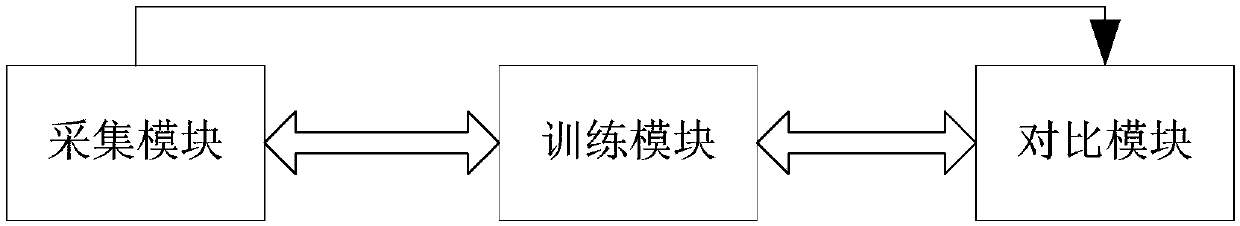
[0015] Such as figure 1 As shown, the present embodiment includes: a collection module, a training module and a comparison module, wherein: the collection module collects the user's behavioral fingerprint information and transmits it to the training module, and the training module uses SVM modeling to obtain the judgment threshold of the behavioral fingerprint information, and the comparison module Receive new fingerprint information from the collection module and compare it with the judgment threshold to identify the user.
[0016] The behavioral fingerprint information includes: abscissa x of the touch point, y coordinate of the touch point y, pressing duration t, pressing area s, angular acceleration, and acceleration g. The angular acceleration includes: X-axis angular acceleration α, Y-axis angular acceleration β and Z-axis angular acceleration γ.
[0017] The acquisition module is connected with a touch screen for obtaining the abscissa x of the touch point, the y coord...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com