Significance area protection method based on encryption image with visual meaning
A technology for encrypted image and area protection, applied in digital image processing and information security intersection, multimedia field, can solve the problems of encrypted image attacker attack, information leakage, feature encryption algorithm can not effectively protect the image salient area, etc., to achieve key data protective effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
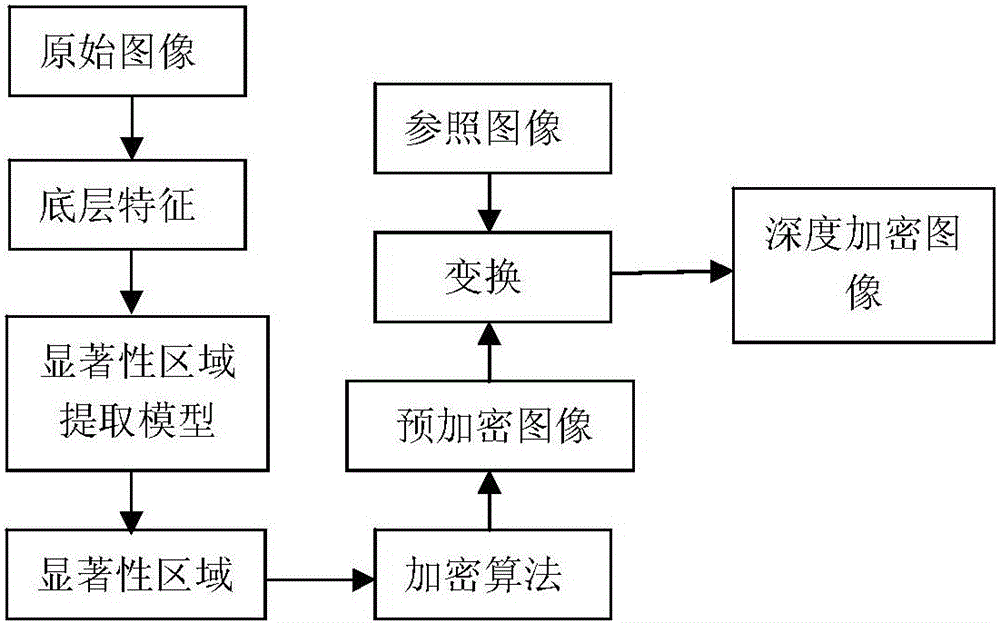
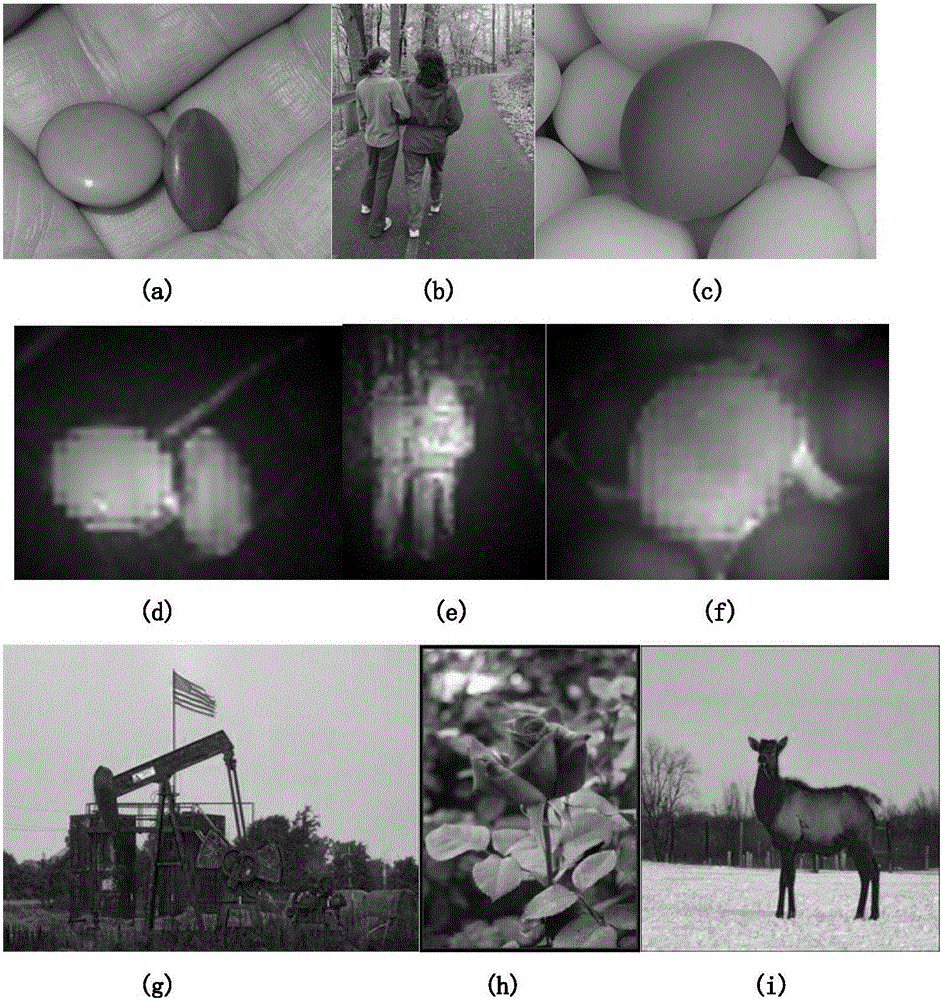
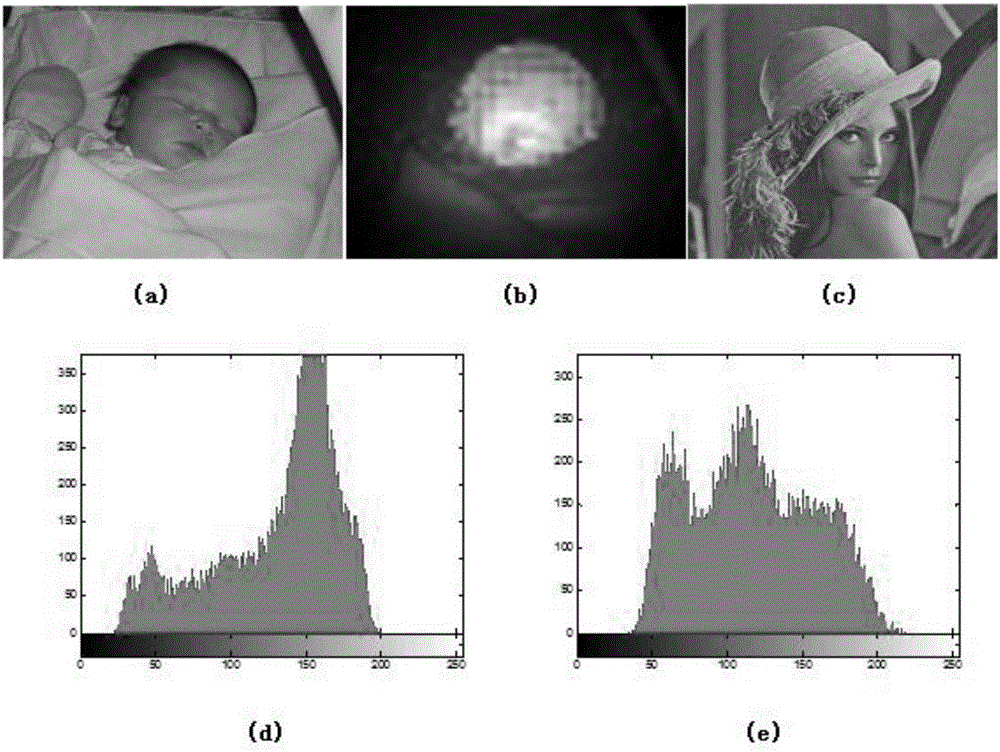
[0018] Embodiment 1: The salient regions mentioned in the present invention can be obtained in the compressed domain or in the uncompressed domain. like figure 1 As shown, the salient region of the image is first extracted, and the underlying features of the image are extracted according to the characteristics of the underlying features of human visual perception, such as color, texture, brightness, shape features, etc., and the feature fusion algorithm is constructed using image processing techniques to obtain salient area of sexuality. Let's take the method of extracting salient regions in the compressed domain as an example, for the original image: figure 2 (a), figure 2 (b), figure 2 (c), first calculate the feature difference between DCT blocks Where k=1,2,3 represent brightness and color features, Ω k ={I,C rg ,C by}; Then calculate the texture difference between block i and block j where 4 represents the texture feature, T i and T j , denote the texture...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com