Method for realizing control and leakage prevention of data out of service system
A data control and business system technology, applied in the field of data security, can solve problems such as inconvenient daily work, achieve the effect of easy office and increased security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
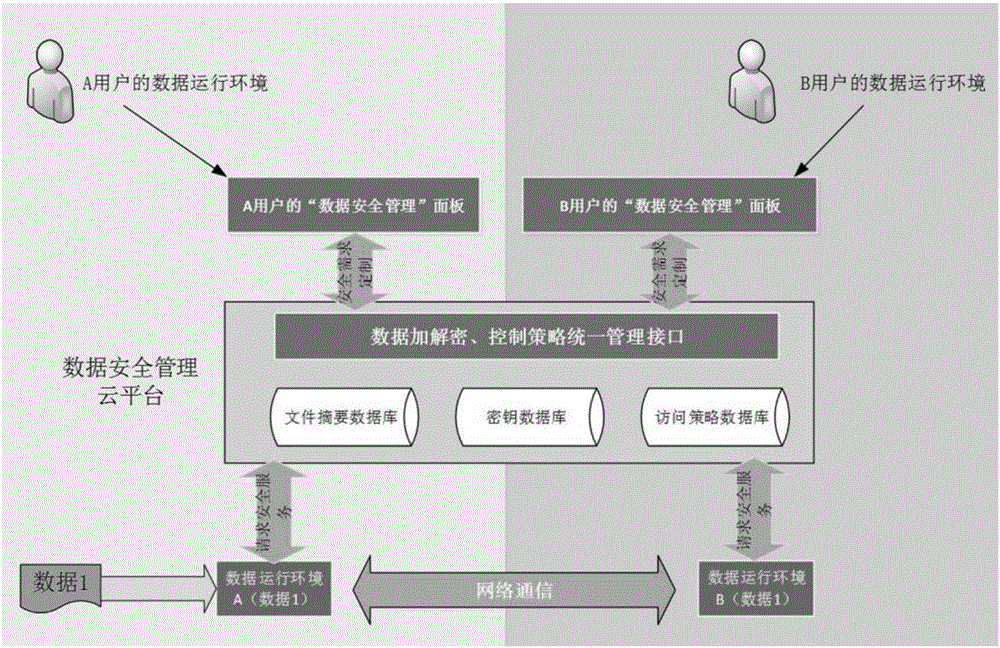
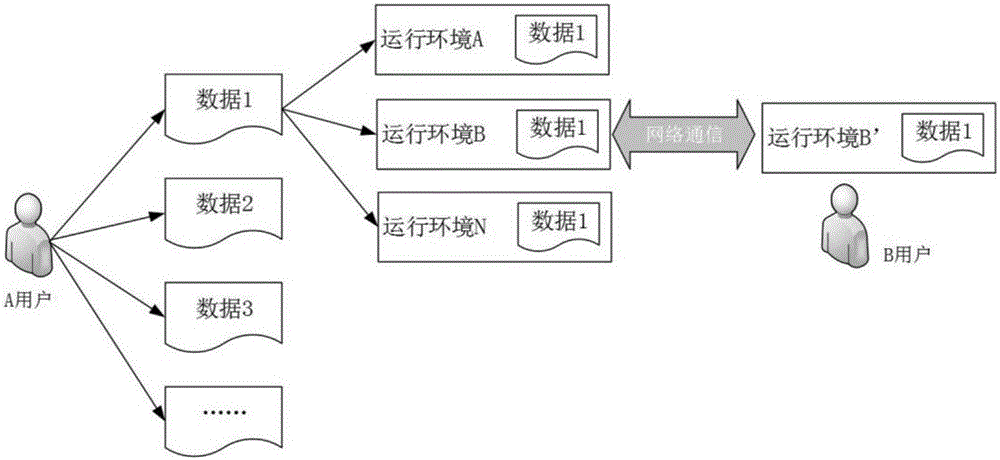
[0042] During the work process, the same data of the same user can run in different client terminals, and different data can also run in the same client terminal. When the data management user sends a piece of data that needs to be protected to the data receiving user through his client, the data management user's client will first send the "data identifier" of the local data to be protected to the data security management cloud platform and request security protection. Services, including the encryption key and control strategy of the data to be protected, etc., the data security management cloud platform will not store the local data of the data sending user. The security management cloud platform generates an encryption key and a decryption key according to the "data identifier" of the received local data; the "data identifier" of each piece of local data corresponds to a unique encryption key and decryption key. The security management cloud platform generates a control st...
Embodiment 2
[0045]In this embodiment, on the basis of Embodiment 1, all operation records of the data security management cloud platform, including time, identity, operation, location, etc., will be saved to the data security management cloud platform accordingly, and aggregated for monitoring by the management panel analyze. In addition, the administrator can modify the control policy through the management panel to determine the period of use of the key. In this way, when different users use the same data, they can have different operation permissions on this data, and the use period of the data will also be different. For example: for the same piece of data, the administrator can grant user A the permission to open, edit, copy, and share by modifying the control policy, while only granting user B the permission to open and edit. At this time, the operation permissions of different user terminals on the data are It will be different; in addition, when the data usage period of the data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com