Identification method and device
An identification method and technology to be identified, applied in the field of information identification, can solve problems such as time-consuming
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
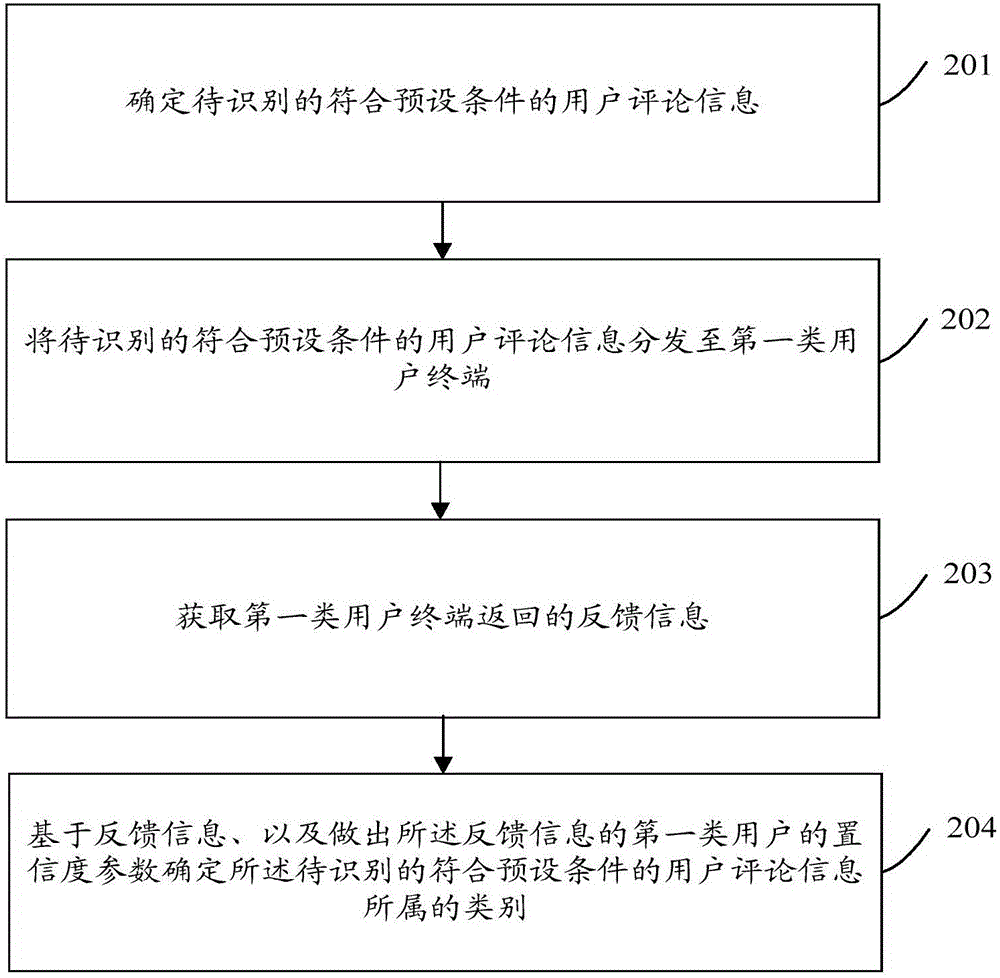
[0102] An embodiment of the present invention provides an identification method, which is applied to the server side, such as figure 2 Said, said method comprises:
[0103] Step 201. Determine user comment information that meets preset conditions to be identified.
[0104] Here, the user comment information mainly refers to comment information written by users on online platforms such as online education platforms, online business platforms, and online game platforms.
[0105] Wherein, the user comment information meeting the preset condition refers to suspicious user comment information; the preset condition means that the category of the user comment information cannot be clearly identified. The server needs to further judge the user comment information meeting the preset condition, so as to determine whether the user comment information meeting the preset condition is valid comment information or invalid comment information.
[0106] Wherein, the invalid comment informat...
Embodiment 2
[0194] Based on the technical solution described in Embodiment 1, a schematic workflow diagram of a recognition system is given, as shown in Figure 6 As shown, the identification system mainly includes: a series monitoring system, a bypass monitoring system, a suspicious comment distribution system, a confidence evaluation system, and a scoring system;
[0195]Wherein, the serial monitoring system is responsible for frequency control, account information detection, and content detection.
[0196] The series monitoring system includes: a frequency control module, an account information detection module, and a content detection module; specifically,
[0197] The frequency control module is responsible for reading the frequency configuration information of the series monitoring system. For example, the frequency configuration information is that a user account is allowed to comment 2 times within 1 minute, and the frequency of user comments is controlled according to the IP addr...
Embodiment 3
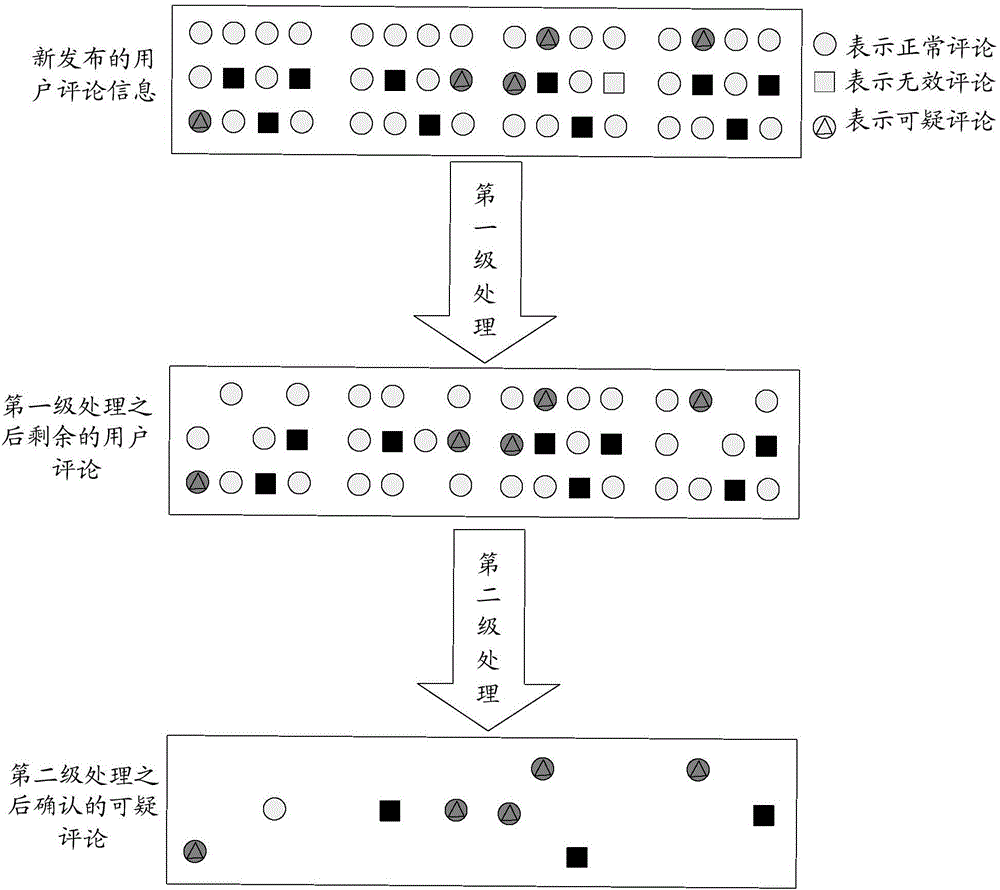
[0213] Figure 7 A schematic diagram showing a hardware entity of parties identifying suspicious comments, Figure 7 It includes: servers 1-4, terminal devices 1-N, and terminal devices 1-N exchange information with servers through wired or wireless networks. Terminal devices include mobile phones, desktops, PCs, and all-in-one machines. Wherein, the online platform application is installed in the terminal device, adopting the embodiment of the present invention, based on Figure 7 In the system shown, the server 1 receives a large number of user comments, performs first-level processing on the massive user comments, and then sends the remaining user comments to the server 2 after the first-level detection processing, and the server 2 performs After the first-level detection process, the remaining user comments are subjected to a second-level detection process, and the remaining user comments after the second-level detection process are sent to the server 3, and the server 3 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com