A Method of Using Safe Keyboard to Conduct Network Transactions
A technology for secure keyboards and network transactions, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve problems such as attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
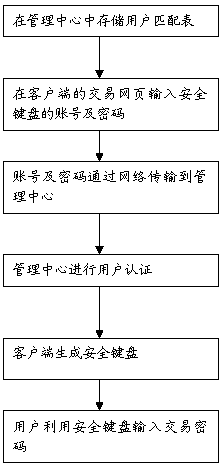
[0016] The design idea of the present invention is: the present invention develops a method of using a security keyboard for network transactions in the sensitive application fields of network transactions such as financial applications and e-commerce applications. The center conducts login authentication, the keyboard pattern is randomly generated, and the password and actual password mapping adopts a one-to-many randomized mapping form. By adopting the present invention, the drawbacks in the prior art that only need to log in to the transaction webpage to conduct transactions are avoided, and only legitimate users who pass through the security keyboard can enter transaction passwords, thereby further ensuring the transaction security of users.
[0017] The technical solution is described in detail below.
[0018] The realization basis of the method of the present invention is: the safety keyboard control and the safety management service module arranged on the client end, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com