Method for defending black hole attack based on active detection in wireless sensor network
A wireless sensor, black hole attack technology, applied in the field of black hole attack defense, can solve the problems of low black hole attack resistance, short network life, unclear node trust, etc., to improve energy efficiency, improve security, and improve network safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with examples and accompanying drawings.
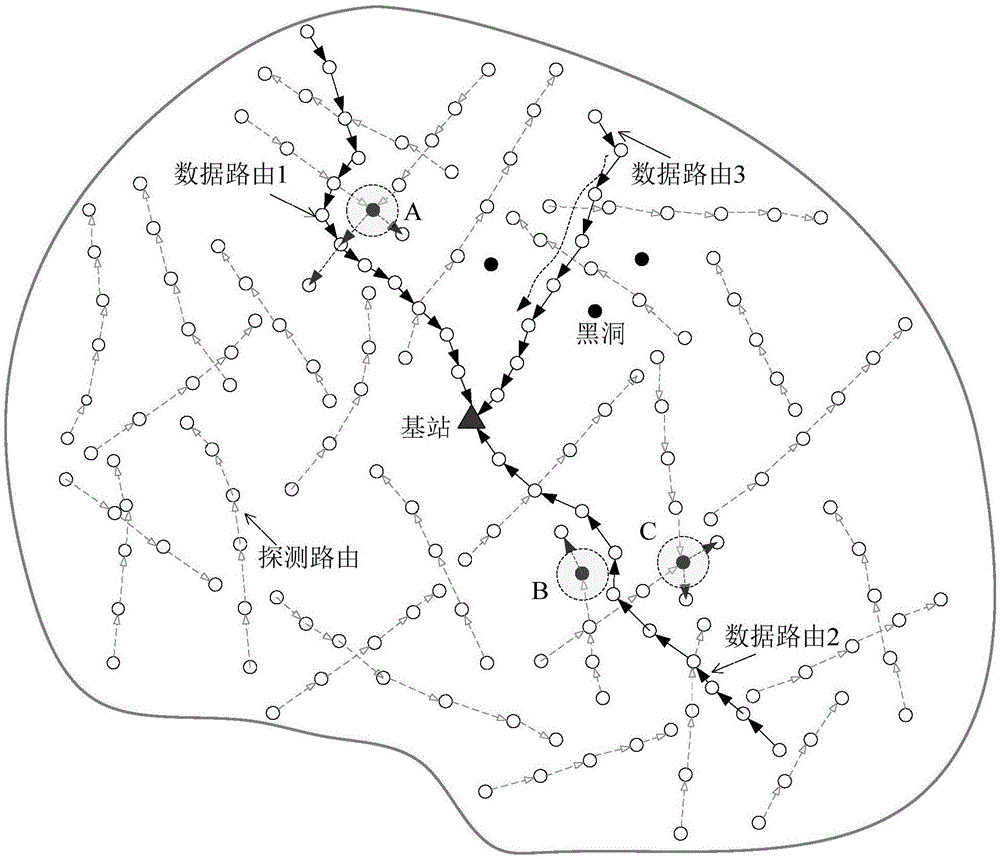
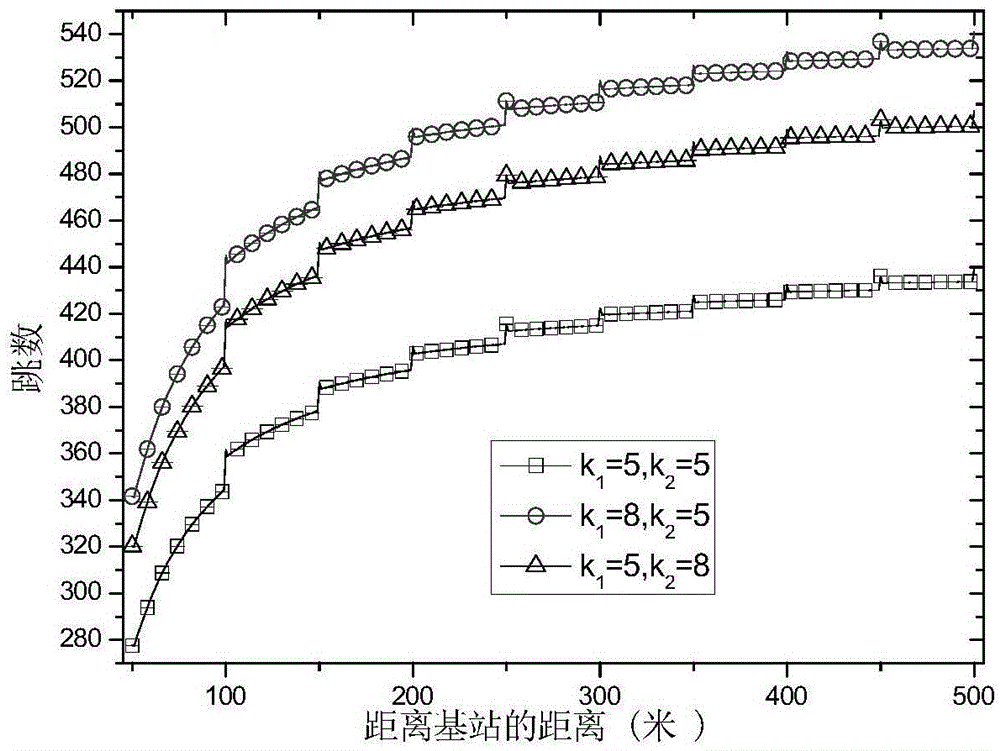
[0033] A method for resisting black hole attacks based on active detection in wireless sensor networks, such as figure 1 As shown in , different numbers of detection routes are generated according to the energy abundance of the sensor network;
[0034] Initiate more detection routes for areas with more residual energy, and initiate fewer detection routes for areas with less residual energy, and do not initiate detection routes for areas near the base station with no energy remaining;
[0035]In the process of detecting routing, the node records whether it has been attacked by a black hole, and if it has been attacked by a black hole, its trust degree will be reduced, and the trust degree of the successful routing node will be increased;
[0036] During data routing, when a node looks for the next hop, it selects a node with a high degree of trust as the next ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com