Method and device for verifying request data
A technology for verifying requests and data, applied in the field of communication applications, can solve the problems of illegal TV client APP use, no solution proposed, and TV client unable to supervise and supervise.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0020] According to an embodiment of the present invention, a method embodiment of a method for verifying request data is provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, Also, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
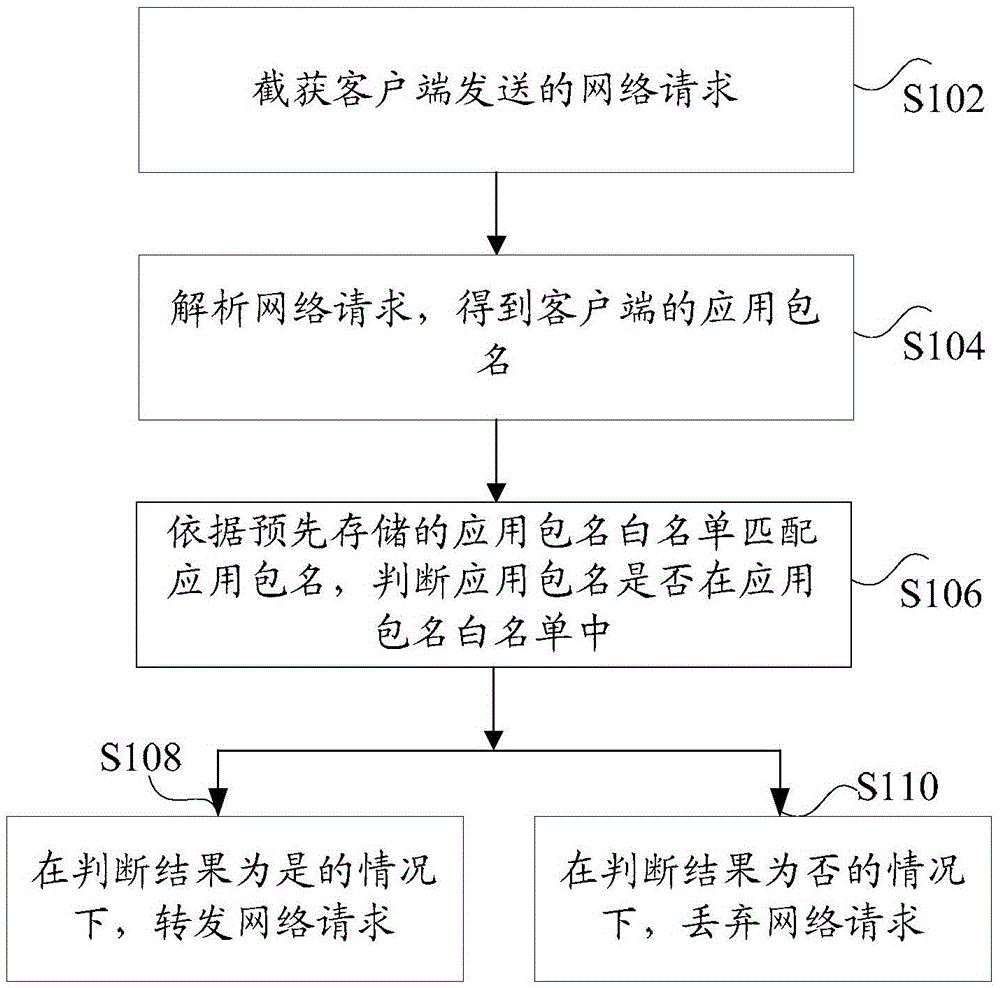
[0021] figure 1 is a schematic flowchart of a method for verifying request data according to an embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
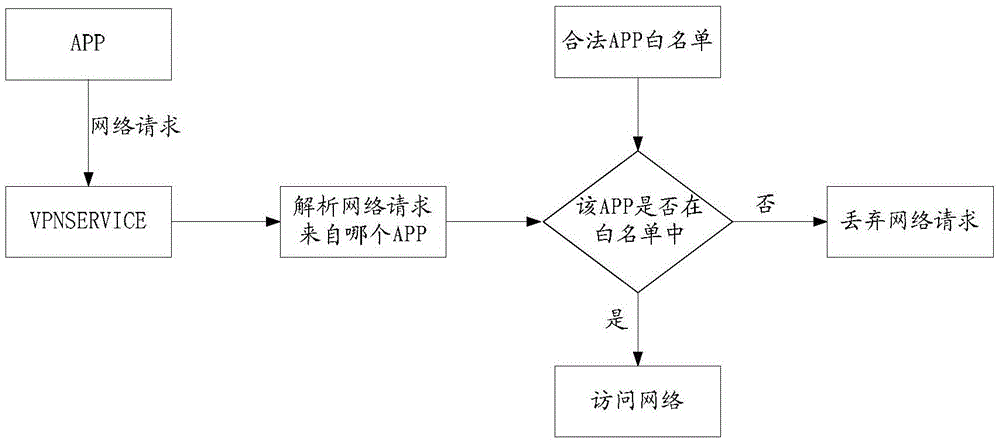
[0022] Step S102, intercepting the network request sent by the client;
[0023] Step S104, analyzing the network request to obtain the application package name of the client;
[0024] Step S106, matching the application package name according to the pre-stored application package name whitelist, a...
Embodiment 2
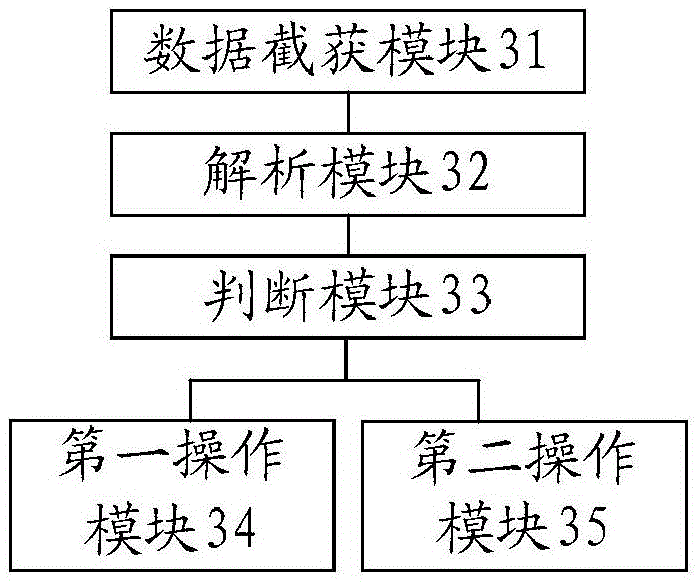
[0069] According to an embodiment of the present invention, a device embodiment of a device for verifying request data is provided, image 3 is a schematic structural diagram of a device for verifying request data according to an embodiment of the present invention, such as image 3 As shown, the device includes: a data interception module 31, an analysis module 32, a judgment module 33, a first operation module 34 and a second operation module 35, wherein,
[0070] Data interception module 31, is used for intercepting the network request that client sends;
[0071] Parsing module 32, is used for parsing network request, obtains the application package name of client;
[0072] Judging module 33, for matching the application package name according to the pre-stored application package name white list, and judging whether the application package name is in the application package name white list;
[0073] The first operation module 34 is configured to discard the network reque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com