P2P botnet detection method based on fractal and self-adaptation fusion
A detection method and adaptive technology, applied in the field of computer security, can solve the problems of low detection efficiency and complex detection process, and achieve the effect of reducing the hypothesis set
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
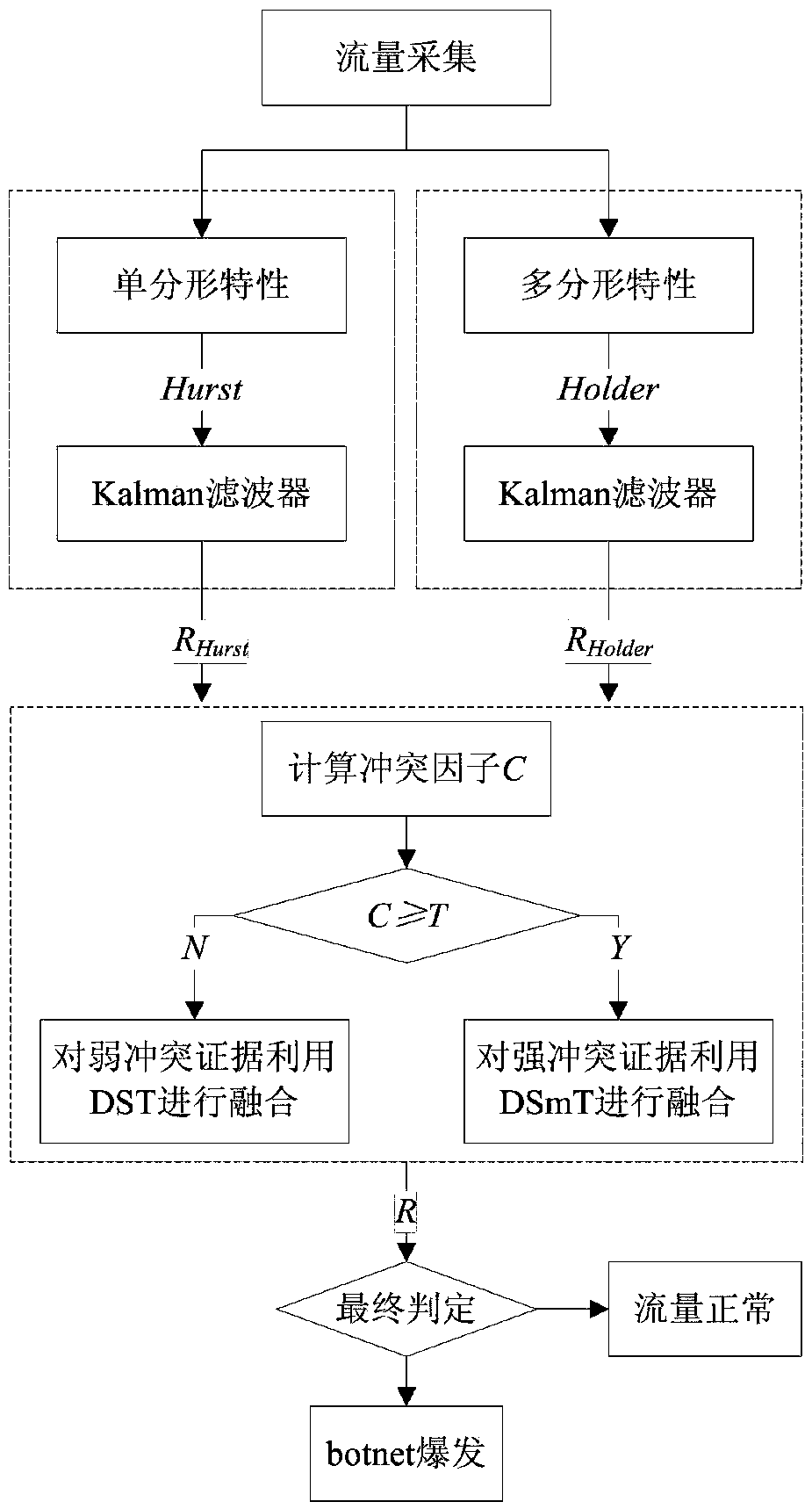
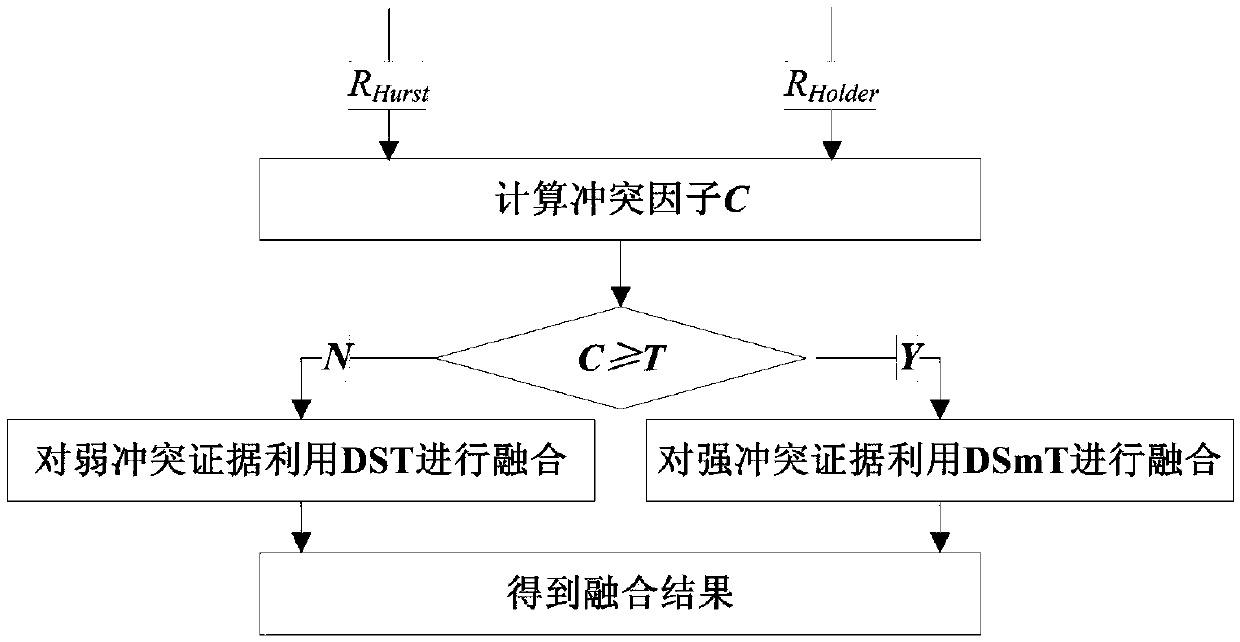
[0034] Specific implementation mode 1. Combination figure 1 with figure 2 Describe this embodiment, the P2Pbotnet detection method based on fractal and self-adaptive fusion, the specific implementation steps are:
[0035] Step 1: Network traffic data collection.
[0036] Use tools such as Wireshark to collect network traffic as the original input data of the detection method.
[0037] Step 2: Construct two network traffic detection sensors using fractal theory to detect whether the characteristics of network traffic at different time scales are abnormal.
[0038] 1) Use the monofractal characteristic detection sensor to detect whether there is anomaly in the self-similarity of network traffic on a large time scale: estimate the Hurst exponent, input it into the Kalman filter as a system measurement value, and establish a Kalman filter model to detect The abnormality of the network traffic self-similarity feature is obtained to obtain the detection result.
[0039] 2) Use ...
specific Embodiment approach 2
[0042] Specific embodiment two, combine figure 1 with figure 2 Describe this embodiment, this embodiment is the embodiment of the P2Pbotnet detection method based on fractal and adaptive fusion described in the specific embodiment one:
[0043] Step A, network traffic data collection, use tools such as Wireshark to collect network traffic, as the original input data of the detection method, calculate the network traffic in a fixed time window, and normalize it to obtain the traffic F k , assuming that the current is the kth time window;
[0044] Step B. Construct two network traffic detection sensors to detect whether the characteristics under different time scales are abnormal.
[0045] 1. Use monofractal characteristics to detect sensors to detect whether there is anomaly in the self-similarity of network traffic on a large time scale: use the rescaled range (R / S, RescaledRange) method to estimate the Hurst exponent in the current time window to obtain Hurst k , which is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com