Method and device of multiple authentications on the basis of AllJoyn
A multi-authentication and authentication method technology, applied in the field of the Internet of Things, can solve the problems that the AllJoyn authentication method is not reliable and flexible, restricts the development of AllJoyn scalability and compatibility, and achieves the effect of enhancing scalability and compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
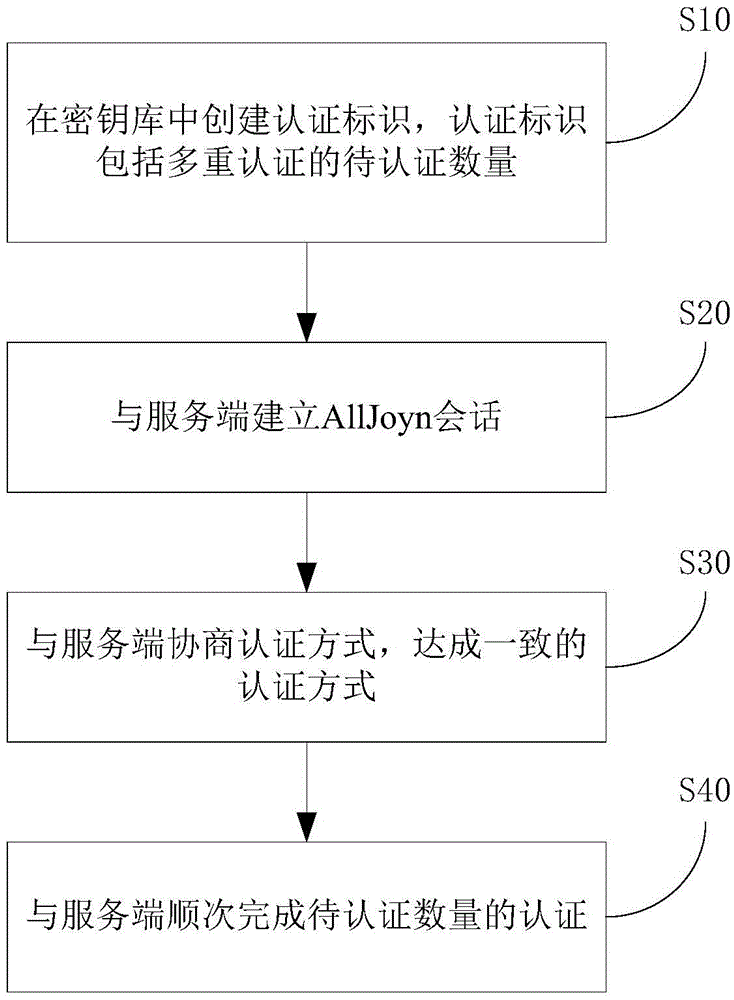
[0036] like figure 1 As shown, in the multi-authentication method based on AllJoyn in this embodiment, the process executed on the client side includes: Step S10: Create an authentication ID in the key store, and the authentication ID includes the number of multiple authentications to be authenticated. Step S20: Establish an AllJoyn session with the server. Step S30: Negotiate with the server on the authentication method to reach an agreed authentication method. Step S40: complete the authentication of the number to be authenticated with the server in sequence. .
[0037] In the multi-authentication method of this embodiment, only one bus attachment needs to be created, which saves the resources of the AllJoyn system, maintains the original pattern of the AllJoyn system, facilitates developers to deploy multi-authentication mechanisms, and enhances the scalability and compatibility of the AllJoyn system authentication methods.
[0038] Preferably, the authentication ID is n...
no. 2 example
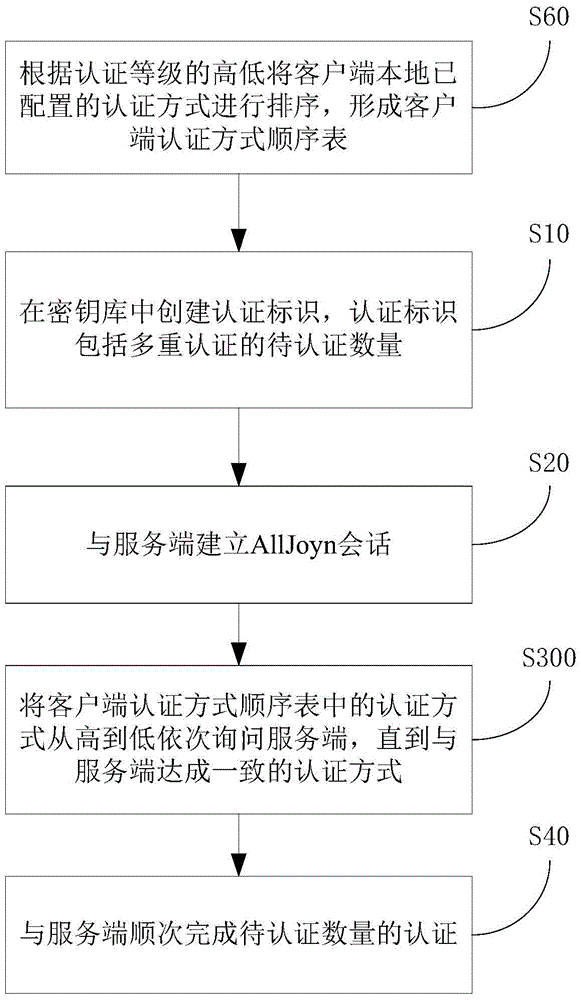
[0052] like image 3 As shown, in this embodiment, on the basis of the first embodiment, before step S30: negotiating the authentication method with the server and reaching an agreed authentication method, the multi-authentication method in this embodiment further includes: Step S60: according to the authentication level Sort the locally configured authentication methods of the client to form a sequence table of client authentication methods; correspondingly, in step S30: Negotiate with the server on the authentication method to reach an agreed authentication method, which specifically includes: Step S300: Set the client The authentication methods in the client authentication method order table are inquired from the server in turn from high to low, until the authentication method agreed with the server is reached.
[0053] On the basis of the second embodiment, preferably, step S300: inquire the authentication methods in the client authentication method sequence table from hig...
no. 3 example
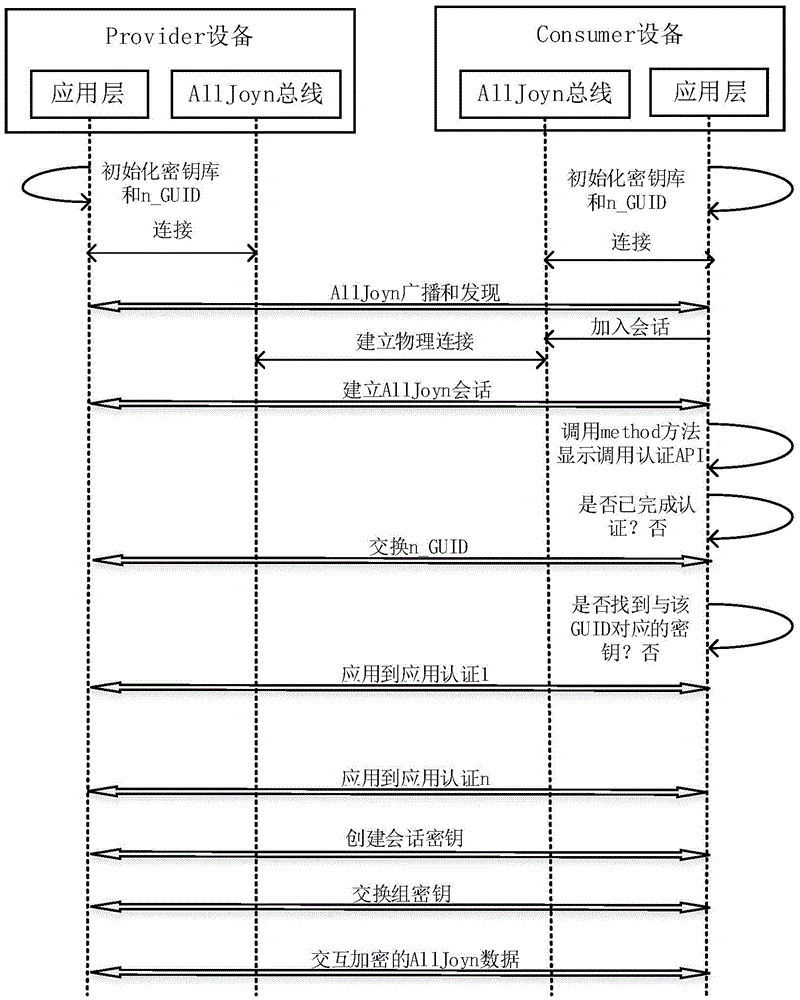
[0055] On the basis of the second embodiment, step S40: complete the authentication of the quantity to be authenticated sequentially with the server, specifically including: calling the AuthChallenge method, and sending the authentication parameter as the verification code of this authentication request for the server to receive After the parameters are authenticated, it is compared with the local verification code of the server; under the condition that the verification code of this authentication matches the local verification code of the server, the confirmation signal sent by the server is received to complete this Authentication, start the next authentication until the authentication of the quantity to be authenticated is completed.
[0056] Further, after receiving the confirmation signal sent by the server, complete this authentication, start the next authentication until the number of authentications to be authenticated is completed, specifically including: after receiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com