Card application access method and device
An access method and technology for an access device, applied in the field of card application access methods and devices, capable of solving problems such as failure of normal use of application services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0023] figure 1 It is a flow chart of the card application access method provided by the embodiment of the present invention. The execution subject of this embodiment is a mobile terminal, such as figure 1 As shown, the card application access method provided in this embodiment includes:
[0024] Step 101: Receive an access request from a first card application, where the access request from the first card application includes an AID (Application Identifier, AID for short) of the first card application.
[0025] Step 102, sending an access request of the first card application to the currently activated first profile in the embedded customer identity module E-SIM, so that the embedded customer identity module E-SIM generates a response result.
[0026] Wherein, the executor of this embodiment is a mobile terminal, and the first card application is a card application program Applet installed in an embedded customer identification module SIM card, that is, an E-SIM card. Confi...
Embodiment 2
[0035] This embodiment is a further supplement or explanation to the above embodiments, figure 2 It is a flowchart of a card application access method provided in another embodiment of the present invention. The card application access method includes:
[0036] Step 201: Receive an access request from a first card application, where the access request from the first card application includes an application identifier AID of the first card application.
[0037] Step 202, sending an access request of the first card application to the currently activated first profile in the embedded customer identity module E-SIM, so that the embedded customer identity module E-SIM generates a response result.
[0038] Wherein, step 201 and step 202 are respectively the same as step 101 and step 102 in the above embodiment, please refer to the explanation in embodiment 1 for details, and details will not be repeated in this embodiment.
[0039] Step 203, receiving the successful access result ...
Embodiment 3
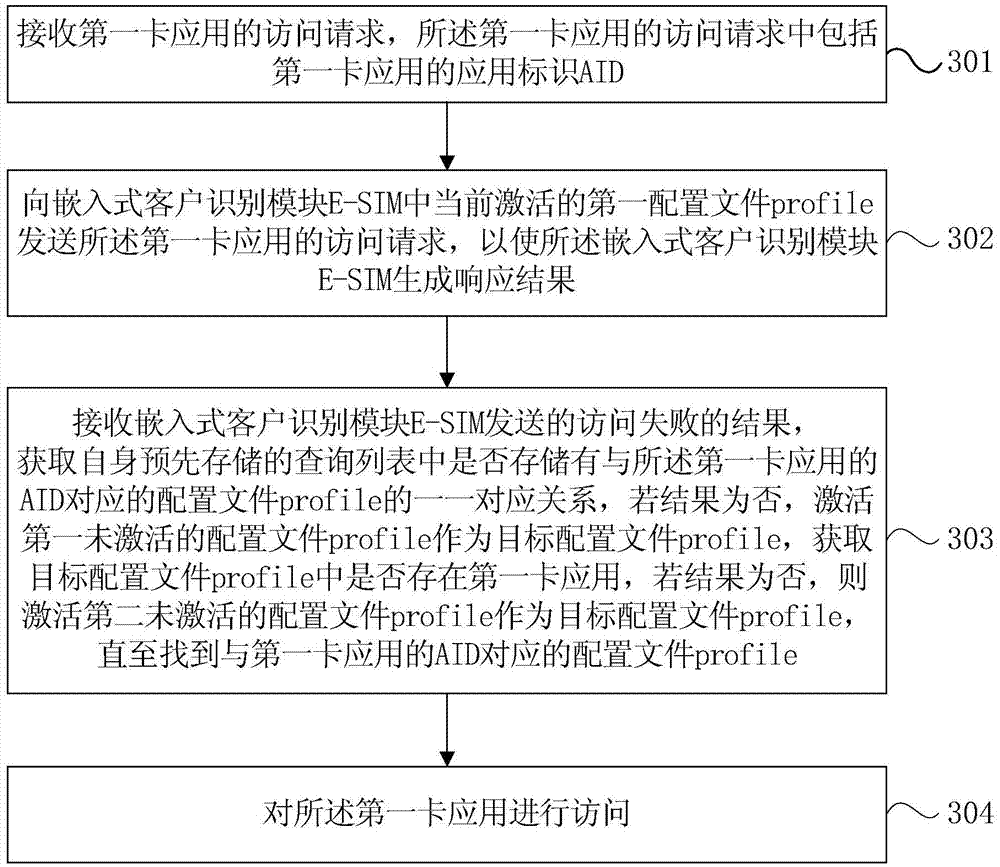
[0045] This embodiment is a further supplement or explanation to the above embodiments, image 3 It is a flowchart of a card application access method provided by another embodiment of the present invention, the card application access method includes:
[0046] Step 301: Receive an access request from a first card application, where the access request from the first card application includes an application identifier AID of the first card application.
[0047] Step 302, sending an access request of the first card application to the currently activated first profile in the embedded customer identity module E-SIM, so that the embedded customer identity module E-SIM generates a response result.
[0048] Wherein, step 301 and step 302 are respectively the same as step 101 and step 102 in the first embodiment, please refer to the first embodiment for details, and will not be repeated here.
[0049] Step 303, receiving the result of the access failure sent by the embedded customer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com