System and method for location reporting in an untrusted network environment
A technology for reporting, location information, used in the field of communications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] overview
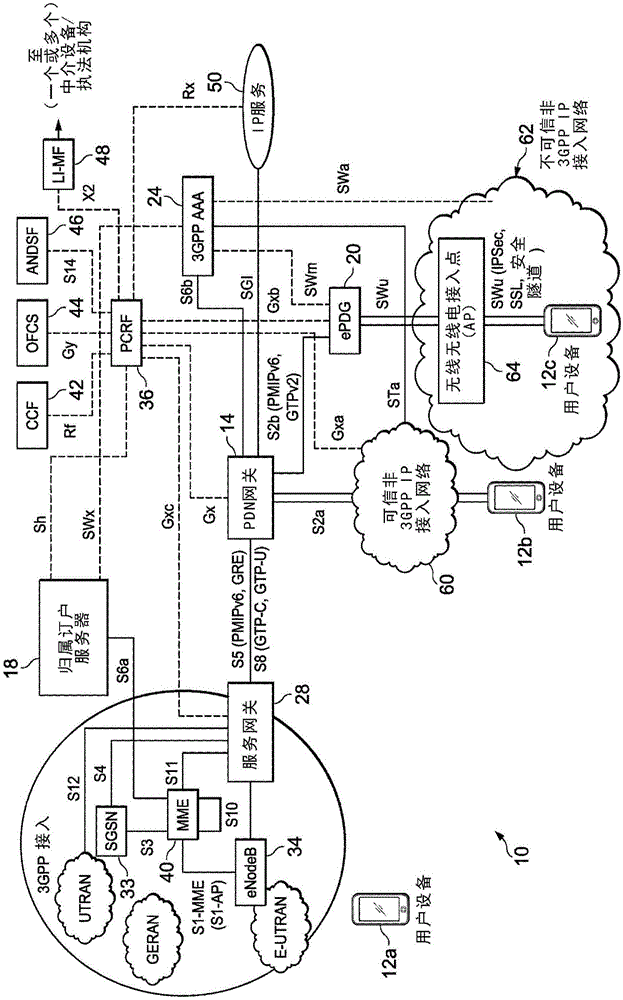
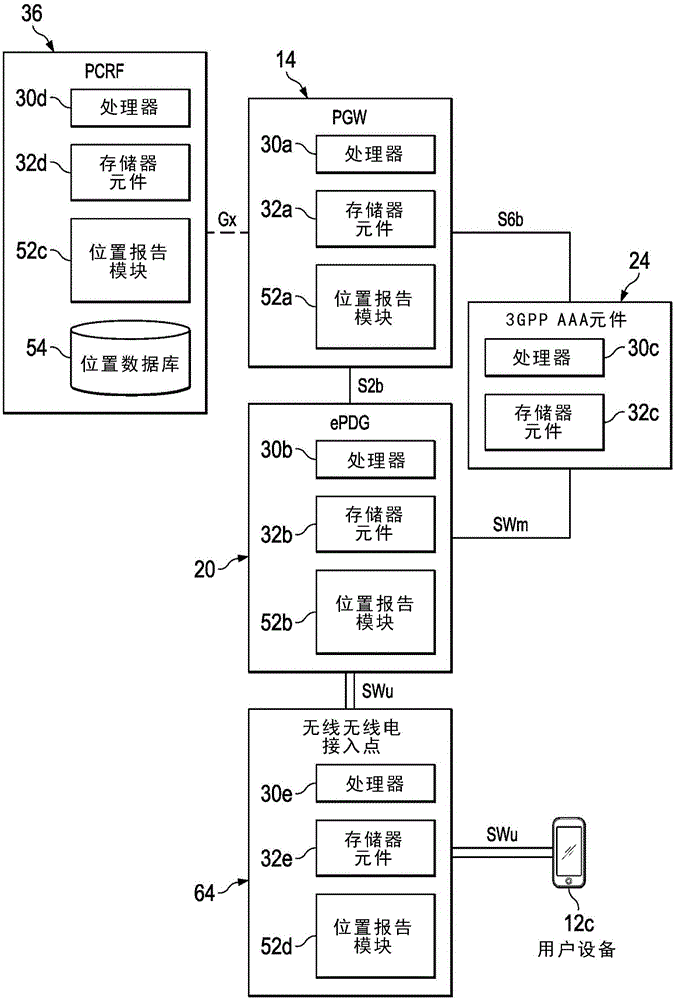
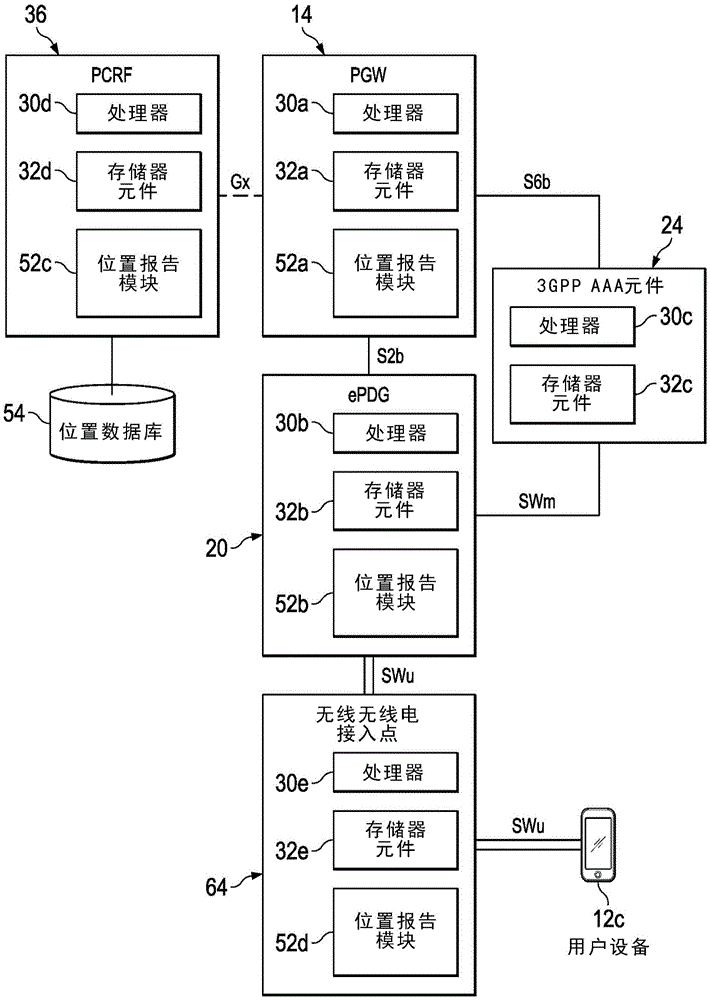
[0014] In an example embodiment, a method is provided, and the method may include: retrieving, by a user equipment (UE), an AP medium access control (MAC) address of an access point (AP) to which the UE is connected, wherein the The AP is in an untrusted Internet Protocol (IP) access network; using the Internet Key Exchange Version 2 (IKEv2) protocol to report the location information of the UE to the Evolved Packet Data Gateway (ePDG) through the SWu interface, where the location information at least partially includes: The location of the UE in Global Positioning System (GPS) coordinates, the service set identifier (SSID) of the untrusted IP access network, the retrieved APMAC address, and cell identification (ID) information for the UE; and using the UE The location information of the UE populates a location database, wherein the location database at least partially includes location information of other UEs in the untrusted IP access network.
[0015] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com