Permission configuration method and system used for photovoltaic monitoring system
A monitoring system and authority configuration technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] Embodiment 1. A permission configuration method for a photovoltaic monitoring system.
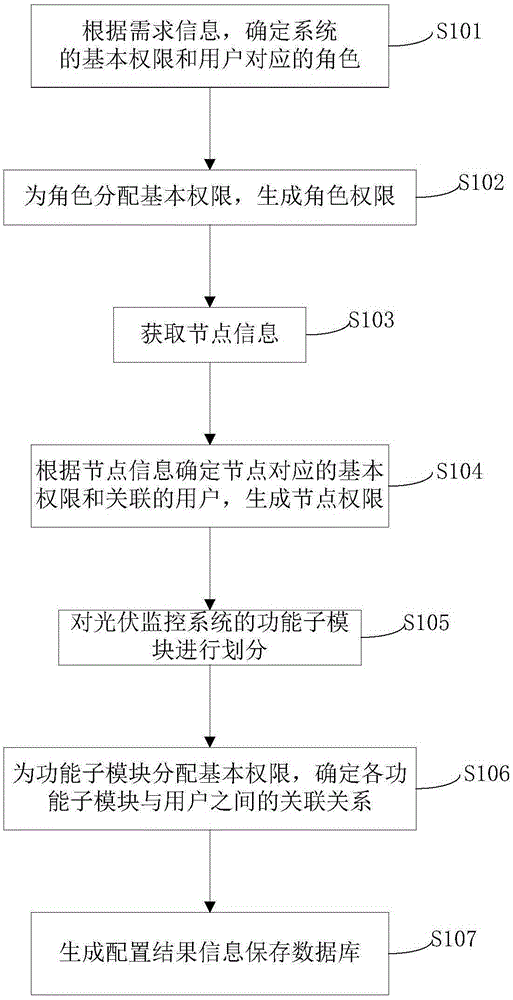
[0065] figure 1 It is a flow chart diagram of the authority configuration method for the photovoltaic monitoring system in Embodiment 1 of the present invention. The embodiment of the present invention will combine figure 1 Be specific.
[0066] Such as figure 1 As shown, the embodiment of the present invention provides a permission configuration method for a photovoltaic monitoring system, including the following steps:
[0067] Step S101: Determine the basic authority of the system and the corresponding role of the user according to the requirement information;
[0068] It should be noted that the basic authority mentioned in the context of the present invention refers to the operation authority of the photovoltaic monitoring system without attributes, which has not been assigned to a specific user; the role authority is assigned based on the role corresponding to the user Perm...
Embodiment 2
[0123] Embodiment 2. A permission configuration method for a photovoltaic monitoring system.
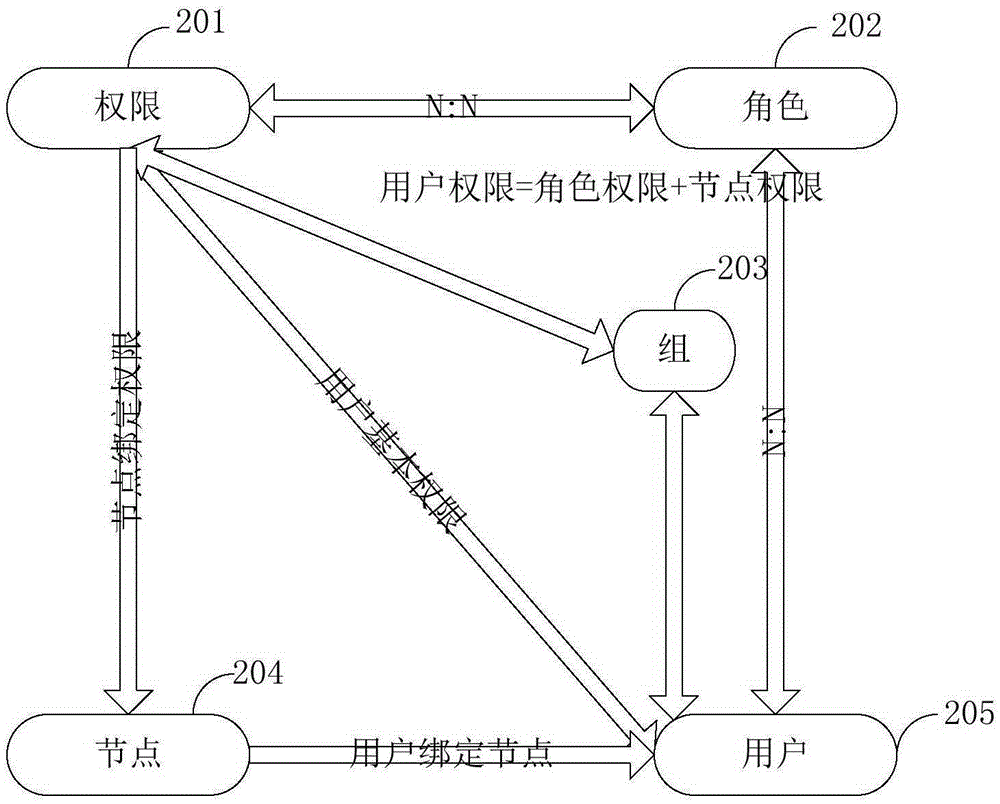
[0124] figure 2 It is a flow chart of the permission configuration method for the photovoltaic monitoring system in the second embodiment of the present invention, and the embodiment of the present invention will combine figure 2 Be specific.
[0125] Such as figure 2 As shown, the embodiment of the present invention provides a permission configuration method for a photovoltaic monitoring system, including: permission 201, role 202, group 203, node 204 and user 205, between the role 202 and the permission 201 is A many-to-many relationship, the relationship between the role 202 and the user 205 is a many-to-many relationship, the node 204 is bound to the authority 201, the user 205 is bound to the node 204, and the user authority includes all The union of the node permissions and role permissions described above.
[0126] Preferably in the embodiment of the present invention, ...
Embodiment 3
[0148] Embodiment 3, a procedure for using a permission configuration method for a photovoltaic monitoring system.
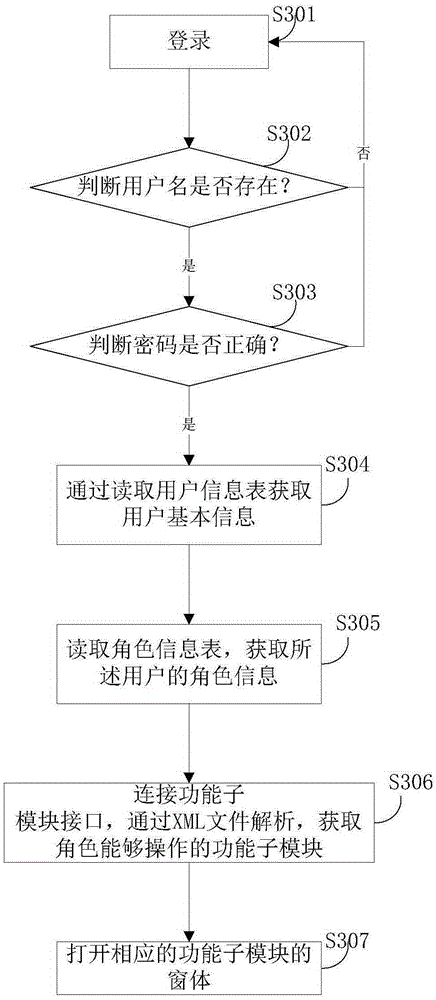
[0149] image 3 It is a flow chart of the authority configuration method for the photovoltaic monitoring system in the third embodiment of the present invention, and the embodiment of the present invention will combine image 3 Be specific.
[0150] Such as image 3 As shown, the embodiment of the present invention provides a procedure for using a permission configuration method for a photovoltaic monitoring system, including the following steps:
[0151] Step S301: login;
[0152] Step S302: Read the user name in the user information table, and judge whether the user exists according to the user name? If the user name exists, then enter the next step; otherwise, jump back to step S301;
[0153] Step S303: Read the password in the user information table, and determine whether the password is correct? If the password is correct, then enter the next step; ot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com