Dual authentication method, system and device for SSH safe login
A two-factor authentication and secure login technology, applied in the field of information security, can solve the problems of inability to guarantee security, leakage of users' passwords, and difficulty in distinguishing the authenticity of the server from the server, so as to facilitate remote login authentication, prevent identity theft, and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
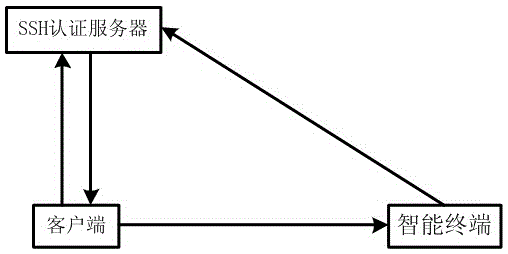
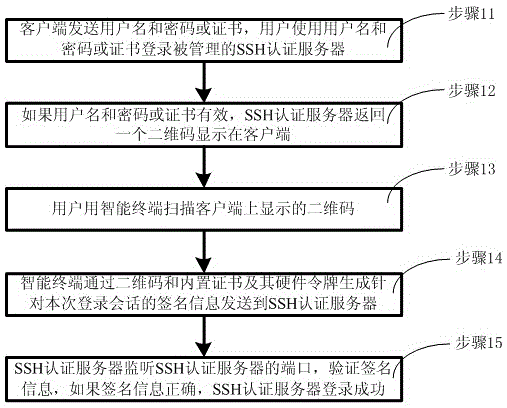
[0058] Example 1, such as figure 1 As shown, the double authentication device for SSH secure login described in the first embodiment of the present invention includes an SSH authentication server, a client, and an intelligent terminal.
[0059] The client is used to send the user name and password or certificate, and display the QR code returned by the SSH authentication server.
[0060] The SSH authentication server performs the first identity authentication on the user name and password or the certificate entered by the user, and if the authentication is passed, generates the QR code required for the second authentication on the user.
[0061] The smart terminal has a built-in encryption key, which is used to scan the QR code required for authentication when authentication is required, encrypt it with the encryption key inside the smart terminal, and return the encrypted QR code to the SSH authentication server.
[0062] like figure 2 As shown, the dual authentication met...
Embodiment 2
[0074] Example 2, such as Figure 4 As shown, a double authentication device for SSH secure login according to the second embodiment of the present invention includes an SSH authentication server, a client, an intelligent terminal and a two-dimensional code hardware device.
[0075] The client is used to send the user name and password or certificate, and display the QR code returned by the SSH authentication server.
[0076] The SSH authentication server performs the first identity authentication on the user name and password or the certificate entered by the user, and if the authentication is passed, generates the QR code required for the second authentication on the user.
[0077] The smart terminal has a built-in encryption key, which is used to scan the QR code required for authentication when authentication is required, encrypt it with the encryption key inside the smart terminal, and return the encrypted QR code to the SSH authentication server.
[0078] The two-dimens...
Embodiment 3
[0093] Example 3, such as Figure 7 As shown, a double authentication device for SSH secure login according to the third embodiment of the present invention includes an SSH authentication server, a client, an intelligent terminal, and a two-dimensional code authentication server.
[0094] The client is used to send the user name and password or certificate, and display the QR code returned by the SSH authentication server.
[0095] The SSH authentication server performs the first identity authentication on the user name and password or the certificate entered by the user, and if the authentication is passed, generates the QR code required for the second authentication on the user.
[0096] The smart terminal has a built-in encryption key, which is used to scan the QR code required for authentication when authentication is required, encrypt it with the encryption key inside the smart terminal, and return the encrypted QR code to the SSH authentication server.
[0097] The two-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com