Method of generating secret key possessing service life and system thereof
A key and key store technology, applied in the field of encryption, can solve the problems of high anti-tampering requirements and high hardware costs, and achieve the effect of improving reliability and security, and ensuring legitimate interests and legitimate rights and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings. However, those skilled in the art know that the present invention is not limited to the drawings and the following embodiments.
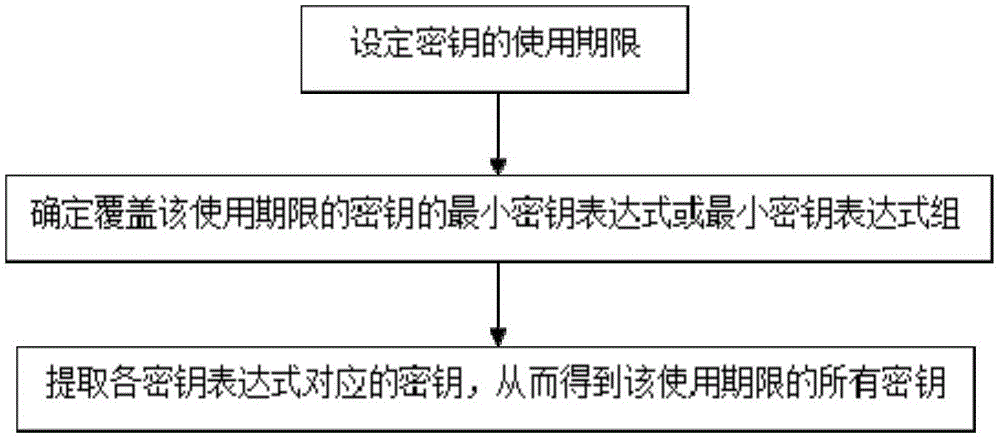
[0021] Such as figure 1 As shown, the method for generating a key with an expiration date proposed by the present invention comprises the following steps:
[0022] S1: Set the usage period of the key;
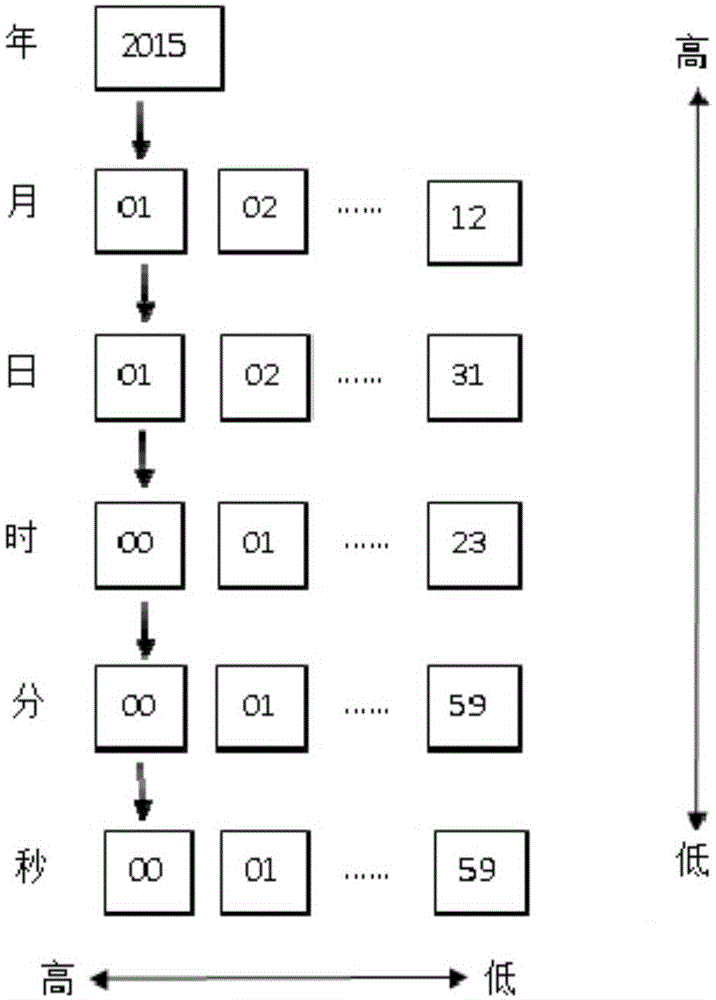
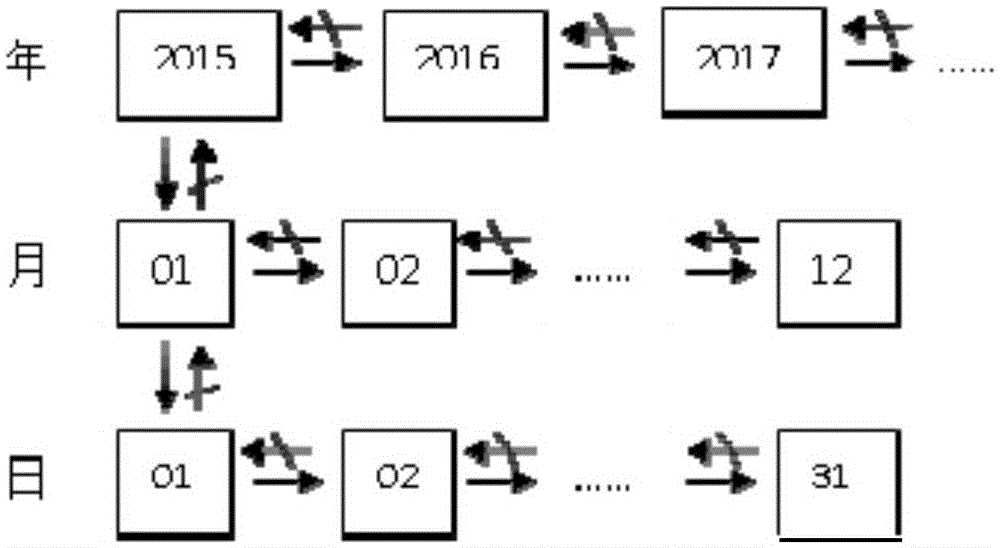
[0023] S2: According to the generation principle of the key, determine the minimum key expression or the minimum key expression group of the key covering the lifetime. Indicates the start time and end time of the key usage period in the form of year, month, day, hour, and second.
[0024] 1. The key generation principle is as follows:
[0025] The level of time is defined according to the orde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com