Group privacy matching method based on permutation matrix
A permutation matrix and privacy technology, applied in the field of network security, can solve problems such as no effective solutions, achieve the effects of reducing time complexity, improving feasibility, and solving single-point damage attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
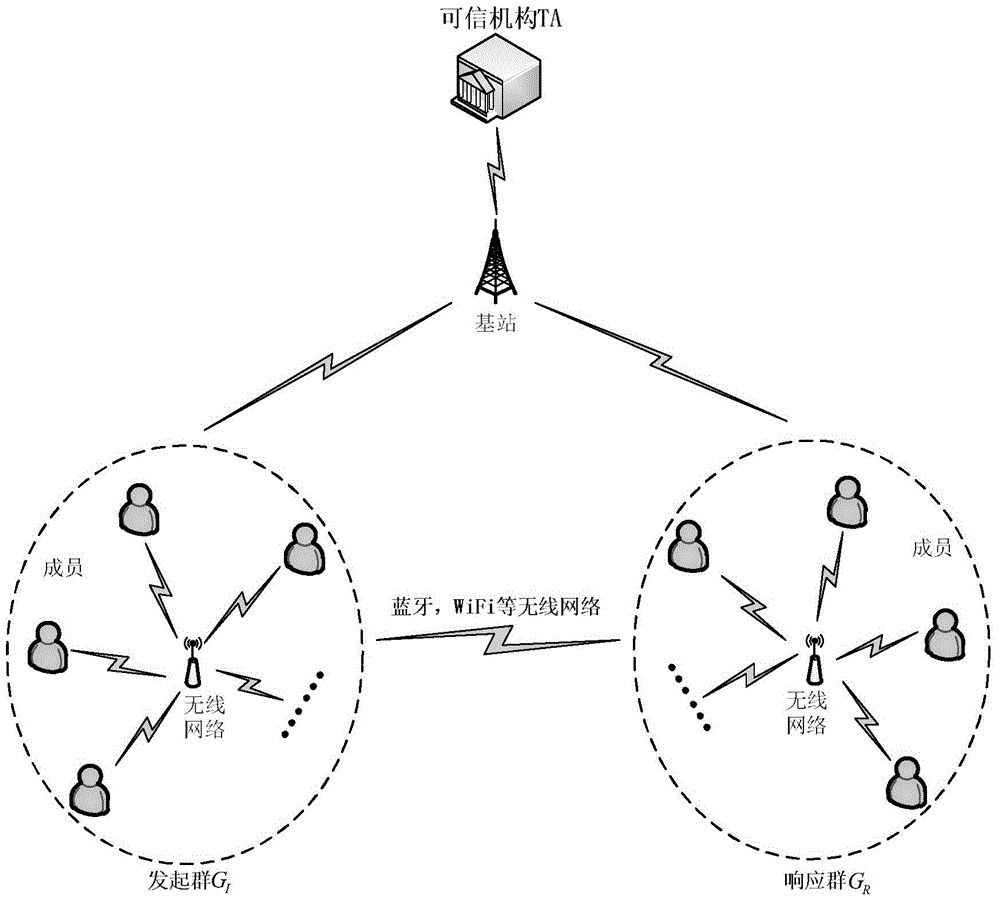
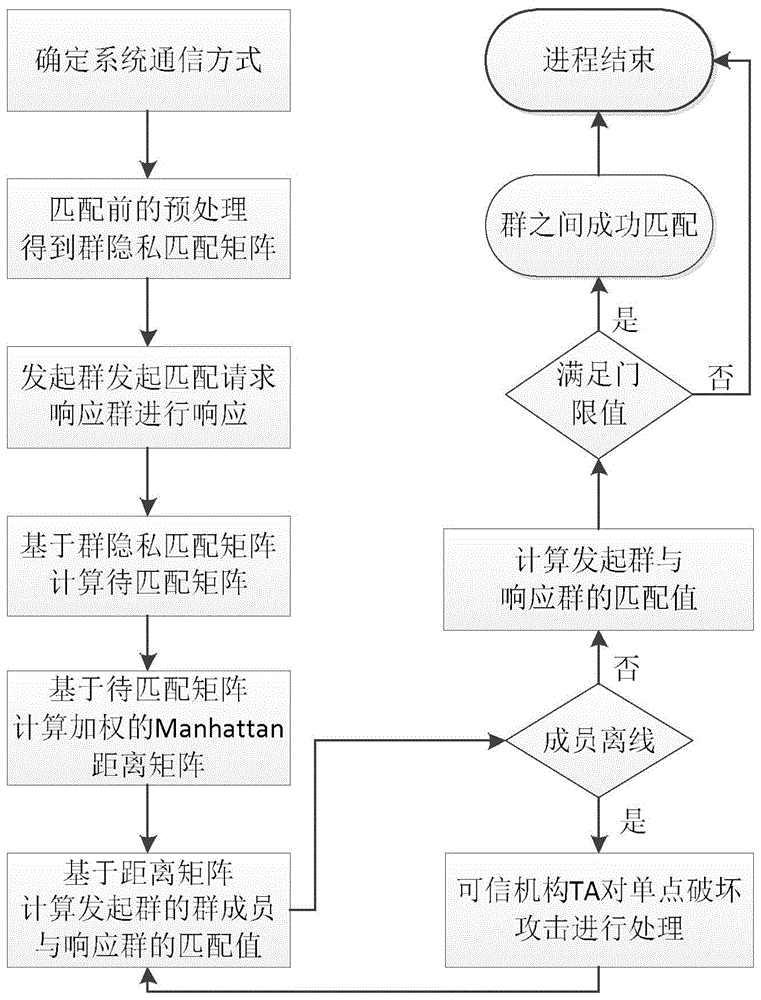
[0041] The core idea of the present invention is to use the permutation function based on the permutation matrix to realize the confusion of the weights of the private attribute keywords of the group members, so as to effectively protect the privacy of the group members; The degree of matching between groups; the introduction of a trusted organization TA can effectively manage the permutation function of group members and the corresponding inverse permutation function, so as to solve the problem of single-point destruction attacks in the matching process, and ensure the relationship between groups in the system. For efficient and secure matching.
[0042] refer to figure 1 , the communication system used in the present invention includes: a trusted organization TA, an initiating group G I , the response group G R : Initiating group G I with the response group G R Communication between members and other members in the same user group is carried out through wireless networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com