RFID-based efficient tracking and tracing method with privacy protection feature
A privacy protection and characteristic technology, which can be used in collaborative devices, businesses, instruments, etc., and can solve problems such as low efficiency and unfavorable privacy protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
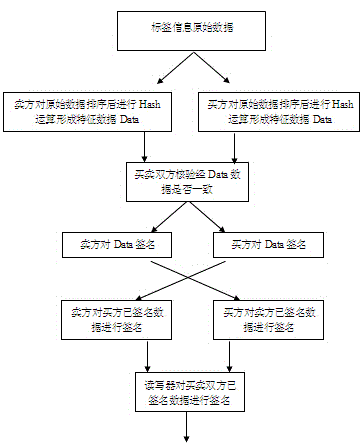
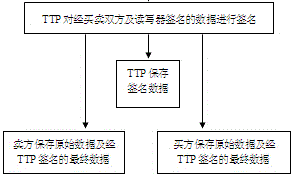
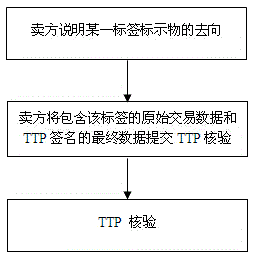
[0059] This method first establishes a trusted third-party TTP, and the user registers in the TTP, and obtains a trusted reader-writer and a portable security device Dev approved by the TTP to store the digital certificate issued by the TTP. During the transaction, the two parties of the transaction, namely the buyer and the seller, respectively read the information of the labels and the commodities corresponding to the labels. Sign the hash value of the sorting results and save the required data respectively; finally, in the case where the item needs to be tracked (traceability), the seller (buyer) explains the whereabouts of the item by proving the required data to TTP (source ),Specific steps are as follows:
[0060] a. Registration:
[0061] Establish a trusted third-party TTP, the user registers in the TTP, and obtains a portable security device Dev approved by the TTP, such as an IC card or USB Key, and the Dev stores the digital certificate issued by the TTP. The safe ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com