Hidden file management system based on steganography
A technology for concealing files and management systems, which is applied in the fields of electrical digital data processing, special data processing applications, internal/peripheral computer component protection, etc., to achieve the effect of convenient operation and strong portability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
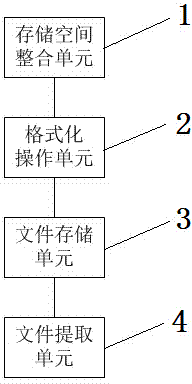
[0032] like figure 1 As shown, a hidden file management system based on steganography includes a storage space integration unit 1, a formatting operation unit 2, a file storage unit 3 and a file extraction unit 4;
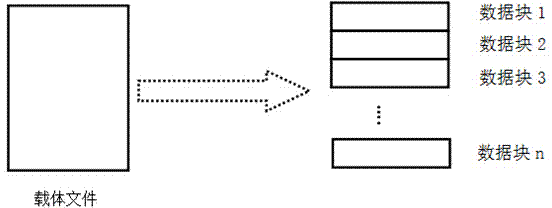
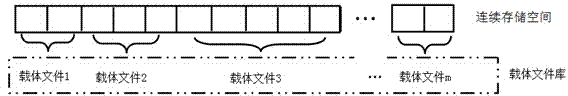
[0033] The storage space integration unit 1 is used to abstract the storage space of the carrier file library into a continuous storage space composed of several data blocks, and use the absolute path of each carrier file in the carrier file library and each data block in its corresponding The offset position in the carrier file is a variable, and the connection relationship between the data block and the carrier file is established;
[0034] The formatting operation unit 2 is used to divide the continuous storage space into a reserved area, a block state area and a data area. The block state area is composed of several block...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com