Malicious URL detection method and implement system thereof
A detection method and malicious technology, applied in transmission systems, electrical components, etc., can solve problems such as threats to the security and property safety of user terminal systems, inability to completely avoid URL flexibility malicious intrusion, etc., to resist the harm of malicious URLs and improve accuracy , the effect of improving safety performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
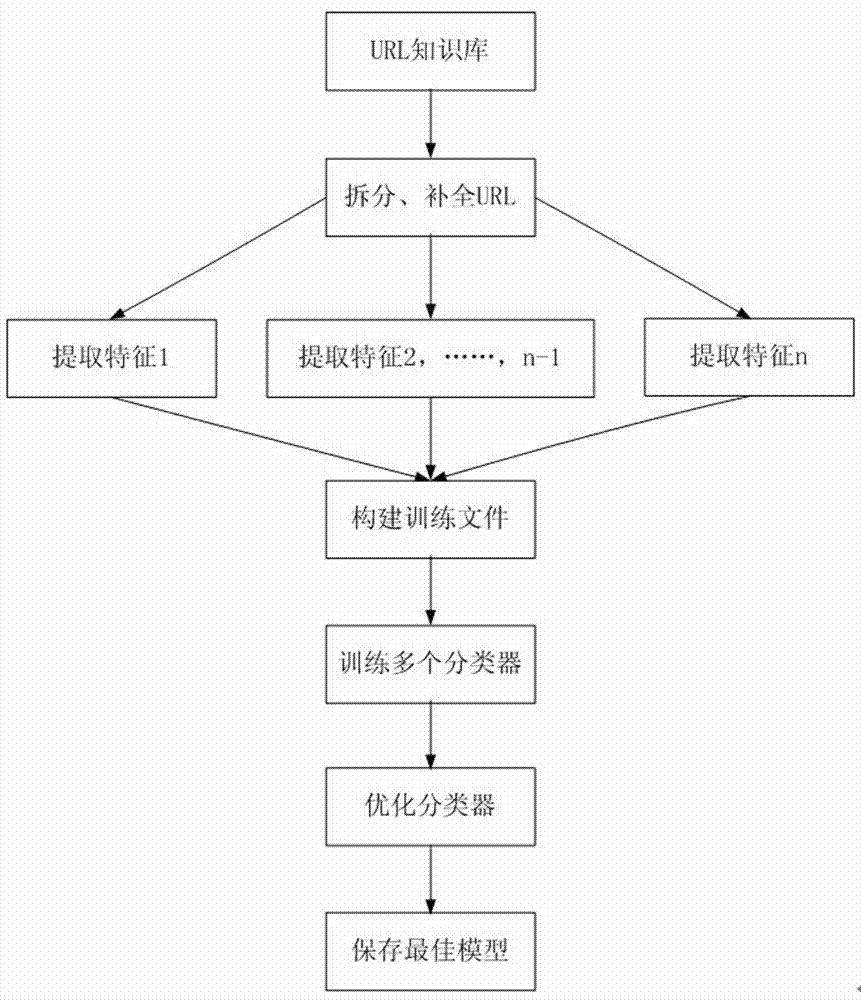
Method used
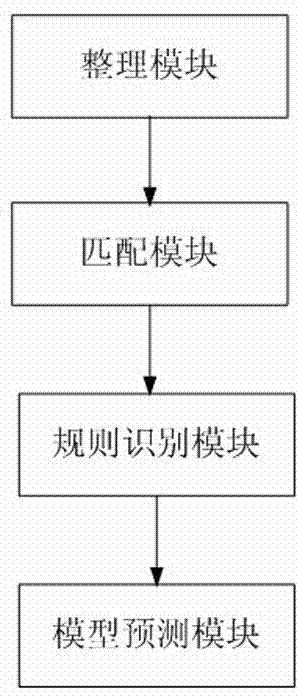
Image
Examples
Embodiment 1
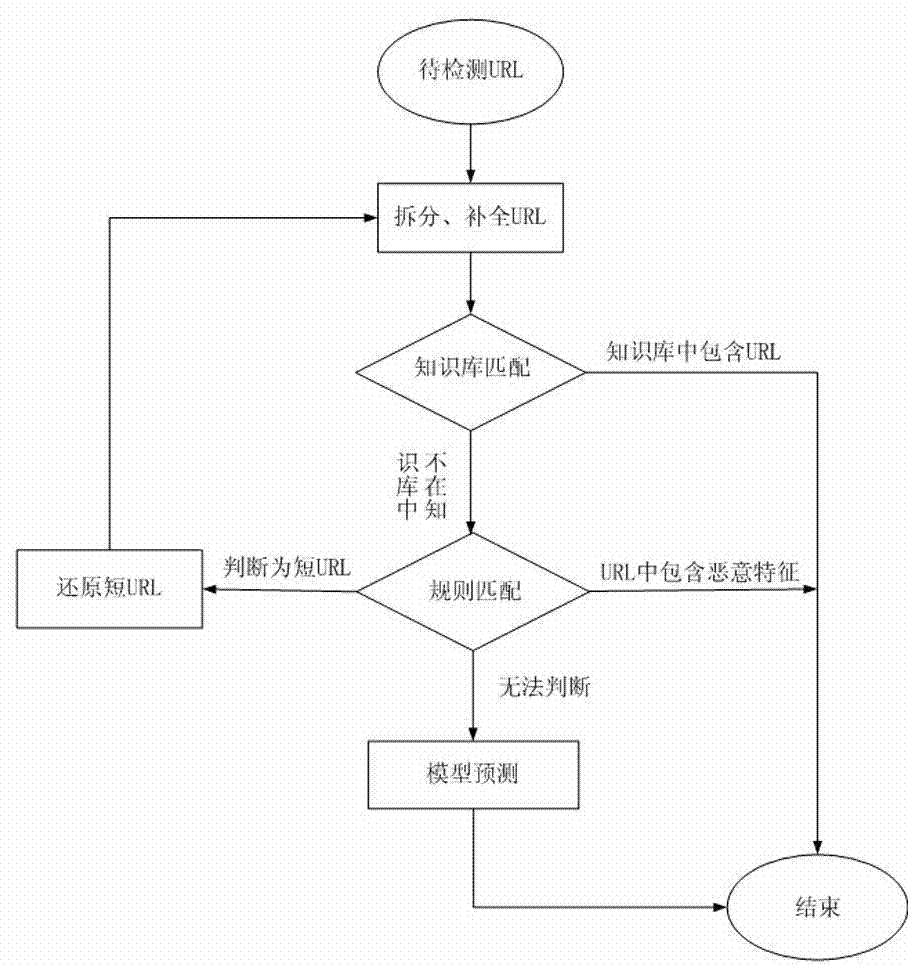
[0028] Embodiment one, If the url to be detected: "abcdefg", the specific judgment steps are as follows:
[0029] (1) Firstly, according to the implementation step S1, complete the modified url to "http: / / abcdefg";
[0030] (2) Then according to the implementation step S2, it is judged that the url is not in the URL knowledge base;
[0031] (3) Go to step S3 again, filter out the malicious features in the url through the rules (execute S31): the url scheme description part only contains English characters, so it is finally judged that the url to be detected is malicious. The same applies to the case where the description part of the rul scheme only contains numbers. Embodiment 2. If the url to be detected is: "http: / / www.dwz.cn / t05ZQ", the specific judgment steps are as follows:
[0032] (1) First, according to the implementation step S1, the url after completion and modification is still "http: / / www.dwz.cn / t05ZQ";
[0033] (2) Then according to the impleme...
Embodiment 3
[0037] Embodiment 3, if the url to be detected: "http: / / shop.ldangdang.com / 14416", the specific judgment steps are as follows:
[0038] (1) Firstly, according to the implementation step S1, the modified url is still "http: / / shop.ldangdang.com / 14416";
[0039] (2) Then according to the implementation step S2, it is judged that the url is not in the URL knowledge base;
[0040] (3) Go to step s3 again, and judge through the rules that not only does not contain malicious URL features, but also does not contain short URL features;
[0041] (4) Finally enter step S33, use the model prediction module to make predictions, and the prediction result is malicious, so it is finally judged that the url to be detected is malicious. The model prediction module used therein has a classifier trained offline and continuously updated, and has a processing device for detecting maliciousness of the predicted file based on the classifier.
[0042] In summary, it can be seen that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com