A method and system for access authentication of an internet of things gateway
An Internet of Things gateway and access authentication technology, applied in the field of Internet of Things gateway access authentication methods and systems, can solve problems such as complex computing and storage capabilities, and reduced security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
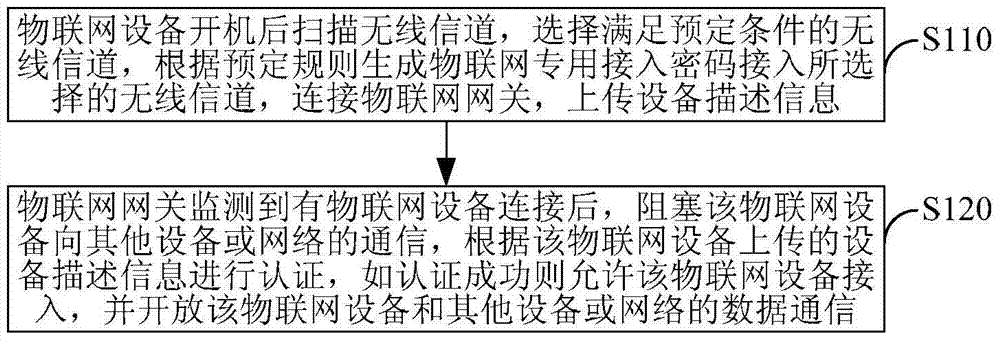
[0046] Embodiment 1. A method for access authentication of an Internet of Things gateway, such as figure 1 shown, including:
[0047] S110. After the Internet of Things device is turned on, scan the wireless channel of the corresponding access method according to its own wireless access method, select a wireless channel that meets the predetermined conditions, generate an Internet of Things special access password according to the predetermined rule to access the selected wireless channel, and connect IoT gateway, upload device description information;
[0048] S120. After the IoT gateway detects that an IoT device is connected, it blocks the communication of the IoT device to other devices or networks, performs authentication according to the device description information uploaded by the IoT device, and allows the IoT device if the authentication is successful. Device access, and open data communication between the IoT device and other devices or networks.
[0049]This emb...
Embodiment 2
[0113] Embodiment 2, an Internet of Things gateway access authentication system, comprising:
[0114] The access module is set in the IoT device, and is used to scan the wireless channel of the corresponding access mode according to its own wireless access mode after the IoT device is turned on, select the wireless channel that meets the predetermined conditions, and generate the dedicated network of the Internet of Things according to the predetermined rules. Access the password to access the selected wireless channel, connect to the IoT gateway, and upload device description information;
[0115] The authentication module is set in the Internet of Things gateway, and is used to block the communication of the Internet of Things device to other devices or networks after detecting that an Internet of Things device is connected to the Internet of Things gateway. According to the device description uploaded by the Internet of Things device If the authentication is successful, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com